
Researchers at the Massachusetts Institute of Technology announced the creation of an anonymous network that, according to them, safer Tor. The relevant announcement was published on the news portal MIT.
The work was begun after in the popular anonymous Tor network found a number of vulnerabilities. Last year it became known that the FBI used Tor for Firefox vulnerability in order to obtain data on viewed pages and sites. The aim was to find darknet users interested in or spreading, primarily child pornography.
After this incident, researchers at MIT have set a goal to create a network, devoid of such shortcomings.
Novelty called «Riffle» is scheduled to present at the Privacy Enhancing Technologies Symposium, which is held in Darmstadt, Germany. Developers do not have to reinvent the wheel, and recognize that «Riffle» operates using the existing encryption algorithms, but from the existing development in the field of network features a different approach to them, the algorithms used.
As Tor, "Riffle" uses a so-called "onion" encryption (which is why the bulb is on the Tor logo). This method "wraps" a message to multiple encryption layers, which are removed in stages at each hop server to send further down the chain. Thus, the final destination is known only to the last server in the forward chain, while the intermediate points are known only to the neighboring Hopa.
In «Riffle» based on the work of anonymous networks is the use of mixnet network. messaging principle is simple enough, but at the same time effective.
If several people send messages in a specific order 1-2-3, the first server that will accept them, this order will change and the next node, they will leave as a 3-1-2. Each server in the chain will change the order of sending to hamper attempts to track down a particular package.
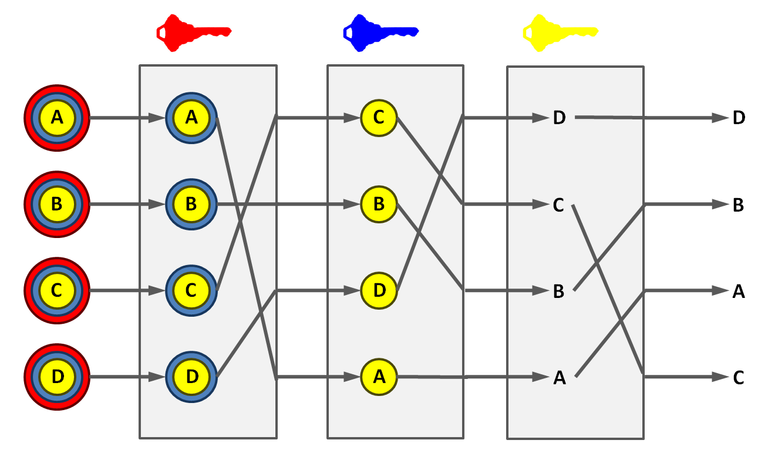
Principle Mixnet
This approach can significantly save on resources and reduce time messaging, compared with other anonymous networks, at times. This is critical, as in anonymous networks as transit servers often act computers of other users. Plus, the developers abandoned not too good practice for using public key.
Also, according to the developers hallmark "Riffle" is that even the compromised server can not properly "shuffle" message.
At the same time, there is one big BUT. If one of the servers in the chain between the sender and the recipient will be compromised and its algorithm "shuffle" packages will be broken, the message may not reach the goal. In the context of classical encryption methods used as a resource-intensive to encrypt and to decrypt the message, however, other factors affect to forward slightly. With the system as "shaflinga" packages you need something more than just encryption - Stable net to be sure that the information reaches its destination.
I upvoted you.