
Hackers have numerous ways to hack a website, I have collected most popular ways of how Hackers hack a website.This is totally my own personal opinions.
Be sure read each Point carefully cause who knows this article might show some flaws in your companies website or if you want make a website be sure to keep these points in your mind while creating it.
Hackers can hack a website by Click jacking Attacks.

This is a malicious technique used by hackers to trick a Web user into clicking on something different from what the user wants to click on and once they click on it they potentially reveal their confidential information and hackers can even take control of their computer. It is a browser security issue that is a vulnerability across a variety of browsers and platforms. A clickjack attack takes the form of embedded code or a script that can execute without the user's knowledge,The user mistakenly just has to click the button that appears to perform another function and once clicked it will start running the embeded code that user isn't even aware of .
SQL Injection Attacks are one of the most popular ways of hacking
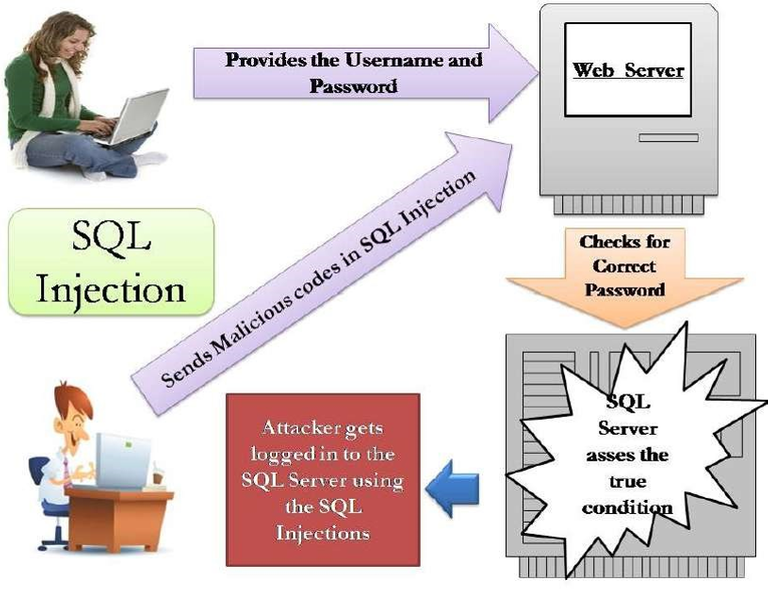
The point of an SQL Injection attack is to compromise a database, which is an organized collection of data and supporting data structures. The data can include user names, passwords, text, etc.
Injection Attacking occurs when there are flaws in your SQL Database, SQL libraries, or even the operating system itself. Employees open seemingly credible files with hidden commands, or “injections”, unknowingly.
What makes injection attacks particularly scary is that their attack surface is enormous. Injection attacks are a very well understood vulnerability class, meaning that that there are countless freely available and reliable tools that will even allow an inexperienced hacker to abuse these vulnerabilities automatically, which is very scary.
Cross Site Scripting Attacks
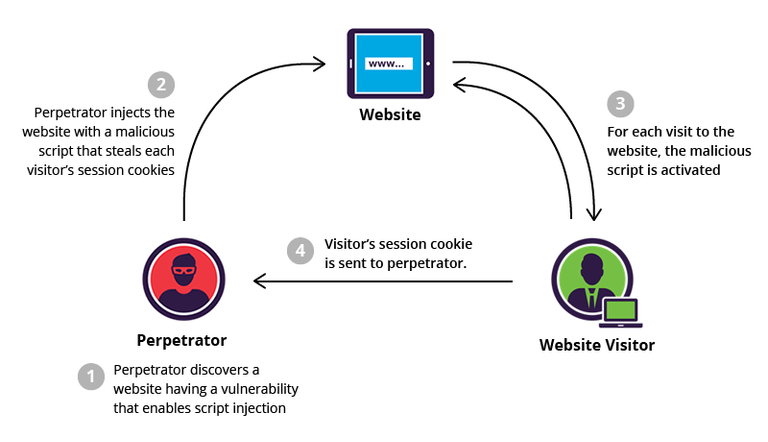
Cross-Site Scripting (XSS) attacks are a type of injection, in which malicious scripts are injected into websites , it is also known as an XSS attack, An attacker can use XSS to send a malicious script to an unsuspecting user in the form of file packet to the web browser window and it bypasses the validation process. Once an XSS script is triggered it will execute the script cause computer thinks that it came from a trusted source, it’s deceptive property makes users believe that the compromised page of a specific website is legitimate.These scripts have the ability to manupulate the content of the HTML page of a website.
DNS Spoofing
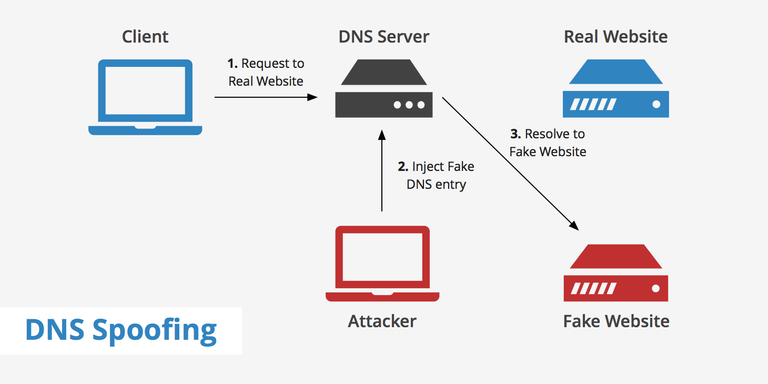
It is also known as DNS cache poisoning, is a form of computer security hacking in which hackers can identify vulnerabilities in a domain name system, which causes diversion of traffic from legit servers to a fake website or server. causing the name server to return an incorrect IP address.
The reason why DNS poisoning is so dangerous is because it can spread from one DNS server to anathor DNS server. Once a DNS poisoning attack resulted in the compromising of Great Firewall of China temporarily escaping China’s national borders.
Social Engineering Attacks

Social Engineering Attacks uses psychological manipulation to trick users into making security mistakes or giving away sensitive information.
Social engineering attacks have many different steps. A attacker first investigates the intended victim to gather necessary background information of him, such as potential points of entry and weak security protocols, needed to proceed with the attack. Then, the attacker moves to gain the victim’s trust that break security practices, such as revealing sensitive information or granting access to critical resources
Best example of a social engineering attack is the " tech support" scam.
This is when someone from a call center who pretends to be a tech support member who says that "your computer is infected and it is will eventually slow down your computer",He talks in a certain way that manipulates the victim to believe in the lies of the attacker and then he will say that the problem can easily be fixed at a certain cost.
Symlinking Attack
Symlink attack is one of the newest and easiest way of exploitation as the Hacker/Attacker can get full root access to the entire server from a compromised website and if the server is in a shared environment then hackers tend to attack more websites as it is linked to other servers which means the attackers can manipulate a ton of data
CSRF Attacks
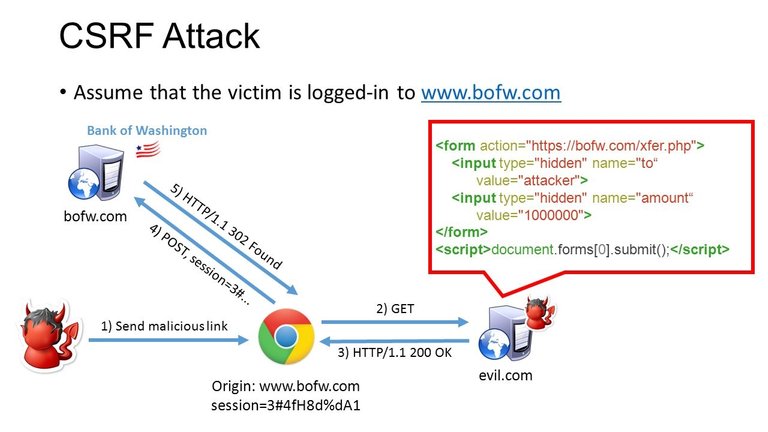
CSRF - Cross-site request forgery it is also known as one-click attack. is an attack that forces an end user to execute unwanted actions on a web application in which they're currently authenticated, in simple words It is a type of malicious exploit of a website where unauthorized commands are transmitted from a user that the web application trusts.
A successful Cross-site request forgery attack can force the user to perform dynamic changing requests like transferring funds, changing their email address, and so on. If the victim is an administrative account, Cross-site request forgery can compromise the entire web application.
RCE Attacks
RCE- Remote code execution, It is the ability an attacker to have access to someone else's computing device and make changes to it , no matter where the device is geographically located. A REC attack is a result of either server side or client side security weaknesses.
Attackers tries to find vulnerabilities and once they find them they will try to execute malicious code and take complete control of the system with the administrative privileges of the user running the application.
DDoS Attack

DDoS - Distributed Denial Of Service Attack, It is the most popular and deadly attack that hackers use. it is an attack in which multiple computer systems are compromised and are made to attack a target, such as a server or website and cause a denial of service for users of the targeted resource. The flood of incoming messages, connection requests or malformed packets to the target system forces it to slow down or even crash and shut down the entire server, Basically the attackers send a lot of traffic to a server or a website and the load for the server is too much for it and it can't handle such traffic which finally causes crashing down of server.
Thank you for reading my article. if you have any quires let me know in the comments section and don't forget to upvote the article.
I also upload Latest movies and funny videos on Dtube. You can check them at
don't forget to follow me if you want see more interesting articles and videos.
@originalworks
The @OriginalWorks bot has upvoted and checked this post!
Some similarity seems to be present here:
https://defencely.com/blog/10-popular-ways-hackers-hack-website/
This is an early BETA version. If you cited this source, then ignore this message! Reply if you feel this is an error.
This is an error . even though the topic headings are somewhat similar but the content is different and genuine
Not bad
Thank you
Nice article.
Thank you