In 2016 alone over one billion records containing personal information including email addresses were put up for sale or made public after a rash of leaked data from numerous breaches.
Researchers 'Beknow' and Troy Hunt recently gained access to the data of one such repository (thanks to Beknow): the spam bot "Onliner" best known for spreading the Ursnif banking Trojan, and discovered a massive trove of hundreds of millions of records including email addresses, email and password combinations (some in cleartext), and SMTP credentials and configuration files.
80 million credentials were found among the data, although determining provenance is near impossible. However, about two million were determined to originate from a Facebook phishing campaign.
“...mind-boggling amount of data.”
“Just for a sense of scale, that’s almost one address for every single man, woman and child in all of Europe,”
- One file alone contained 1.2 million email addresses and cleartext passwords, many of which are likely from the LinkedIn breach which leaked passwords as SHA1 hashes with no salt
- Another file contained 4.2 million email addresses and passwords, according to Hunt each one were found in a list from the Exploit[.]In underground forum
- Around 2 million came from a Facebook phishing campaign
- Also found in separate files, thousands of records containing email addresses, passwords and SMTP server and port designations
Hunt said that the particular Onliner server, hosted in the Netherlands, was still up and running and law enforcement had been notified.
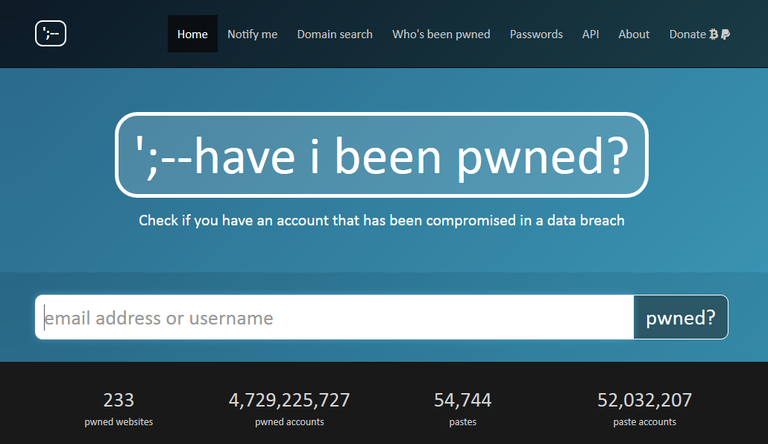
"have i been pwned?" is a service you can use to check if an account has been compromised in a data breach. Using the service is very straight forward, simply enter the email address or username to check & hit "pwned?", but be aware that:
- Sensitive breaches are not publicly searchable
- Unverified breaches may be sourced from elsewhere
- Spam Lists are used for spam marketing
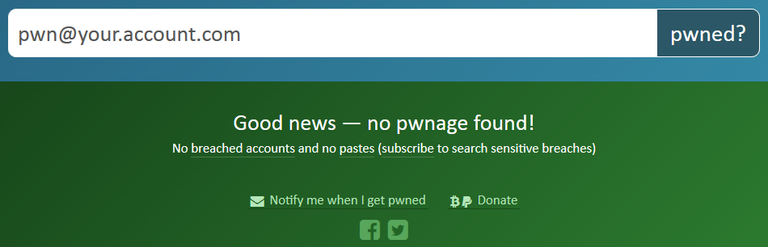
Green is good, in at least as the account isn't present in known breach data, see Advice* below.

Red means stop is not so good, jump to Advice* section now.
The service began after its creator Troy Hunt (a Microsoft Regional Director & international web security speaker/author) continued to find the same accounts in repeated post-breach analysis, often with the same passwords, putting the victims at risk of further accounts being compromised.
All build and running costs are funded directly from Troy's own pocket, but Paypal or Bitcoin (121CEyDDEewZfp7mpFLd6WvfD9fcyWpwQe) donations are very gratefully accepted.
*Advice
"...there are known knowns; there are things we know we know. We also know there are known unknowns; that is to say we know there are some things we do not know. But there are also unknown unknowns – the ones we don't know we don't know. And if one looks throughout the history of our country and other free countries, it is the latter category that tend to be the difficult ones.
- Donald Rumsfield, former US Secretary of Department of Defense
A word to the wise: if you find a match for your user or account name, change your password for the indicated service(s).
A word to the unwise: if you use the same password in multiple locations, or, gods help you, everywhere, then you should change the compromised password everywhere you've use it, preferably to a unique one at each site/service, preferably even if it hasn't been compromised.
There's also a Notify Me service that can send alerts when if HIBP find your email address again in future data breach dumps (you changed to a unique, complex password, right?).
If you're daunted by the prospect of managing a number of unique and complex passwords then check out my series of articles on this very subject:
🔐 How vulnerable are you: secure, ubiquitous, ease of access
🔐 How vulnerable are you: managing complexity
I've been working towards an article on more secure computer practices and behaviour, but @profit-generator has just beaten me to the punch with just such an article, I suggest you read it.
I'll probably still write an article on the topic anyway. P-G will likely write more too, as will @an0nkn0wledge and @ausbitbank and etc et al. Over time you may get a bit sick of the continued best-practice digital security advice, but we won't quit, we'll just STEEM ON!
If you need any further encouragement just check the list and totals of compromised sites/accounts below.
The HIBP pwage list is extensive, it includes site/services, details the number and types of accounts compromised, and provides dates, links and other details where available. Among the data security breaches listed are:
- 4,789,599 Bitcoin Security Forum Gmail Dump email addresses, passwords in September 2014
- 501,407 Bitcoin Talk dates of birth, email addresses, genders, IP addresses, passwords, security questions and answers, usernames, website activity in May 2015
- 568,340 BTC-E account balances, email addresses, IP addresses, passwords, usernames, website activity in October 2014
As at writing the current Top 10 breaches are:
- Onliner Spambot - 711,477,622 Onliner Spambot accounts
- Exploit.In - 593,427,119 Exploit.In accounts
- Anti Public Combo List - 457,962,538 Anti Public Combo List accounts
- River City Media Spam List - 393,430,309 River City Media Spam List accounts
- MySpace - 359,420,698 MySpace accounts
- NetEase - 234,842,089 NetEase accounts
- LinkedIn - 164,611,595 LinkedIn accounts
- Adobe - 152,445,165 Adobe accounts
- Badoo - 112,005,531 Badoo accounts
- B2B USA Businesses - 105,059,554 B2B USA Businesses accounts
^vote, resteem, and comment below. Considerable effort has gone into researching, testing, and formatting for this article.
Congratulations! This post has been upvoted from the communal account, @minnowsupport, by neuromancer from the Minnow Support Project. It's a witness project run by aggroed, ausbitbank, teamsteem, theprophet0, someguy123, neoxian, followbtcnews/crimsonclad, and netuoso. The goal is to help Steemit grow by supporting Minnows and creating a social network. Please find us in the Peace, Abundance, and Liberty Network (PALnet) Discord Channel. It's a completely public and open space to all members of the Steemit community who voluntarily choose to be there.
This post has received a 1.04 % upvote from @drotto thanks to: @banjo.
Congratulations @neuromancer! You have completed some achievement on Steemit and have been rewarded with new badge(s) :
Click on any badge to view your own Board of Honor on SteemitBoard.
For more information about SteemitBoard, click here
If you no longer want to receive notifications, reply to this comment with the word
STOPThanks for sharing this vital information here....we so grateful.
You're most welcome, I'm glad you found it informative, feel free to resteem the article if you think it will benefit others.
HIBP is a very useful tool to check after the announcement of a major data breach, of which there have been many in the last few years.
Thank you for this post, I will resteem just in case it can help someone else. Came through #theunmentionables in Discord :)
Thank you moonray, it's a very useful tool, particularly because email addresses can be subscribed to a notification list for alert emails if it is found among future breach data.
#theunmentionables is a great group, very active, lots of good steemians and material there.
If you'd like to see more material like this consider voting for my selection comment in the MAP "Six of the Best" post :)