Next time someone tells you that connecting to STEEM is complicated, tell him the story of the man in the middle (MitM attack).
 pxfuel (Creative Commons Zero - CC0) modified
pxfuel (Creative Commons Zero - CC0) modified Context
By the end of 2019, the number of worldwide email users increased to over 2.9 billion with an average of 246.5 billion of Emails Sent/Received Per Day.
source: Email-Statistics-Report-2015-2019-Executive-Summary.pdf
 Image Courtesy: Pixabay
Image Courtesy: Pixabay That gives us an average of 85 emails received per day per account! An ideal environment for a particular type of attack, the attack consisting of sending fake emails that appear legitimate called the fishing attack.
And I'm not talking about other ways of communication (sms, messenger...) increasing the probability of this kind of attack.
Story
The man in the middle (MitM) is someone who comes between you and the server (application) you want to connect to, for example facebook.
 piqsels (Creative Commons Zero - CC0)
piqsels (Creative Commons Zero - CC0) To do this he sets up an intermediary server, with an https address (internet address such as https://www.facebook.com for example) that is ambiguous and good enough to mislead you and send you an email, a sms... with the false link. For example, like this one https://www.facebook.com.my.hacking.server.com/login/ where you think you're going to facebook while you're going to my.hacking.server.com.
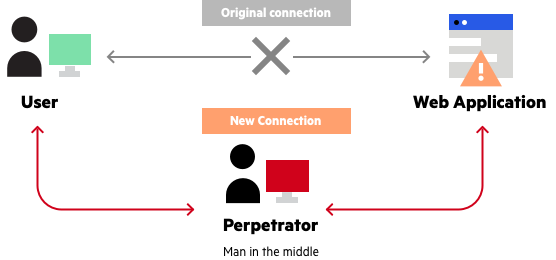
But it doesn't stop there, with a real-time copy script of the original login page (real-time web scraping) his page is always up to date. Making it even harder to tell the difference between real and fake login pages.
The wrong good idea
Ok, you tell yourself that you'll never be stupid enough to be fooled, besides you're not stupid anyway, you've enabled 2 factor authentication (Google authenticator or SMS) so nothing can happen to you!
And here's the nice wrong good idea, the attacker's server being in the middle (relay server) what will happen if you have configured 2 factor authentication?
It's simple, the attacker's server will make a connection request as if it were you on the genuine server, so the genuine server will ask for 2 factor authentication that the attacker's server will immediately ask you on its fake login page and you will have lost! Game Over!
Okay, but what about STEEM in all of this?
And this is where the difficulty and complexity of connecting to the different Steem apps becomes an asset!
It's so difficult to memorize the different keys and annoying to try to type them on the keyboard each time that the best way to connect to Steem apps is to use an encrypted password manager (like LastPass, Dashlane...), which recognizes only the genuine servers to propose you to use your login/password on them. Another way is to use the Steem Keychain extension where the login process is local to your machine or SteemConnect.
 PCmag: the best password managers
PCmag: the best password managers So the next time you want to convert someone to come on STEEM and he'll tell you:
No it's too complicated to connect!
Tell him this little story ;)

If you liked this article
Feel free to let me know by
[ Upvote | Resteem | Comment ]
THANKS :)
@french-tech

Statistics Update
!trdo