Encryption has been used for thousands of years starting from roman times, with extremely simple methods such as the Scytale to conceal messages between politicians, to modern times with the movement of data between servers and clients in seconds all while using sophisticated algorithms to keep data safe.
Scytale
During Greek and Roman times, a device called a Scytale allowed for simple transposition (simply put it shifts text around in a certain pattern, usually in a bijection function then to decrypt, one would use a inverse function). The device used paper slips that rotated on a scroll to move plaintext around for the transposition. The strips of paper unravel to show a message to the recipient.

Caesar Cypher
Julius Caesar used a cypher that also involved shifting letters back and forth a number of spaces. Quite a simple way to make messages hidden.
Example:
Plain: ABCDEFGHIJKLMNOPQRSTUVWXYZ
Cipher: DEFGHIJKLMNOPQRSTUVWXYZABC
Polybius square
Another example of a simple encryption is the Polybius square which uses a polyalphabetic cipher that lists letters on either the top or side, and numbers corresponding with the letters on the adjacent side.

The use of encryption has huge implications for anyone who wants to use the Internet securely and privately, especially when dealing with finance. The modern encryption methods are separated into 2 different protocols for encryption and decryption, Symmetric Key Encryption and Asymmetric Encryption
Symmetric Key Encryption
Lets say you have a box, a message, and a lock, you put the message into the box and lock it with your key then ship it to a friend for them to read the message. When the box arrives your friend opens up the box with an identical key, reads the message, and sends a reply locking the box with his identical key in your lock.
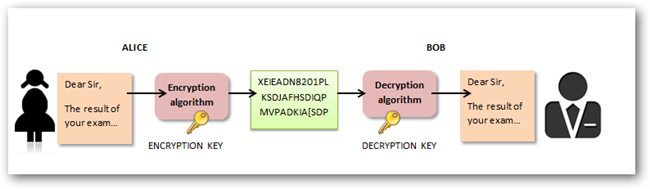
Symmetric Key Encryption can be divided into 2 types as well, with stream cyphers and block cyphers. Stream cyphers encrypt bits of the message at a time so it takes a bit longer than it's counterpart. Block cyphers encrypt in large groups of bits, usually in groups of 64, and does it as a single unit instead of on it's own. Some well respected algorithms are, Twofish, AES, and IDEA.
Asymmetric Encryption
So let's say you want to send another message to your friend but want to make it a bit more complicated for some reason, so you ask them to send a box with a lock you don't have a key for, you put your message in and lock the box and send it back. They get the box and open it with their key and need to respond to your message so they ask you for a box with your lock and they do the same as you did and so on. The advantage of this method is neither of you ever had to send the keys to the box so no one from the post office could make an identical key in order to steal your message.
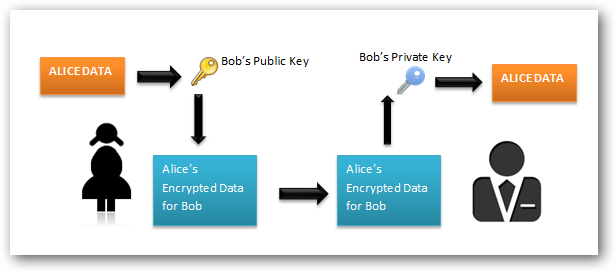
Asymmetric uses 2 different keys for encryption and decryption, a public and private key. The public key is given to the person who is sending the message to encrypt the message, while a private key is given to the recipient of the message. This is so that if sensitive information is being transferred between a server and a user. you don't have to be worried about the key being stolen because it is useless without the private key.
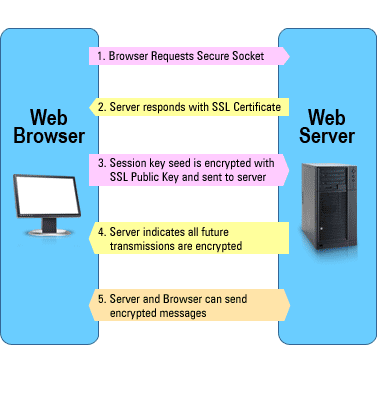
How it works online
Most sites you visit use HTTPS (Hypertext Transfer Protocol with SSL), this utilizes the power of TSL/SSL (Secure Socket Layer). SSL/TSL is a way of encrypting communications between a server and your browser, by a system of requests, public keys, and certificates. The process starts off with the browser sending a request to a web server, then the server sends back a certificate and a public key for communication. The browser then looks through a list of trusted certificates in order to see if communicating with the site is safe, if the site is considered safe then the browser sends a random symmetric encryption key with a URL for the site to decrypt. The server decrypts it and uses the key to view the URL and HTTP data. The server sends the key back to the browser with the HTML document and data encrypted with the key and displays the information requested
Learning about encryption is great especially on a website built off of a cryptocurrency. It is amazing to see how it has evolved and changed over time.
Easily an upvote. Encryption is one of those concepts that many of us hear about (myself included), but very few actually understand. Thanks for teaching me something new!
@OriginalWorks
The @OriginalWorks bot has determined this post by @cockroach to be original material and upvoted(1.5%) it!
To call @OriginalWorks, simply reply to any post with @originalworks or !originalworks in your message!
Really detailed piece. Resteemed.