Analysis of @hivesurvey surveys
VERDICT: at the moment it does not seem to be a security threat for Hive users.
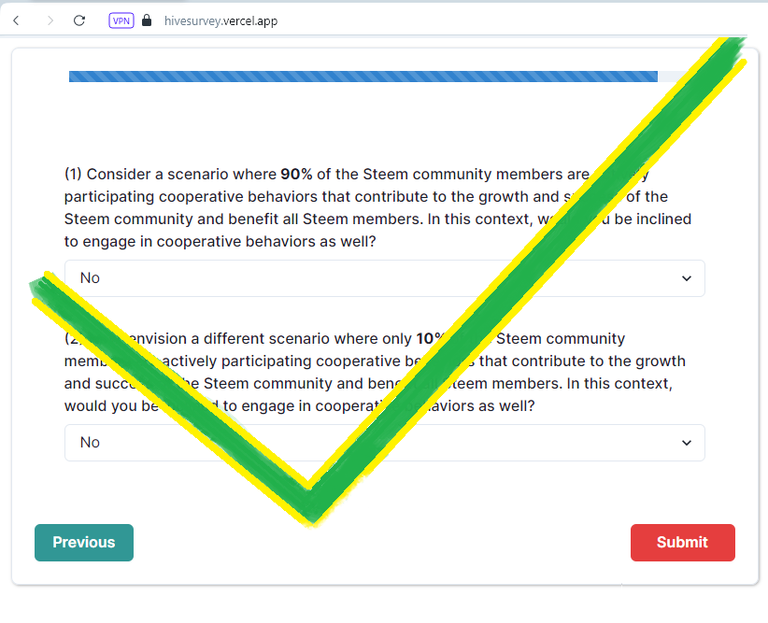
If you saw this post that warned you against this Survey before I had a chance to edit it after about 10 minutes, my apologies. I am feeling a bit after the weather today so I rushed to conclusions.
Follow below the RED FLAGS that initially brought me to think that it was just another phishing wave.
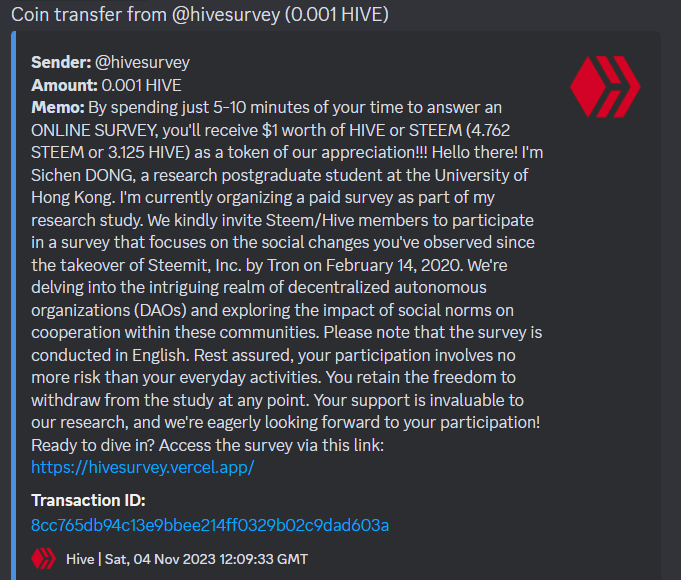
WALLET SPAM
The initial warning was triggered because it's sent with wallet spam that looks like this:
2. FREE MONEY
They are promising you $ 1 to complete a brief survey.
They seem to have kept their word though.
As @themarkymark said: they have been paying users, and they bought stake. It's basically asking questions about the Justin Sun take over. You can view the questions without logging in.
PS. The payments stopped briefly after this comment.
3. OUT OF NOWHERE
As @louis88 said:
- Why do massive spam
- No Introduction Post
- Why use a shady Vercel Application
- No details to the person behind it.
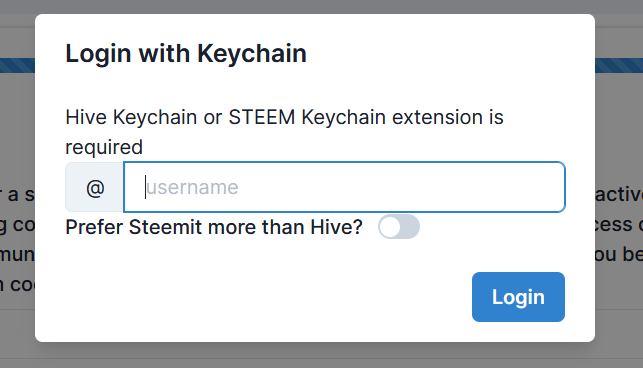
4. ACTIVE KEY LOGIN
Another red flag was that it asks for your ACTIVE KEY to login (with Hive Keychain). That is suspicious as usually the posting key is enough.
It also sends username and active key to their server but the latter is actually the PUBLIC active key, so not a threat.
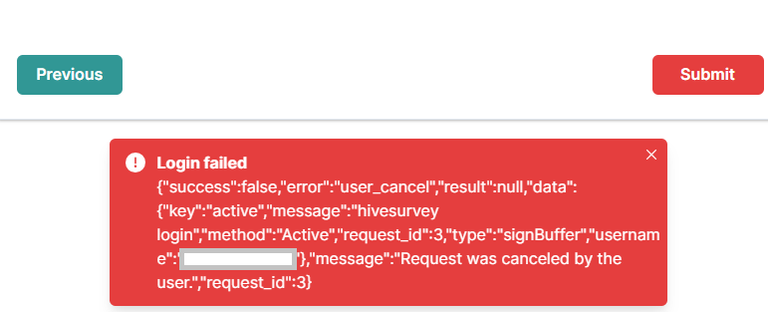
NOTE: I originally thought it was the private key, but clearly that's not accessible to the website when you login with the Hive Keychain.
Their code responsible for submitting the survey looks like this:
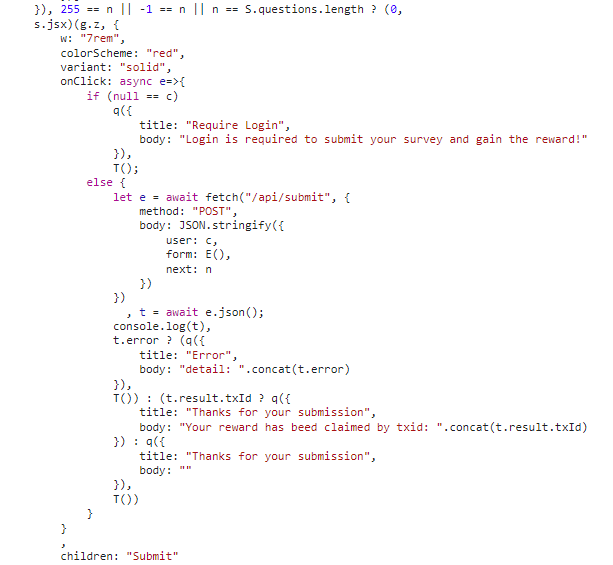
This code is easily readable, but other scripts are not so I submitted some parts to ChatGPT and it helped me understand those parts better.
There does not seem to be any threats currently in place.
FINAL CONSIDERATIONS:
I would still advise to keep an eye on this domain and use some healthy skepticism.
My concern is that this could spread fast because of the promised payouts, and once many users are on it because they heard it's legit, the owner could change the login mechanism to ask for private keys instead.
DO YOUR PART
If the scenario described above still ends up occurring (unlikely since the payments stopped), please use my !phishing command anywhere on chain followed by the phishing url of the website.
Eg.
@keys-defender !PHISHING https://somesketchysite.com
What this does is scan all new blocks and all blocks generated in the previous hour to detect such link and warn users that came across it by using wallet memos or replies with a warning.
This command can be used anytime you see a phishing link, you can use it anywhere (posts/comments). If you can't remember this command (or the others) just tag @keys-defender for a list of all commands.
If you are a top-40 witness, the !phishing command will immediately add the phishing link to @keys-defender database. If you're not a top-40 witness, 3 different reports from users with reputation above 50 are required for the blacklist command automation to work.
STAY SAFE!
@keys-defender
play-to-earn WEB3 Shooter on HIVE


Discord Twitter

@keys-defender !PHISHING https://ja.cat/sexae
Thank you for your report, entry added to @keys-defender's database "PHISHING".
Thanks!