
Have you heard about Coinhive? Coinhive is a malicious browser-based cryptocurrency mining snippet, that website owners can include in the website. As an unsuspecting visitor comes to the website in question, Coinhive miner will secretly use that visitors processing power to mine Monero, the privacy coin.
In October2017, Check Point Software, a cyber-security firm, announced that Coinhive is already the 6th most common malware in the world. What enourmous number of users are already affected by it, we can only guess. Maya Horowitz, a manager at the cyber-sec firm, said that "crypto mining is new, silent, yet a significant threat".
Via coindesk.com
Already at the end of last year we got reports, that Coinhive has taken this new threat one step further. Apparently websites running the Coinhive script, can now, after the user closes the tab, open browsers as a background process and keep mining, using the users computing power. Earlier this could only be done, when the user under attack remained on the website.
Why is this significant? Because most popup-blockers are helpless against this type of trickery by the malicious script. Luckily many antivirus apps are able to detect and block Coinhive from running and there is also a nice range of browser extensions made specifically to block Coinhive.
One of the most famous is No Coin, available at the Chrome Store for free. Follow this link to get it.
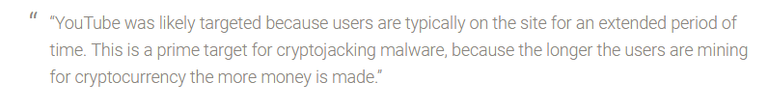
But now we get to the most recent news. According to a report by Trend Micro, they observed the detections of Coinhive miners tripling. And the reason for this was, as they called, "a malvertising campaign". Coinhive miner has been injected into Google's Doubleclick ads, which might trick users with false warning about malware. One of the most affected websites was Youtube, where users started complaining, that staying on the site, drains their CPU power. Accoring to an independent reseacher, Tony Mursch, Youtube was probably targeted as users tend to stay on that site for extended periods of time.
According to Google, this issue was fixed almost immediately, but Trend Micro claims they have evidence, that indicates that the malicious scripts were running for at least week after Google reported this issue fixed. According to TM, the jump in the number of miners on January 24th, was a whopping 285% and according to some experts, they expect this number to grow even more.
What can you do to protect yourself?
Installing the No Coin browser extension and blocking javascript-based apps in browser settings is a good start.
Be safe out there.
Sources:
https://bitsonline.com/computer-mining-cryptocurrency/
https://www.coindesk.com/coinhive-cryptocurrency-miner-is-6th-most-common-malware-says-report/
ttps://www.trendmicro.com/vinfo/us/security/news/cybercrime-and-digital-threats/coinhive-miner-the-6th-most-common-malware
bitsonline.com - Illegal Cryptocurrency Mining Scripts Target YouTube Viewers
Check out Chainbb, an alternative frontend for STEEM network. If you like forum style, that's the platform for you.
Title image from pixabay


Are you looking for Minnowbooster, Buildteam or Steemvoter support? Or are you looking to grow on Steemit or just chat? Check out Minnowbooster Discord Chat via the link below.

BuildTeam

Some actually seek out in-browser mining where it's a voluntary way to pick up some crypto change without expensive rigs, for everyone else there are a few things that can be done even without plugins or extensions, such as:
GOTO 4GOTO 1GOTO 4GOTO 1- seriously, human behaviour is the most significant undermining factor in system and data security, no amount of blind faith in the totemic magical warding powers of this or that ste-and-forget software you installed aeons ago can protect you from your own actionsFirefox and Google Chrome both have a private browsing mode that can block coinhive and many other such tricks that use tracking & scripting to fingerprint your computer, cache profile data locally, and load remote resources for execution on your system.
click for larger view
click for larger view
Remember: Internet St is not equal to Sesame St, despite the interesting people you may meet.
Nice feedback, thanks man!
Just read about it in some local major news site, your report is much more extensive and better so thanks!
Just found out that the same method have been used in local popular sites in my country - affecting about 4 million users (in a country of about 7 million!) so that's a big risk :(
Apparently Adblock plus claim they did block Coinhive with the "easylist" filters but I am not sure if it covers the new method you mentioned so better just install that app you suggest too.
i had been infected a few weeks ago and my machine became slow, i installed no coin and all went back to normal , we must be vigilant annd spread the word around cause most people dont know about it
HI @furious-one ,
Great read thanks for that , i was not even aware of this.
Do you know of any protection software that blocks it ?
Yes i do, and it's also mentioned in my article :P
OK I will have to go back and read this a few more times.

Wow... I just knew about this. Thanks much for the info. Research now should be based on how to block this malwares.
Once again, thanks for the information, really helpful I believe
Great information thanks
Thanks for sharing this informative and awareness spreading post, yes now days malware attacks are increasing and genuine people who want to earn from mining can get effected by these types of Malware, hope that some new technology will be developed to prevent these malwares. Thanks for sharing.
Have a great day and stay blessed.
Very useful information for protecting computers.
Yes, hackers are completely insolent =) I have already done everything that you advised. Thank you so much.

Of course, Google wanted to reassure its users, so that they did not chew. Hmmm ... And what if Google itself is interested in such an illegal way of earning?)))
It seems to me that everything can be in our world.
Thank you for the article, @furious-one!
I really appreciate your expert opinion - https://steemit.com/trading/@maksym7/trading-ideas-on-tuesday-btc-eth-xrp-and-bch
Thank you!