
Address spoofing attacks, often employed by malicious actors, can redirect traffic, disrupt services, or gain unauthorized access to sensitive data by inserting false information or altering routing tables. These attacks exploit vulnerabilities in network protocols, posing a significant threat to data integrity and network security.
This article aims to explore the concept of address spoofing attacks, their various forms and consequences, and strategies to safeguard against such threats.
Address Spoofing Attacks in the Crypto Realm
In the world of cryptocurrencies, hostile activities where attackers manipulate or deceive users by tampering with cryptocurrency addresses are known as address spoofing attacks. On a blockchain network, these addresses, composed of specific alphanumeric strings, serve as the source or destination of transactions. These attacks employ various tactics to compromise the security and integrity of cryptocurrency wallets and transactions.
Address spoofing attacks in the crypto space are typically used for either illicitly acquiring digital assets or disrupting the smooth operation of blockchain networks. These attacks may involve:
Theft: Attackers may deceive users into sending their funds to malicious addresses using techniques like phishing, transaction interception, or address manipulation.
Disruption: Address spoofing can disrupt the normal operations of blockchain networks by introducing congestion, delays, or interruptions in transactions and smart contracts, reducing network effectiveness.
Misdirection: Attackers often attempt to mislead cryptocurrency users by impersonating well-known figures. This undermines community trust in the network and could lead to incorrect transactions or confusion among users.
To safeguard digital assets and the overall integrity of blockchain technology, address spoofing attacks underscore the importance of robust security measures and ongoing vigilance within the cryptocurrency ecosystem.
Types of Address Spoofing Attacks
Address spoofing attacks in crypto encompass phishing, transaction tampering, address reuse exploitation, Sybil attacks, fake QR codes, address mimicking, and smart contract vulnerabilities, each presenting unique risks to users' assets and network integrity.
Phishing Attacks: In the cryptocurrency domain, phishing attacks are a prevalent form of address spoofing. Criminal actors create fake websites, emails, or communications closely resembling legitimate entities like cryptocurrency exchanges or wallet providers. These fraudulent platforms aim to deceive unsuspecting users into revealing login credentials, private keys, or mnemonic phrases. Once obtained, attackers can execute unauthorized transactions and gain unauthorized access to victims' cryptocurrency assets.
Transaction Tampering: Another method of address spoofing involves attackers intercepting legitimate cryptocurrency transactions and altering the destination address. Funds intended for the rightful recipient are diverted by changing the recipient address to one under the attacker's control. This type of attack often involves malware compromising a user's device or network, or both.
Address Reuse Exploitation: Attackers monitor the blockchain for instances of address reuse before exploiting such occurrences to their advantage. Reusing addresses can compromise security by exposing the address's transaction history and vulnerabilities. Malicious actors leverage these weaknesses to access user wallets and steal funds.
Sybil Attacks: Sybil attacks involve creating multiple deceptive identities or nodes to exert disproportionate control over a cryptocurrency network's operation. With this control, attackers can manipulate data, deceive users, and potentially compromise network security. In proof-of-stake (PoS) blockchain networks, attackers may employ numerous fake nodes to significantly influence the consensus mechanism, allowing them to alter transactions and potentially double-spend cryptocurrencies.
Fake QR Codes or Payment Addresses: Address spoofing can occur when counterfeit payment addresses or QR codes are distributed. Attackers often distribute these fake codes physically to unsuspecting users, aiming to trick them into sending cryptocurrency to an unintended address. Users who scan these codes inadvertently send funds to the attacker's address instead of the intended recipient, resulting in financial losses.
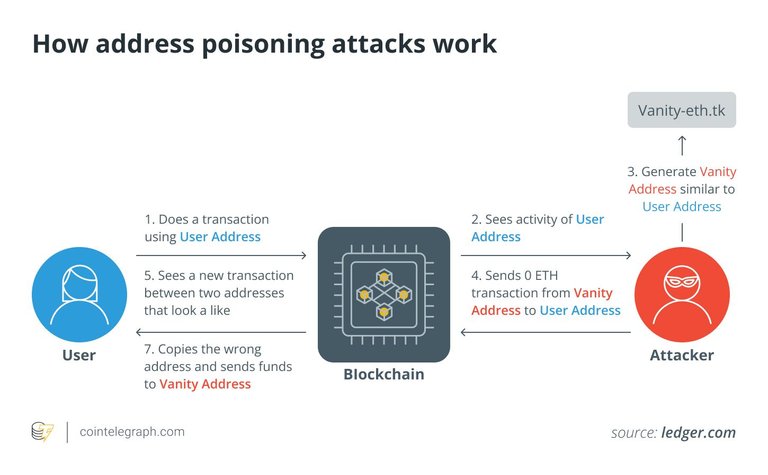
Address Mimicking: Attackers using address mimicking create cryptocurrency addresses that closely resemble legitimate ones. The goal is to deceive users into sending money to the attacker's address instead of the intended recipient's. This method relies on the visual similarity between the fake address and the genuine one.
Smart Contract Vulnerabilities: Attackers exploit flaws or vulnerabilities in decentralized applications (DApps) or smart contracts on blockchain systems to carry out address spoofing. Attackers can reroute funds or manipulate the contract to behave unintentionally by tampering with transaction execution. This can lead to financial losses for users and disruptions in decentralized finance (DeFi) services.
Consequences of Address Spoofing Attacks
Address spoofing attacks can have severe consequences for both individual users and the overall stability of blockchain networks. These attacks often result in significant financial losses for victims, as attackers may steal cryptocurrency assets or manipulate transactions to redirect funds to their own wallets.
Beyond financial losses, these attacks can erode users' confidence in the security and integrity of blockchain networks and related services. Users who fall victim to fraudulent schemes or have their assets stolen may lose trust in the cryptocurrency ecosystem.
Additionally, certain address spoofing attacks, such as Sybil attacks or the exploitation of smart contract vulnerabilities, can disrupt blockchain networks, causing delays, congestion, or unexpected outcomes that impact the entire ecosystem. These effects underscore the need for robust security measures and user awareness in the crypto ecosystem to mitigate the risks of address spoofing attacks.
How to Avoid Address Spoofing Attacks
To safeguard users' digital assets and maintain the security of blockchain networks, it is crucial to prevent address spoofing attacks in the cryptocurrency world. The following measures can help prevent becoming a target of such attacks:
Use Fresh Addresses: Create a new cryptocurrency wallet address for each transaction to reduce the likelihood of attackers linking an address to your identity or previous transactions. For example, address spoofing attacks can be reduced by using Hierarchical Deterministic (HD) wallets, which generate new addresses for each transaction, minimizing address reuse.
Utilize Hardware Wallets: Hardware wallets offer a more secure alternative compared to software wallets. They limit exposure by keeping private keys offline.
Exercise Caution When Sharing Public Addresses: Exercise caution when sharing your crypto addresses in public forums, especially on social media platforms, and consider using aliases.
Choose Reputable Wallets: It's crucial to use well-known wallet providers known for their security features and regular software updates to shield yourself from address spoofing and other attacks.
Regular Updates: To stay protected against address spoofing attacks, it's essential to regularly update your wallet software with the latest security patches.
Implement Whitelisting: Consider using whitelisting to restrict transactions to trusted sources. Some wallets or services allow users to whitelist specific addresses that can send funds to their wallets.
Consider Multisig Wallets: Multisignature (multisig) wallets require multiple private keys to authorize a transaction. These wallets can provide an additional layer of protection by requiring multiple signatures to approve a transaction.
Use Blockchain Analysis Tools: To identify potentially malicious behavior, individuals can track and analyze incoming transactions using blockchain analysis tools. Sending seemingly insignificant, small amounts of cryptocurrency (dust) to various addresses is a common practice known as coin mixing. Experts can detect potential spoofing attempts by examining these dust transaction patterns.
Unspent Transaction Outputs (UTXOs) with small amounts of cryptocurrency are often the result of dust attacks and should be closely monitored for potential risks.
By adopting these practices and remaining vigilant, cryptocurrency users can reduce the risk of falling victim to address spoofing attacks and contribute to a safer crypto ecosystem.