
The original report can be found on Medium: https://medium.com/konfid-io-blockchain-reports/iota-report-decoding-the-tangle-part-1-a7705c458583
IOTA Report: Overview
Introduction
This four-part series aims to provide an in-depth analysis of IOTA. The project is looking to disrupt traditional blockchain systems by utilizing a new type of distributed ledger technology to enable a scalable, trustless, and feeless network suitable for microtransactions in the Internet-of-Things (IoT) industry. We aim to provide an objective overview of the project and how it works (Part 1), the history of the IOTA token, the Foundation and the token distribution (Part 2), the tech and the protocol (Part 3), and its possibilities & limitations (Part 4).
Why IOTA?
The value of the tradable token of the IOTA protocol, MIOTA, peaked at $5.66 on December 19th, accounting for a market cap of over $15 billion, and trading volumes north of $1 billion per day. Although there are several open questions about the practical usability and several controversies in the past, the IOTA project established itself as one of the biggest names in the crypto space as of today.
Abstract: Part 1
In the first part we briefly discuss the basics of IOTA, how it works, its vision, which technology it utilizes, how it differs from blockchain protocols like Bitcoin, why it uses ternary logic, and the process of publishing transactions onto the ledger.
Part 1: How IOTA works in a nutshell
What is IOTA ?
IOTA is a new transaction settlement and data transfer layer for the Internet of Things (IoT). It’s based on a newly designed distributed ledger, the Tangle, which aims to overcome the inefficiencies of current Blockchain protocols by introducing a new way of reaching consensus in a decentralized peer-to-peer system.
IOTAs Vision
The project promises to deliver a scalable, decentralized, trustless, partition tolerant network that allows for feeless micropayment transactions. By doing so, internet-connected devices can make transactions with each other without any kind of human intervention. IOTA is experimenting with a blockless architecture and novel verification method to achieve consensus.
To execute on its vision, IOTA must overcome hurdles such as becoming fully decentralized, establishing trust in its novel cryptography, and creating a network that can viably be supported by small IoT devices with limited resources.
Brief Summary of the Technology
How IOTA differs from Blockchains
In comparison to blockchains, which employ a system where two distinct parties (transaction issuers & miners) are needed to generate and verify transactions on a distributed ledger, the Tangle introduces a more homogeneous approach. The IOTA network consists of nodes that do both, as they “issue and validate transactions” simultaneously (IOTA Whitepaper, p.2).
In order to add a transaction to the Tangle, nodes have to approve two previous transactions. This leads to a data structure called directed acyclic graph (DAG) (as seen in Figure 1), which notably differs from the linear data structure of a blockchain. IOTA is using a DAG as a distributed ledger because it is trying to move away from the restrictions of traditional blockchain architectures, which have seen a notable increase in transaction fees due to scaling limitations of having each node process every transaction that is broadcasted to the network.
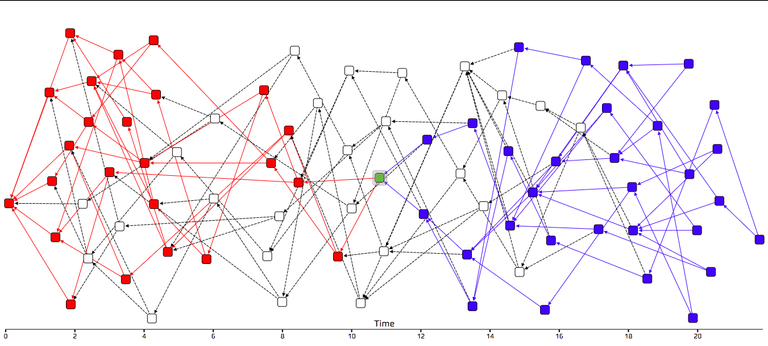
In Figure 1 (time since genesis on the horizontal axis), the green transaction directly or indirectly references all red ones including the genesis transaction at the far left. Similarly, the green transaction itself is referenced directly or indirectly by all blue ones on the right.
The Tangle
As described in the Whitepaper, the Tangle is a data structure which uses “a directed acyclic graph (DAG) for storing transactions” (WP p.1). A transaction is also known a site. A site may be added to the Tangle by referencing and verifying two previous sites. As sites are added, the Tangle grows but always references the genesis site created by the Foundation at the beginning of 2016 which contains the original transaction from a single address to all crowdfunding participants. Unfortunately it is not practical to go back in time and look at the genesis transaction, as the IOTA Foundation shortens the history of the network on a regular basis, which will be discussed in more depth in the following parts.
Approving Transactions
The IOTA protocol demands no explicit fees to submit a transaction to the network. However, in practice IoT devices must verify two previous transactions and solve a minuscule PoW problem. Both these processes require computational resources, and therefore represent a cost.
Publishing Transactions to the Ledger
Submitting a transaction to the tangle is conducted in the following manner:

Steps involved in publishing transactions
- Signing
A node first signs its transaction with its private key.
- Tip selection
The node randomly chooses two unapproved transactions (‘tips’) according to a specific algorithm. A tip is a newly created transaction that is waiting for approval by other transactions. The Whitepaper states that the creators “do not impose any rules for choosing which transactions a node will approve” (WP, p.3). However, it suggests using the Markov Chain Monte Carlo (MCMC) tip selection algorithm, an algorithm used to select tips randomly based on the size of their cumulative transaction weights. The MCMC is used by most clients to create some reference rules for transactions on how to choose which previous transactions they should validate.
- Validation
After selecting the tips, the node has to check “if the two transactions are not conflicting” (WP, p.3) and select new tips if they are. In addition, it has to verify that those two transactions performed appropriate Proof-of-Work on their part. If one of the previous transactions verified an invalid transaction, then that transaction will not be verified.
- Proof-of-Work (PoW)
In order to issue a valid transaction, the Whitepaper states that “the node must solve a cryptography puzzle similar to those in the Bitcoin blockchain” (WP, p.3). Unlike Bitcoin’s PoW, IOTA nodes do not compete for block rewards and the difficulty remains unchanged as the needed computation simply acts as a spam protection.
- Publishing
Once steps 1-4 are completed by the node, the transaction is published to the Tangle.
These significant differences in the approach of how transactions are published on the ledger were designed with the intention of overcoming some of the drawbacks of traditional blockchain protocols like Bitcoin which include high hardware requirements of full nodes and its corresponding scalability issues for the network.
Ternary Hardware
The IOTA protocol is using a rather unconventional approach, as the protocol is based on ternary logic. “Ternary logic is more efficient than binary logic”, claims IOTA founder David Sønstebø in an interview beginning of 2018. He argues that ternary computation is important for enabling the creation of what he calls the “mbit market” consisting of small micro controllers or sensors that are deployed in the open field and are expected to run for 15 to 20 years straight. Making devices just fractionally more energy efficient using ternary is hence seen by Sønstebø as significant in terms of resource savings over time.
At the moment, only a fraction of nodes on the Tangle use ternary hardware, because wide adoption has not yet occurred on a global scale. We will briefly discuss the impact of using ternary hardware in todays world in the last part of this series.

Summary
IOTA is a distributed ledger for the internet of things (IoT).
IOTA employs the Tangle which is a distributed ledger protocol based on ‘Directed Acyclic Graphs’ (DAGs).
The Tangle aims at providing a scalable, decentralized, feeless, trustless, partition tolerant network.
The Tangle tries to compensate the drawbacks of PoW/PoS systems associated with many blockchains.
Issuing transactions demand no explicit fee.
A transaction is also called a site. A verification of two previous sites validates a transaction.
Ternary logic is used for efficiency reasons, but will only be successful if ternary hardware can overcome the lack of adoption and replace the binary hardware that is currently in use.
Whats Next
To get a better insight whether this different approach of employing a DAG based distributed ledger can compete with its competitors for the adoption in the IoT industry and if the project brought any revolutionary change into the cryptoeconomy, we have to evaluate the history of the project and its founders, what essential role JINN tokens played in the formation of IOTA and how the tokens are distributed. After that we will dive deep into the promises of IOTA’s technology, its current practical limitations, the future roadmap and what our opinion on the success of the IOTA protocol will be. All these topics will be revealed in the next articles of this series.

Editor’s Note
At Konfid.io we composed a detailed report about the IOTA project for which we provide a condensed but informative four-part summary on Medium, aimed to give an overview about IOTA for entrepreneurs and companies that are planning to build on the protocol, as well as for developers and crypto-enthusiasts that are interested in the Tangle.
What is Konfid.io?
Konfid.io is a technology consultancy and venture studio based in Berlin that focuses on Blockchain technology to build decentralized applications in private as well as public distributed systems. We constantly research the practical usability of distributed ledger projects and like to share our findings with the wider community.
Hi! I am a robot. I just upvoted you! I found similar content that readers might be interested in:
https://medium.com/konfid-io-blockchain-reports/iota-report-decoding-the-tangle-part-1-a7705c458583