Cyber security is a set of tools, policies, security principles, security guarantees, risk management approaches, actions, training, insurance, and technology, which are used to protect the cyber environment, resources, organizations, and users. Cybersecurity means to achieve and maintain the security properties of the organization's resources or users against cyber attacks.
The primary goals of security are availability, integrity, including authenticity, and confidentiality. Cyber security is a prerequisite for the development of the information society.
Despite I'm studying at math department, we have pretty a lot computer science classes some of which specifically dedicated to cyber security. I explored there a lot of interesting topics some of which I would like to share with you. In my recent articles, I've already told about RSA algorithm and Hash functions and now is the time to tell you about DES.

In 1977, the US National Bureau of Standards (NBS) published the Data Encryption Standard (DES), made for use in the public and US government agencies to protect against unauthorized access to important but not secret information. The algorithm, which is the basis of the standard, spread quickly, and already in 1980 has been approved by ANSI. Since then DES became standard. There appeared specialized software and a microcomputer for encryption / decryption of information in networks and on magnetic media. At the present time, DES algorithm is the most widely used data protection systems. Why DES has achieved such popularity?
The main features of the DES algorithm
- only one key with a length of 56 bits is used;
- the simplicity of the algorithm provides high speed of information processing;
- sufficiently high resistance of algorithm.
Description and encryption of data
DES encrypts 64-bit data blocks using the 56-bit key. Decryption is the inverse of a DES encryption operation and is performed by repeating cryptographic operations in reverse order.
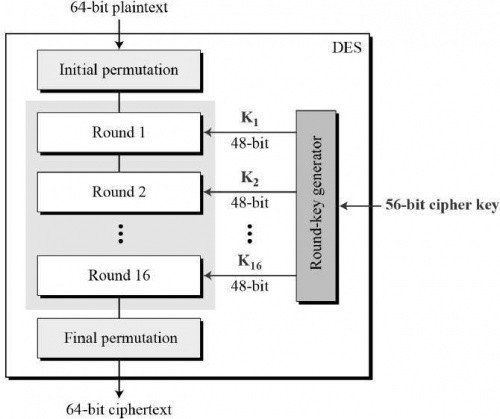
The encryption process is an initial permutation of bits of the 64-bit block, 16 cycles of encryption and finally inverse permutation of bits.
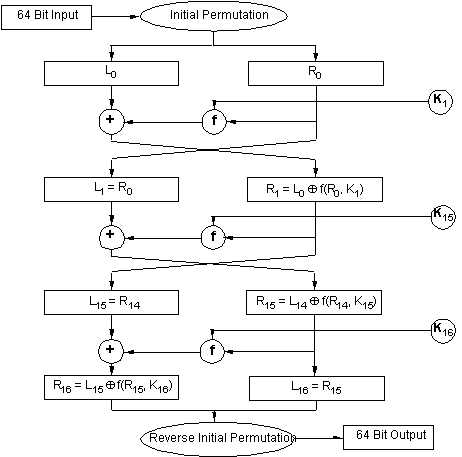
The 8-byte unit T is read from file, which is then converted by matrix of initial permutation of IP as follows:
Matrix of initial permutation (IP) (1):
58 50 42 34 26 18 10 02
60 52 44 36 28 20 12 04
62 54 46 38 30 22 14 06
64 56 48 40 32 24 16 08
57 49 41 33 25 17 09 01
59 51 43 35 27 19 11 03
61 53 45 37 29 21 13 05
63 55 47 39 31 23 15 07
Bit of a 58 block T becomes bit 1, bit 50 - bit 2, etc., which will result in: T (0) = IP (T). The resulting sequence of bits T (0) is divided into two sequences of 32 bits each: L (0) - left or upper bits, R (0) - right or lower bits.
Then, the encryption consists of 16 iterations. The result of the i-th iteration is described by the following formulas:
L (i) = R (i-1)
R (i) = L (i-1) xor f (R (i-1), K (i)), where xor - exclusive OR operation.
On the 16th iteration there is a sequence of R (16) and L (16) (without transposition) which are concatenated to a 64-bit sequence R (16) L (16).
Then, the bit positions of this sequence are transposed according to the IP-1 matrix
Matrix of inverse permutation of IP (2):
40 08 48 16 56 24 64 32
39 07 47 15 55 23 63 31
38 06 46 14 54 22 62 30
37 05 45 13 53 21 61 29
36 04 44 12 52 20 60 28
35 03 43 11 51 19 59 27
34 02 42 10 50 18 58 26
33 01 41 09 49 17 57 25
Matrix IP-1 and IP are related as follows: the value of the 1st element of IP-1 matrix is 40, and the value of the 40th element of IP matrix is 1, the value of the 2nd element of IP-1 matrix is 8, and the value of the 8th element of IP matrix is equal to 2, etc.
The process of decryption of data is inverted with the encryption process. All actions must be performed in reverse order. This means that the decrypted data is first rearranged in accordance with the IP-1 matrix, and then the same operations as in the encryption process, but in reverse order are made with a sequence of bits R (16) L (16).
The iterative process of the decryption can be described by the following formulas:
R (i-1) = L (i), i = 1, 2, ..., 16;
L (i-1) = R (i) xor f (L (i), K (i)), i = 1, 2, ..., 16.
On the 16th iteration sequence L (0) and R (0), which is concatenated to a 64-bit sequence L (0), R (0) is received.
Then, the bit positions of this sequence are transposed according to the IP matrix. The result of this permutation - the original 64-bit sequence.
Modes of DES algorithm
- Electronic Codebook - ECB;
- Cipher Block Chaining - CBC;
- Cipher Feedback - CFB;
- Output Feedback - OFB.
Let's look at all these modes
DES-ECB
In this mode, the source file M is partitioned into 64-bit blocks (8 bytes each): M = M (1) M (2) ... M (n). Each of these blocks is encoded separately using the same encryption key. The main advantage of this algorithm - ease of implementation. Disadvantage - relatively weak resistance against skilled cryptanalysts.
DES-CBC
In this mode, the M source file as well as in the ECB mode is divided into 64-bit units: M = M (1) M (2) ... M (n). The first block M (1) is summed by modulo 2 with 64-bit initial vector IV, which is changed daily and kept in secret. The resulting amount is then encrypted using the DES key, that is known to the sender and recipient. The resulting 64-bit block of ciphertext C (1) is summed by modulo 2 with the second plaintext block, and there appears the second encrypted 64-bit block of ciphertext C (2) etc. The procedure is repeated as long as there are no more blocks of plaintext.
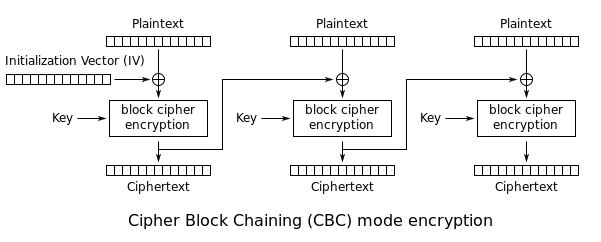
The beauty of this mode is that it does not allow transmission errors to accumulate. M (i) is a function unit only for C (i-1) and C (i). Therefore, an error in the transmission will result in the loss of only two of the original blocks of text.
DES-CFB
In this mode, the block size can vary from 64. Source file M is read by t-bit blocks (t <= 64): M = M (1) M (2) ... M (n).
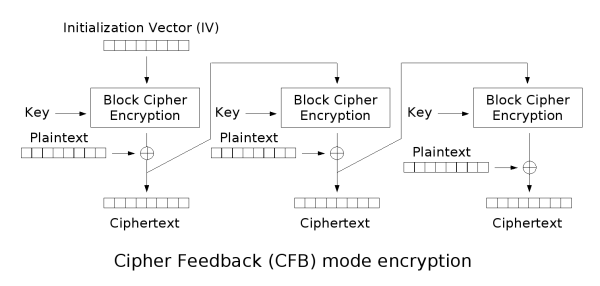
The 64-bit shift register (input section) comprises an initialization vector IV, aligned to the right. For each encryption session, the new IV is used.
For all i = 1 ... n C (i) ciphertext block is defined as follows:
C (i) = M (i) xor P (i-1), where P (i-1) - upper t bits of DES operation (C (i-1)), and C (0) = IV.
Updating of the shift register is done by removing its upper t bits and appending of **C (i) to the right.
Recovery of encrypted data also presents no difficulty: P (i-1) and C (i) are computed similarly and
M (i) = C (i) xor P (i-1).
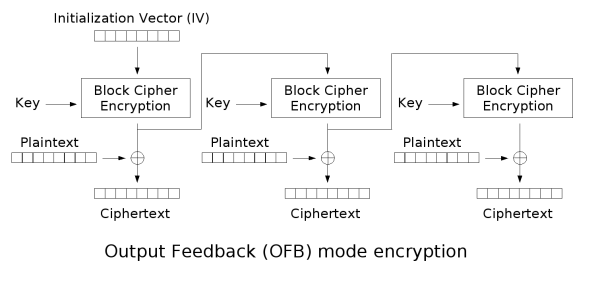
DES-OFB
OFB mode is very similar to CFB mode.
CFB mode is different with the OFB method only by the shift register updating. In this case, it is done by removing upper t bits and appending P (i-1) to the right.
So you see that DES is popular and fast cryptography algorithm, which has been developed 40 years ago and was used by specialists from all over the world to fight against hackers. Now DES algorithm is considered to be insecure due to the short key size that is just 56 bit and can be hacked, that's why in 2001 it was substituted by advanced encryption standard (AES). Despite currently DES is not used widely, it made a great impact on development of modern cryptography
If after reading this short article you want to learn about DES in more detail I would recommend starting from reading the following articles: 1, 2 3 or watch this explanatory video from Gideon Samid.
Follow me, to be the first to learn about my publications devoted to popular science and educational topics
With Love,
Kate
The government does things like insisting that all encryption programs should have a back door. But surely no one is stupid enough to think the terrorists are going to use encryption systems with a back door. The terrorists will simply hire a programmer to come up with a secure encryption scheme.
Of course, there are a lot of well-known and secure encryption schemes that can be used. A lot of them are implemented in code and open sourced so you can easily check whether it has a backdoor