This is an adaptation for Steemit of KrebsOnSecurity. if you want to have it in HTML format you can see it here.
A story published here last week warned readers about a vast network of potentially malicious Web sites ending in “.cm” that mimic some of the world’s most popular Internet destinations (e.g. espn[dot]cm, aol[dot]cm and itunes[dot].cm) in a bid to bombard visitors with fake security alerts that can lock up one’s computer. If that piece lacked one key detail it was insight into just how many people were mistyping .com and ending up at one of these so-called “typosquatting” domains.
On March 30, an eagle-eyed reader noted that four years of access logs for the entire network of more than 1,000 dot-cm typosquatting domains were available for download directly from the typosquatting network’s own hosting provider. The logs — which include detailed records of how many people visited the sites over the past three years and from where — were deleted shortly after that comment was posted here, but not before KrebsOnSecurity managed to grab a copy of the entire archive for analysis.
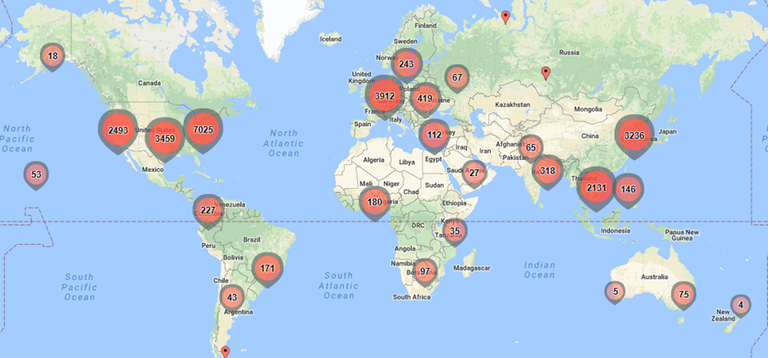
The geographic distribution of 25,000 randomly selected Internet addresses (IP addresses) in the logs seen accessing the dot-cm typosquatting domains in February 2018. Batchgeo, the service used to produce this graphic, limits free lookups to 25,000, but the above image is likely still representative of the overall geographic distribution. Perhaps unsurprisingly, the largest share of traffic is coming from the United States.
Matthew Chambers, a security expert with whom this author worked on the original dot-cm typosquatting story published last week, analyzed the access logs from just the past three months and found the sites were visited approximately 12 million times during the first quarter of 2018.
Chambers said he combed through the logs and weeded out hits from Internet addresses that appeared to be bots or search engine scrapers. Here’s Chambers’ analysis of the 2018 access log data:
January 2018; 3,732,488 visitors
February 2018: 3,799,109 visitors
Mar 2018: 4,275,998 visitors
Total Jan-Mar 2018 is 11.8 million
Those figures suggest that the total number of visits to these typosquatting sites in the first quarter of 2018 was approximately 12 million, or almost 50 million hits per year. Certainly, not everyone visiting these sites will have the experience that Chambers’ users reported (being bombarded with misleading malware alerts and redirected to scammy and spammy Web sites), but it seems clear this network could make its operators a pretty penny regardless of the content that ends up getting served through it.
Until very recently, the site access logs for this network of more than 1,000 dot-cm typosquatting sites were available on the same server hosting the network.
Chambers also performed “reverse DNS” lookups on the IP addresses listed in the various dot-cm access logs for the month of February 2018. It’s worth noting here that many of the dot-cm (.cm) typosquatting domains in this network (PDF) are trying to divert traffic away from extremely popular porn sites (e.g. pornhub[dot]cm).
“I’ve been diving thru the data thus far, and came up with some interesting visitors,” Chambers said. “I pulled those when it was easy to observe that a particular agency owned a large range of IPs.”
Chambers queried the logs from 2018 for any hits coming from .gov or .mil sites. Here’s what he found:
-National Aeronautics and Space Administration (JSC, GSFC, JPL, NDC): Accessed one of the .cm typosquatting sites 104 times in February, including 16 porn sites.
–Department of Justice (80 times) [7 porn sites]
–United States House of Representatives (47 times) [17 porn sites]
–Central Intelligence Agency (6 times)
–United State Army (29 times)
–United States Navy (25 times)
–Environmental Protection Agency (15 times)
–New York State Court System (4 times)
Other federal agencies with typosquatting victims visiting these domains include:
Defense Information Systems Agency (DISA)
Sandia National Laboratories
National Oceanic and Atmospheric Administration (NOAA)
United States Department of Agriculture
Berkeley Lab
Pacific Northwest Lab
Last week’s story noted this entire network appears to be rented out by a Colorado-based online marketing firm called Media Breakaway. That company is headed by Scott Richter, a convicted felon and once self-avowed “spam king” who’s been successfully sued for spamming by Microsoft, MySpace and the New York attorney general. Neither Richter nor anyone else at Media Breakaway has responded to requests for comment.
If you’re in the habit of directly navigating to Web sites (i.e. typing the name of the site into a Web browser address bar), consider weaning yourself of this risky practice. As these ubiquitous typosquatting sites show, it’s a good idea to avoid directly navigating to Web sites you frequent. Instead, bookmark the sites you visit most, particularly those that store your personal and financial information, or that require a login for access.
Update, April 5, 8:05 a.m. ET: An earlier version of this story included numbers that didn’t quite add up to almost 12 million hits. That’s because Chambers sent me multiple sets of numbers as he refined his research, and I inadvertently used figures from an early email he shared with KrebsOnSecurity. The monthly figures above have been adjusted to reflect that.