Hello and welcome, I am currently working on a video course 'addressing' IP version 4, and I've decided to post my slides and scripts here on STEEM as I go along. I appreciate any feedback or suggestions, or if you are new to the world of computer networking, I hope you enjoy them!
Here is part 6 of a multi-part series. How many parts will there be? I have no idea because I am posting them as I go along. This section can be a bit repetitive, but you could skip through it fairly fast once you pick up the pattern of what happens to the number of networks and hosts as you add a bit to the subnet mask.
If you missed any sections, click one of the links below for your favorite front end:
PART 1:
https://steempeak.com/palnet/@joshman/course-ip-version-4-addressing-and-subnetting-deep-dive-part-1
https://steemit.com/palnet/@joshman/course-ip-version-4-addressing-and-subnetting-deep-dive-part-1
https://busy.org/@joshman/course-ip-version-4-addressing-and-subnetting-deep-dive-part-1
PART 2:
https://steempeak.com/palnet/@joshman/course-ip-version-4-addressing-and-subnetting-deep-dive-part-2
https://steemit.com/palnet/@joshman/course-ip-version-4-addressing-and-subnetting-deep-dive-part-2
https://busy.org/@joshman/course-ip-version-4-addressing-and-subnetting-deep-dive-part-2
PART 3:
https://steempeak.com/palnet/@joshman/course-ip-version-4-addressing-and-subnetting-deep-dive-part-3
https://steemit.com/palnet/@joshman/course-ip-version-4-addressing-and-subnetting-deep-dive-part-3
https://busy.org/@joshman/course-ip-version-4-addressing-and-subnetting-deep-dive-part-3
PART 4:
https://steempeak.com/palnet/@joshman/course-ip-version-4-addressing-and-subnetting-deep-dive-part-4
https://steemit.com/palnet/@joshman/course-ip-version-4-addressing-and-subnetting-deep-dive-part-4
https://busy.org/@joshman/course-ip-version-4-addressing-and-subnetting-deep-dive-part-4
PART 5:
https://steempeak.com/stem/@joshman/course-ip-version-4-addressing-and-subnetting-deep-dive-part-5
https://steemit.com/stem/@joshman/course-ip-version-4-addressing-and-subnetting-deep-dive-part-5
https://busy.org/@joshman/course-ip-version-4-addressing-and-subnetting-deep-dive-part-5
From here I’m going to go through each of the /24 and longer subnet lengths and show you how they break down into subnets. It can be repetitive, but I think it’s essential to picking up the pattern and easily picturing subnets in your head.
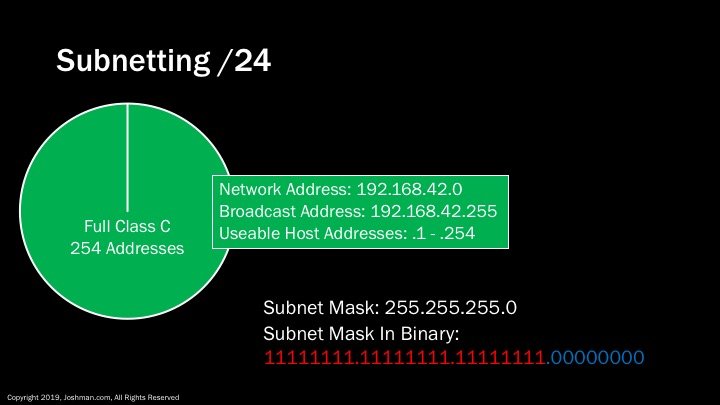
First we have the ubiquitous /24 or Class C subnet. This is most common subnet to deploy from my experience. When you have plenty of addresses to work with, such as when you are using private addresses, you can worry less about being conservative with IP addresses. When you have a decent sized enterprise, and all you have to work with is a /24, subnetting is essential.
As we’ve covered previously, we the network address, subnet mask, broadcast and host address, and usable hosts for a /24. I’ve also broken the subnet mask down to binary, so you can see how it changes as we ad bits for subnetting. There are 254 useable addresses in a /24 because 2^8-2 is 254. At this point, we have an entire /24 pie, so let’s start slicing it up!
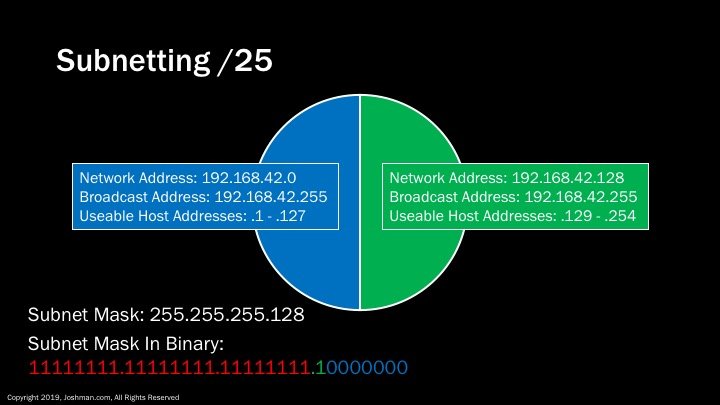
For a /25 we claim the first bit of the host address to be used for subnetting. This bit is indicated in green on the binary subnet mask. We know that the first bit represents 128 in decimal, so it creates a network address of either 0 or 128. This splits the /24 into two parts. Each part has 126 useable addresses because 2^7-2 = 128.
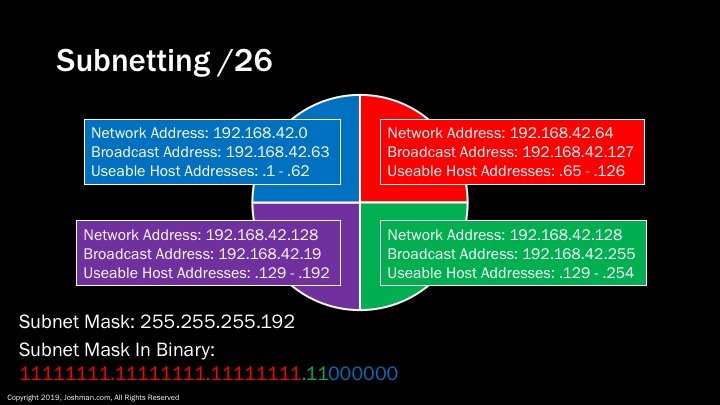
For a /26, we add another subnet bit (indicated in green). This splits the /24 into four parts. Each has 62 addresses, because 2^6-2 = 62. Do you see a pattern yet?
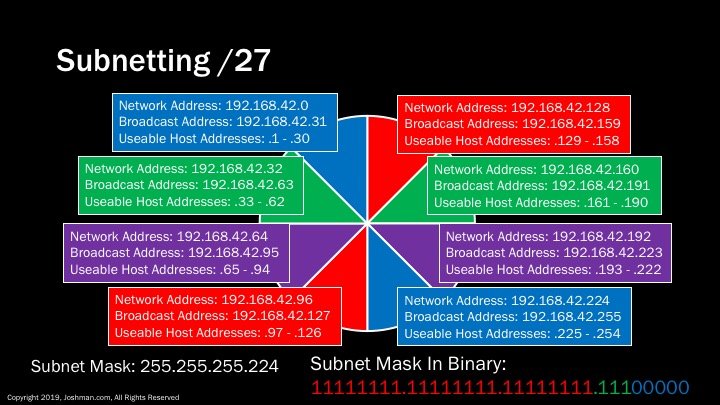
For a /27, we add yet another subnet bit (indicated in green). This splits the /24 into eight parts. Each has 30 addresses, because 2^5-2 = 30. Now the slide is starting to get crowded.
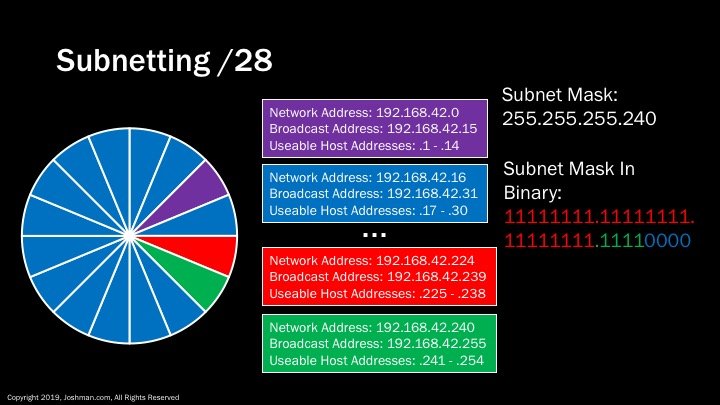
For a /28, we add yet another subnet bit (indicated in green). This splits the /24 into sixteen parts. Each has 14 addresses, because 2^4-2 = 14. I can’t fit them all here, you’re going to have to take my word for it.
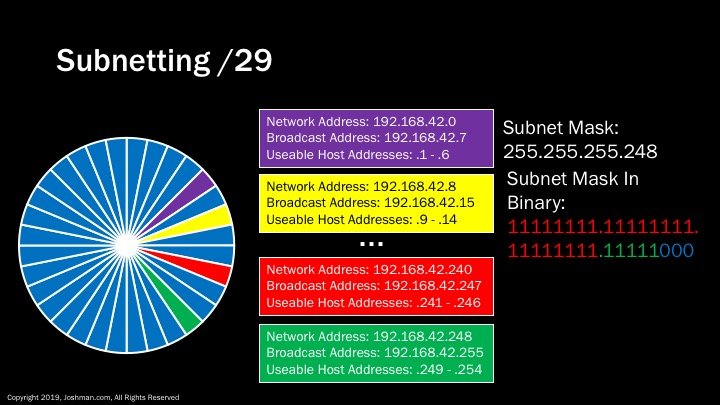
For a /29, we add still another subnet bit (indicated in green). This splits the /24 into thirty-two parts. Each has 6 addresses, because 2^3-2 = 6. I can’t fit them all here, you’re really going to have to take my word for it.
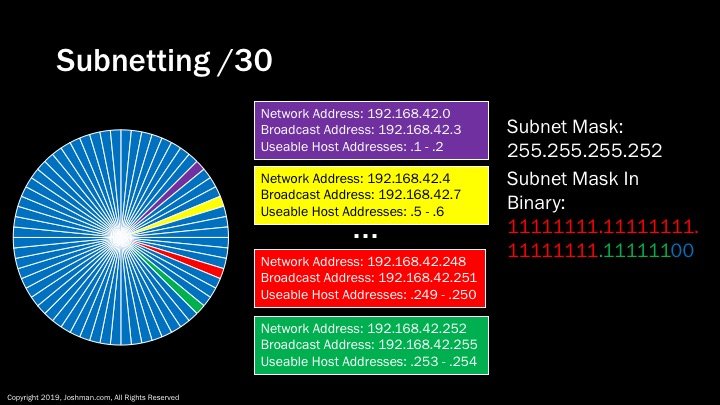
For a /30, you know the deal. This splits the /24 into sixty-four parts. Each has 2 addresses, because 2^2-2 = 2. That’s a lot of slicing, but you are also wasting half of your IP addresses when they are transformed to network and broadcast addresses. A /30 is typically used for point-to-point links, or the extremely rare occasion where you need to have a network with a single IP address. Why do I say a single IP address when there are clearly 2 available? This is because that single device will need a default gateway to reach any other network. I normally recommend not to place a device such as a server onto a /30 network, because it leaves you no room for expansion. You will learn about default gateways a bit later.
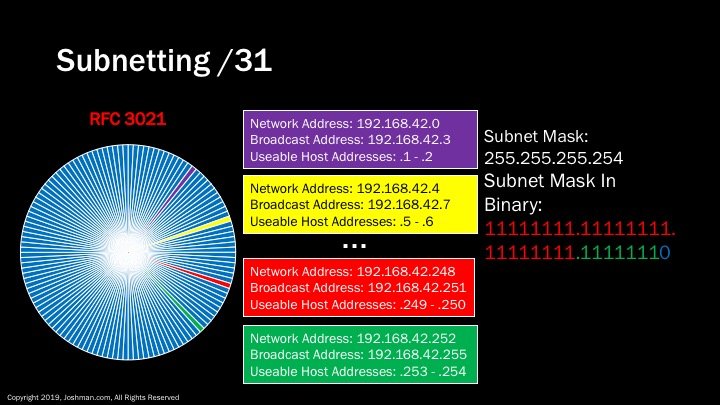
Then we arrive at the /31. The /31 was standardized in 2000 in RFC 3021. It creates a subnet type the previously did not exist. The /31 slices a Class C network into 128 parts. The kicker is, there is no network or broadcast address. It is just two addresses. This subnet type is meant specifically for point-to-point Wide Area Network (WAN) links used for routing protocols to exchange information.
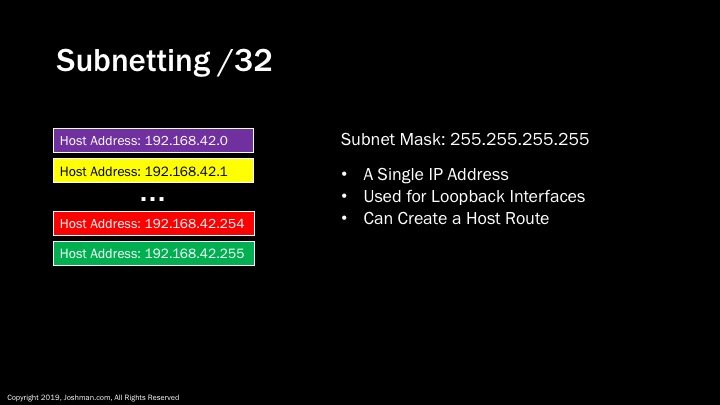
Finally we have a /32. A /32 really isn’t a subnet. It’s how we reference a single IP address, so a /24 or Class C can contain 256 of them. You can also use the .0 or .255 as host address when using a /32. A /32 is often used for adding an IP address to a loopback interface. A loopback interface is simply a logical interface on a device used exclusively for management and monitoring. In routing a /32 address and subnet mask is referred to as a host route, meaning you can create a network route pointing to a single IP address. IP routing is beyond the scope of this course.
Thanks for viewing. In the next part, we will go over subnetting networks larger than a /24, and how you can mix and match different length subnets within the same network block.
This post has been voted on by the SteemSTEM curation team and voting trail. It is elligible for support from @curie.
If you appreciate the work we are doing, then consider supporting our witness stem.witness. Additional witness support to the curie witness would be appreciated as well.
For additional information please join us on the SteemSTEM discord and to get to know the rest of the community!
Thanks for having added @steemstem as a beneficiary to your post. This granted you a stronger support from SteemSTEM.
Please consider using the steemstem.io app to get a stronger support.
Thanks again!
Erratum:
The first slide should list 256 addresses in the pie chart. Although it's technically correct there is 254 useable addresses within a Class C. I want to make it clear that we are subnetting the entire class C and not just the usable addresses.
Thanks for setting steemstem as benificiary :o)
Thank you joshman! You've just received an upvote of 64% by tommyknockers!
Learn how I will upvote each and every one of your posts
Please come visit me to see my daily report detailing my current upvote power and how much I'm currently upvoting.
Thanks
Posted using Partiko Android
Shall we sign an armistice? I'm about to break even with you. I suggest that we don't take further action before next time who start a fight. Includes john37.speaker1, john371911, joshman, and your merrie men of anti-abuse collective.
This is not a war, you abused bid bots and got flagged for it. You are too much of a child to deal with the result, so you then started to abuse flags to "get even". I am not here to fight or get even with anyone. If you abuse bid bots, I am going to flag you. If you choose to continue to abuse the system as it was designed, you are going to find yourself on blacklists for abuse, and you will find it increasingly more difficult to be successful here. I will continue to collect evidence of this abuse, so the justification will not be difficult.
The community sets the rules, not you. If you do not participate in abuse, you'll never hear from me or my "merrie men".
To me it's you that violate "no penalty without a law" and childishly flagging others, try to play justice instead of making clear rules, making steem environment worse. So I just fought for my right.
There are only two common rules on the steem far as I know, no plagiarism and the necessity to use NSFW tag in some posts. Others are just private rules.
If I feel your post is over-rewarded, I have the right to return whatever amount I choose up to 100% of my voting power. I also have the right to assemble with others that feel the same way. My reason for downvoting was always clear. You downvote indiscriminately in retaliation. That is technically your right. If you want to continue to make yourself a pariah on this platform, just keep up what you are doing, nobody can stop you.
Posted using Partiko Android
If the question is, will I flag you for the recent abuse of flags? As stated, I have left it up to community how to proceed, and will not take unilateral action, though I am a member of the flag trail that was previously mentioned, so can make no promises.
Besides flag trail, is there any other communitie?
Most communities, tribes, etc. support anti-abuse efforts and work closely together to police abuse and promote fair reward distribution.
Posted using Partiko Android