End-to-end encryption provides the highest level of protection for users who are seriously concerned about data privacy.
For private data management you no longer have to rely on third-party services that can:
- give you not enough protection of your data, giving it to hackers, special services and others;
- scan your data and share information to receive commercial benefits and do researches without the privity.
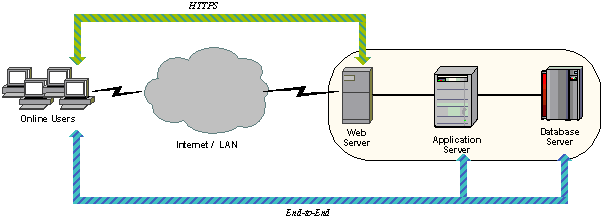
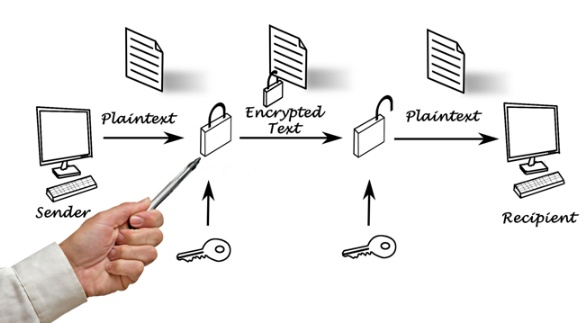
In the end-to-end encryption keys are used to encrypt and decrypt the information generated and stored only on the leaf nodes of correspondence, that is, on its participant's sides. The server side takes no part in creating keys and therefore has no access to them, it only sees the encoded data transmitted between the parties.
How the end-to-end encryption method works
During the beginning of the session, on the devices of each interlocutor 2 keys are generated: public and private. It is used to decrypt the data, this key does not leave the limits of the local device.
The public key for an open communication channel is transferred to the other party (one or all, if there are several). With the help of the public key interlocutor can only encrypt the source data, and only be the holder of the corresponding private key can decrypt it. Therefore, no matter who intercepts the public key. As a result, it can only transmit its encoded data.
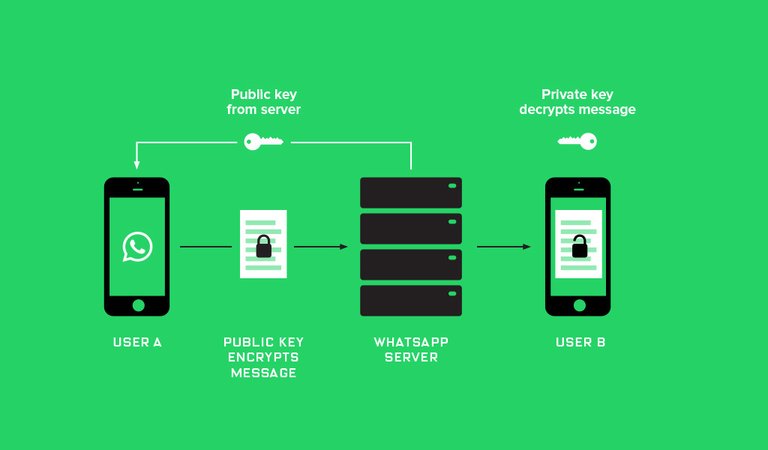
As a key pair is generated, the interlocutors exchange public keys, and then secure communication begins.
Text, video, audio, files after encryption get to the server where they are stored until the recipient is able to retrieve data. After that, depending on the strategy of the company - owner of the server, the data is either destroyed or stored for some time.
As we can see: end-to-end encryption - it's really good.
For modern ICT encryption / decryption will not be a daunting task, not even a difficult task. At the same time, if the conversation involves several interlocutors, then, sending a message, it is necessary for each one you need to encrypt it for both interlocutors, so with increasing amounts of interlocutors the load on the device equally increases. To do this, the developers optimize the means of the organization of group talks.
The idea of end-to-end is not new. Software for messages and other data encryption PGP(Pretty Good Privacy) was developed in 1991 by Phil Zimmerman. In subsequent years, the algorithm and corresponding software were improved and acquired additional mechanisms.
In 1997, the PGP company Inc. proposed initiative OpenPGP, a free implementation of PGP - GnuPG was created in 1999.
There were no examples of hacking PGP system, so encryption mechanisms based on the implementation of open PGP can be created by developers of different messengers.
End-to-end encryption can be a very important requirement in the increasingly popular Internet of things. In a world where every traffic light, and each car is connected to the Internet, smartphones know everything about their owners, authentication and encryption are vital.
The latest news about messengers allows optimistic predictions about the prospects for widespread implementation of features of end-to-end encryption. WhatsApp has recently added this capability to its messenger. Viber and Google seem to be moving in the same direction. All this points to the fact that large companies have adopted new rules of the game.

And maybe soon people will stop hoping that the services are not viewing their personal data. Services will even not be able to view the data.
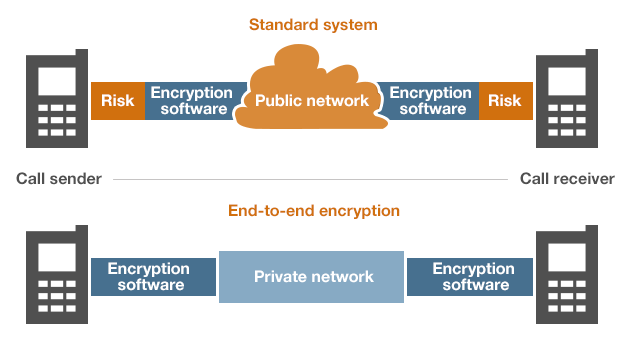
To date, in terms of security, we can divide messengers into two categories: messengers that implement full end-to-end encryption and the second category, they are systems for the exchange of messages that are just trying to be like the first category, although they encrypt outgoing data, these data can be easily read on the server.
Follow me, to learn more about popular science, math, and technologies
With Love,
Kate
Nice post, interesting to read about how this encryption works! :)