After a few minutes of thinking about the subject I was going to talk about, I had an idea. Before I was working on a software project that included connecting via the Tor network and then the VPN, to avoid tracking and spaming users as well as data transmitted over the Internet, Arab network on this giant network (I mean here the Tor network and not the VPN networks) is very little compared to its widespread use and its high security value. Let this be the subject of the post.

On the blessing of God we first begin by defining the Tor network

Tor developers have been working on a clear goal of "anonymity, privacy and security" for Internet users, where the program connects users to the network, which consists of a set of servers called "nodes" - we come to define it next - and are interconnected in the form of a network And the process of communication through these nodes to get full privacy and ensure users against every trace of their movements on the Internet and the sites they visit and protects them from attempts to trace, identify and spy, which can be carried out by several individuals, companies or governments, Or saved Service (ie the company that provides us with contact to the internet service, for example, Maroc Telecom -mthal not more-).
Second, how does the Tor network work?
The Tor network works in a simple and easily understandable way but at the same time very professional - at the technical level - by sending caller data across three servers before reaching its final destination. These servers are called when connected to the ring and are within the Tor network.
As mentioned earlier in the first axis, the Tor network servers are called nodes. It should be noted here that the first two nodes pass the data called "bridges" while the last node is called the "exit node." These are the most important concepts that you should understand well to use the network And use them to the fullest extent possible.
The difference between these two types of nodes is that the data is exchanged between the caller and the bridges in an encrypted manner, and its role - ie bridges - is limited to passing the data encrypted as it is without decrypting (bridges originally not intended for decoding and not being involved). When an outbound node disassembles its content to send to its final destination, which is the user's contact (eg, the professional site).
To clarify more about the contract - the servers used in Tor -, I note that this contract is chosen by the Tor network randomly to connect and transfer data and in each connection process there are 3 nodes: node access, middle node, exit node, The Internet user knows of the sites and services he visits, as these sites are also prevented from knowing the real location of the user - I mean here the real geographical location -.
Here I try to explain all these words in one picture:
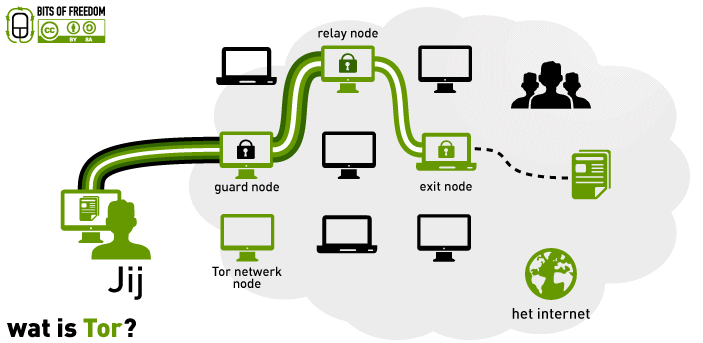
And these types with a more simplified explanation:
Login node: A server connected directly to you and knowing your location, but does not know what data is being sent because it is encrypted before it is accessed - it is encrypted by the Tor program before sending it.
Central node: This is a server connected to the node of entry and exit node, which does not know any information about you, and does not know the data that is sent or received by you (not your geographical location, nor the data you sent, nor the site you are visiting) It must receive data from the access node, and pass it to the exit node.
Outbound node: This is the last server in the string. The Tor network ends up creating another connection, decrypts the data and passes it to the site (or whatever), so the node identifies the site you want to visit and the data you send to the site . However, if you use the Tor network while visiting a site that supports HTTPS encryption (for example: https://google.com), this node can only know the location you want to visit, while the data is decrypted within the site you have visited (for accuracy: The site is disassembled, not the site in its usual sense).
To further expand on this subject, in theory and conceptualization, here are quick links:
And I refer you, my dear reader, to the rest of the references in the links above for further elaboration.
Important alert
For this last node, you must be cautious about it, if your destination - the site you are visiting - does not use a secure connection supported by a trusted encryption certificate (ie, using a prefix called https), you should pay attention when sending or receiving sensitive data , And take the necessary action.
I always make sure that you use a secure connection, but it is not necessarily available, so you can use another type of encrypted connection, for example if it is a secret conversation (I do not know, maybe at the government or other level). Use encryption software for this purpose, for example using RSA encryption type, you can read about it via the following link:
RSA algorithm
In fact, I have developed a desktop program for this purpose, but it needs a lengthy explanation, and I do not want to prolong you and introduce you to another topic. So I refer you to a program that meets this purpose, OpenPGP
Official website link -For download and download-: http://openpgp.org/
Through this program you can use encryption types, or multiple encryption algorithms, personally I recommend you rsa.
Now we have finished concepts, and theoretical work, even though he needs to explain more fully, but Uncle Google in debt
Download the supplies
The first thing to start with is to download the Tor network operating system.
It is simple and easy indeed, and does not require any technical knowledge - in principle -.
For information, this phase will be divided into two parts, the first for desktops and tablets and the second for smartphones.
For the first part, ie, the computer - and the issue - the file you will download is located on the official website of the Tor network on the following link:
Https://www.torproject.org/download/download.html.en

I am a dedicated Tor user for a couple of years now. People need to get used to the browser, especially the network speed. I recommend adding another layer of protection by using VPN too to make it even more robust.
yes i think so, thanks for your comment
Information is not knowledge.
- Albert Einstein