
We have mentioned on more than one occasion that attacks on DeFi protocols are occurring more frequently. Perhaps it does not mean that the companies behind them are not investing in security. But the ways in which they try to exploit a platform are much more precise, managing to commit the act.
In a DeFi protocol, there is a large flow of money when considering the liquidity provided by users. Perhaps it is similar to the focus on DEX, where there is also a significant volume to consider. It is clear that the cyber attackers' main targets are these two mentioned.
Today we will talk about a new case of exploitation that the security firm Cyvers has reported and followed through social media. Before that, I would like to address one of the precedents that occurred this year in similar situations.
In mid-July, the DeFi protocol Li.Fi was hacked. At that time, the blockchain security firm called Certik estimated that around $11 million had been stolen. The explanation given was that some users made a manual configuration of their accounts, allowing the perpetrators to use an exploit. In this case, the cybercriminals singled out certain users of the Li.Fi platform to commit the crime.
There was also mention of one of the wallets involved, which led to the loss of approximately $6 million in ETH, along with several stablecoins that also represented a significant value collectively.
After the incident, the DeFi company Li.Fi reported that the attack had been contained and that the necessary measures would be taken to resolve the disaster. It was also communicated that the incident affected a smart contract, which was later somehow deactivated.
In this case, the procedure is to report the case to the relevant authorities and connect with external companies responsible for tracking the funds. Fortunately, only a small number of users have suffered this attack, although it is regrettable that it happened.

On the other hand, urge users to revoke permissions from accounts that are believed to have been compromised. In this case, it could be a matter of prevention, or truly an action to avoid a greater harm.
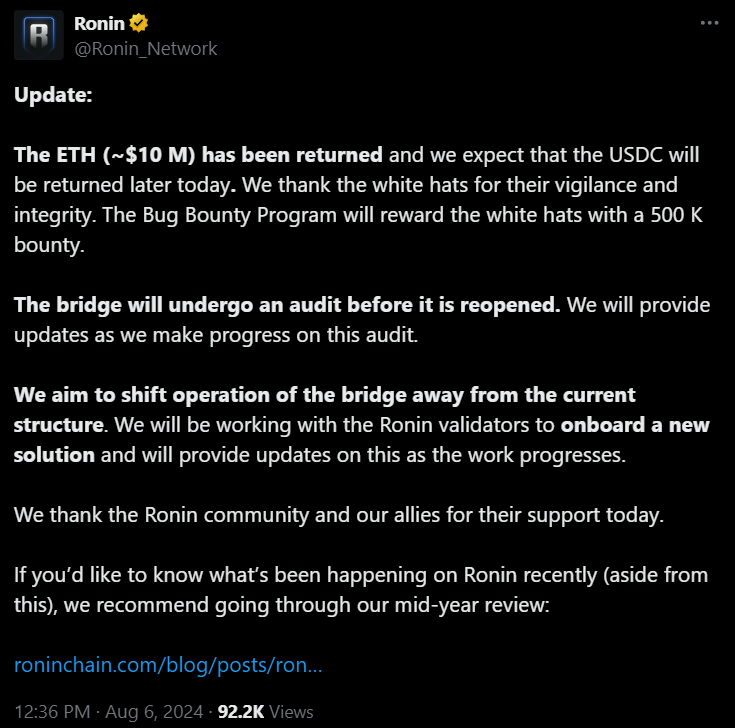
Another background or situation in which a platform was attacked was in August, where the Ronin bridge, which connects Ethereum with the Ronin sidechain, had fallen victim to an "MEV exploit".
At that time, the loss amounted to a total of $12 million (4,000 ETH and $2 million in USDC). The good news is that it was reported that a group of ethical white-hat hackers had managed to recover the funds, so on one hand, ETH was quickly recovered and later the rest of the USDC to complete the total amount.
One of the heads of a security company mentioned that when an update occurs, the platform itself may experience points where there could be an intrusion, so every time the necessary updates are done, the necessary security measures must be implemented to prevent a new way of exploiting a connection from being found.
It is clear that the ways to breach a cryptographic system are becoming increasingly sophisticated. In my opinion, these incidents will continue to occur because they will never stop. I believe that there is no other solution but to implement necessary preventive measures, even if this leads to a high estimated investment by the company.
Today, news emerged regarding a new exploit; this time on the DeFi Delta Prime protocol. The cryptographic security firm Cyvers has reported detecting several transactions deemed suspicious, resulting in the loss of $5.93 million.
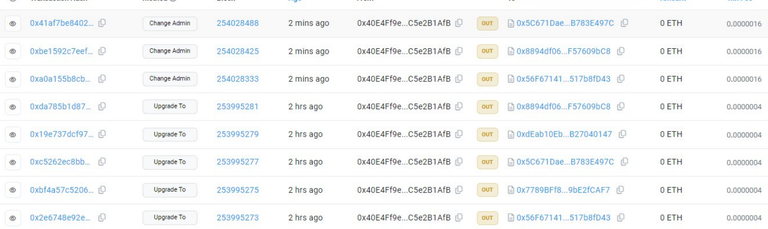
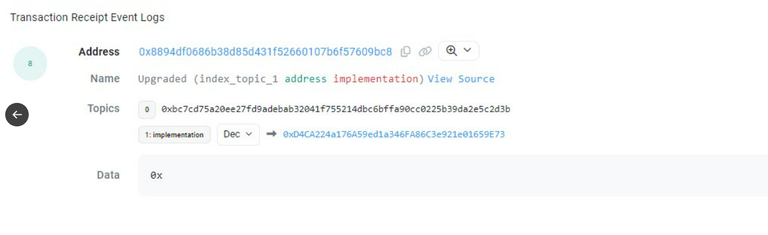
The firm has communicated that there is a possibility that the protocol administrator may have lost control of their private key, leading to cybercriminals gaining access to smart contracts after updating the proxy.
Looking at it this way, let's say that what the attackers achieved was accessing the smart contracts and manipulating their function to accept their exploit. Thus, they managed to drain several liquidity funds that included DPUSDC, DPARB, and DPBTCb.
Subsequently, it was discovered that one of the suspicious addresses was converting USDC to Ethereum, suggesting that in other attacks, the attackers had the same preference for convertibility.

Will it be a rather untimely oversight? An error that could have been avoided? The truth is that no matter how we make mistakes, there will always be someone willing to take advantage of the opportunity to breach a system and achieve their goal. The problem is that many users will regret it, and in addition to their losses, the trust and reputation of a particular protocol would collapse in a matter of seconds.

- Main image created using Ideogram (AI) and edited in Canva.
- I have consulted information in decrypt.co: I, II and III
- I have used Hive Translator to translate from Spanish to English.
Posted Using InLeo Alpha
La vulnerabilidad de los sistemas.
Gracias por tu explicación.
!HUESO
!LUV