
Blockchain and decentralization have become synonyms in the cryptocurrency industry. The use of blockchain technology made it possible to create a network where all users are equal, and information is distributed over a countless number of computers in the world. Decentralization has gained a particular value for banks and other commercial institutions, since it brings a new dimension to the concepts of security and transparency.
A study conducted in February 2018 by Professor Emin Gün Sirer demonstrated that Ethereum is much more distributed than Bitcoin with nodes better spread out around the world. This results in the Ethereum network being more decentralized than its elder brother.
Well, “more” doesn’t necessarily mean “absolutely”. Is Ethereum 100 percent decentralized, anyway? This question has been frequently raised by the community and developers over the past two years.
There are a lot of reasons supporting the argument, and many which are against it One such reason could be the manipulation of commissions within the network caused by the massive launch of the CryptoKitties online game, which turned characteristics as decentralization into a myth. Cointelegraph offers you either to confirm or disprove this and six more myths about Ethereum decentralization.
Myth 1: Decentralization means distribution
To better understand what decentralization means in the Ethereum blockchain environment let’s refer to the concept as described by the network’s founder Vitalik Buterin. On his Medium post, he expressed many important thoughts about the need for decentralization and the ways to achieve it:
“Decentralization” is one of the words that is used in the cryptoeconomics space the most frequently, and is often even viewed as a blockchain’s entire raison d’être”
Vitalik states that decentralization is one of the fundamental concepts in blockchain, which is essential for protecting the networks from such problems as faults, attacks, and collusions. Although “thousands of hours of research” and development are aimed at achieving and improving decentralization, the exact meaning of the term is still unclear.
Vitalik cites the example of the “completely unhelpful, but unfortunately all too common diagram” of decentralization, which has spread among users and even developers. Whereas the last two images should obviously be reversed since "decentralization means that none of the nodes has the ability to control the processing of all transactions on the network."
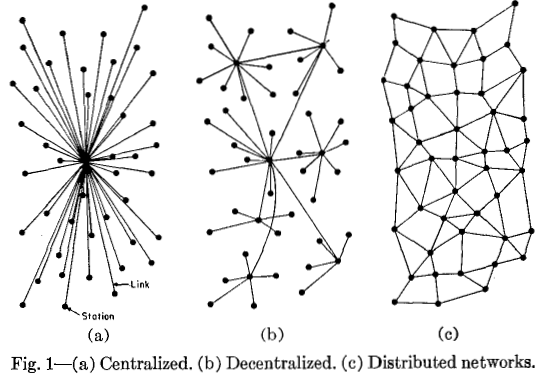
Myth 1: Decentralization means distribution
Image source: Vitalik Buterin Medium Post
Myth 2: Blockchain is resistant to errors
Myth 2: Blockchain is resistant to errors
What are we supposed to do, if even developers themselves are confused about the definition of decentralization? To clarify the ambiguity, Buterin created his own classification, which can be used to determine whether a network is centralized or not.
Myth 2: Blockchain is resistant to errors
Image source: Vitalik Buterin Medium Post
Architectural decentralization is based on the amount of physical computers in a system. The more the number of those computers it can tolerate breaking down at any single time is, the stronger its decentralization is.
Political decentralization refers to the share of individuals or organizations ultimately controlling the computers that the system is made up of.
Logical decentralization is identified according to the interface and data structures form which can look more like a single monolithic object, or an amorphous swarm. One simple heuristic is: if you cut the system in half, including both providers and users, will both halves continue to fully operate as independent units?
Often, architectural centralization leads to a political one, although in computerized communities this can be avoided. The same cannot be said for logical centralization, which in turn makes it difficult to form an architectural and political decentralization.
Myth 3: The Ethereum network is protected against attacks
Myth 3: The Ethereum network is protected against attacks
What makes the network decentralized? These are three essential components that constitute the foundation of this unique characteristic. If at least one of them works incorrectly, the system can be turned into a centralized entity:
Fault tolerance — decentralized systems are less likely to fail accidentally because they rely on many separate components that are not likely to fail.
Attack resistance — decentralized systems are more expensive to attack and destroy or manipulate because they lack sensitive central points that can be attacked at much lower cost than the economic size of the surrounding system.
Collusion resistance — it is much harder for participants in decentralized systems to collude to act in ways that benefit them at the expense of other participants, whereas the leaderships of corporations and governments collude in ways that benefit themselves but harm less well-coordinated citizens, customers, employees and the general public all the time.
It may seem that everything is simple - but at the protocol level, the situation looks somewhat different. For example, fault tolerance is useless if for some reason a large number of component computers fail to process the blocks at once.
Vitalik Buterin cites an example from real life:
“Sure, four jet engines are less likely to fail than one jet engine, but what if all four engines were made in the same factory, and a fault was introduced in all four by the same rogue employee?”
Myth 4: The Ethereum network is resistant to attacks
Myth 4: The Ethereum network is resistant to attacks
Attack resistance works much better in systems based on the Proof of Stake (PoS) algorithm, rather than Proof of Work (PoW), which the entire Ethereum blockchain operates on. This is one of the reasons why the Ethereum foundation is switching to PoS this year.
The fact that Ethereum is vulnerable to attacks became known in September 2016, when a series of Distributed Denial of Service (DDoS) attacks led to a significant delay in the operation of the nodes.
That time, despite the release of a series of Geth updates including “What else should we rewrite?”, “Come at me Bro (1.4.15)” and “Poolaid (v1.4.17),” the Ethereum developers failed to handle the DDoS attacks. The situation was supposed to be remedied by the release of the several Ethereum Improvement Proposals (EIPs):
Some of the highlighted EIPs that describe the protocol changes implemented in this hard fork, include EIP 155: Replay attack protection which prevents transactions from one Ethereum chain from being re-broadcasted on an alternative chain; EIP 160: EXP that adjusts the price of ‘EXP’ opcode so it balances with the computational complexity of the operation; EIP 161: which makes it possible to remove a large number of empty accounts that were put in the state at very low cost as a result of earlier DoS attacks; and EIP 170 for contract code size limit.
However, in early October 2017, the new Ropsten network underwent new attacks. Ironically, at that moment it was being used for testing the new Ethereum Byzantium update code supposed to prevent DDoS attacks by means of increasing the gas costs of opcodes.
Myth 5: Pools collusion is impossible
Myth 5: Pools collusion is impossible
No one seems to deal with the solo mining of Ether today – users combine into large and small mining pools. This special threat to decentralization is posed by larger ones, since they manage the capacities of all the miners connected to them.
For example, pool operators can include in the generated blocks only those transactions which they are interested in processing. Therefore, one of the goals of the modern mining which many pools have today is to provide the distributed generation of blocks.
In the current environment, 60 to 70 percent of the total hashrate of the network belongs to just four or five of the most popular pools. This applies to almost any cryptocurrency where its complexity has already outgrown certain limits, making solo mining impossible. As a result, pool owners influence the policy of the network as a whole.
Myth 5: Pools collusion is impossible
Image source: Etherscan
Until recently, the risk of full centralization of mining seemed far and far-fetched. But in 2017, Dr. Loi Luu expressed the opinion that the situation is more dangerous than it seems to be, and decentralization measures should be taken as soon as possible.
Myth 6: Wallet owners have private access to their funds
Myth 6: Wallet owners have private access to their funds
One of the features of cryptocurrencies is that no one can make any transactions with the funds that do not belong to them. In most tokenized systems, this is done through the following scheme: each of the transactors should have the ability to allow the operation to be performed so that it can meet the requirements of the previous transactor. This implies having the right private key and allows avoiding double transactions or theft.
Ethereum has a full-fledged version of smart contracts. A smart contract is a program executed once the transaction starts. In addition, it is the main "building material" for the creation of any decentralized application (dApps).
The technology of smart contracts has many advantages in terms of security and convenience, with the exception of one crucial drawback. Holders of digital wallets can not be considered sole owners of their funds - the custodians are the contracts themselves, which contradicts the original principles of cryptocurrency.
Theoretically, a running contract can perform any actions without the user's permission. Though it’s always possible to check the correctness of actions through the open source code, not everyone can do this. This problem could be solved by means of creation and use of only one contract for auditing, but for the time being nobody implemented it.
On May 18, the NEO platform reported that it collided with the vulnerability of smart contracts:
A Statement on Storage Injection Vulnerability. https://t.co/CksTyaxn3I
— NEO Smart Economy (@NEO_Blockchain) May 18, 2018
As it turned out, hackers could perform any actions with tokens - for example increasing or decreasing the displayed amount and burning coins - using only one parameter of the smart contract. Actually, the developers managed to calm down the community by stating that the real state of the blockchain wasn’t affected.
A similar situation happened to the OKEx exchange, which on April 25 suspended all ERC20 tokens deposits after the discovery of a new smart contract bug connected with the vulnerability of the batchOverflow parameter:
By exploiting the bug, attackers can generate an extremely large amount of tokens, and deposit them into a normal address. This makes many of the ERC20 tokens vulnerable to price manipulations of the attackers.

Myth 7: Manipulating network settings is impossible
In late 2017, the CryptoKitties online game took more than 13 percenthttps://cointelegraph.com/news/cryptokitties-becomes-largest-ethereum-based-decentralized-applicationof all Ethereum traffic, having received the title of "Ethereum’s Killer App"https://cointelegraph.com/news/cryptokitties-sales-hit-12-million-could-be-ethereums-killer-app-after-all. Such popularity was brought to the DApp by the simple and at the same time unordinary functionality of allowing users to breed different virtual cats and get the offspring. The more unique offspring is, the higher the reward is given to its owner. Characteristics are countless, so each pet is different from the others.
Myth 7: Manipulating network settings is impossible
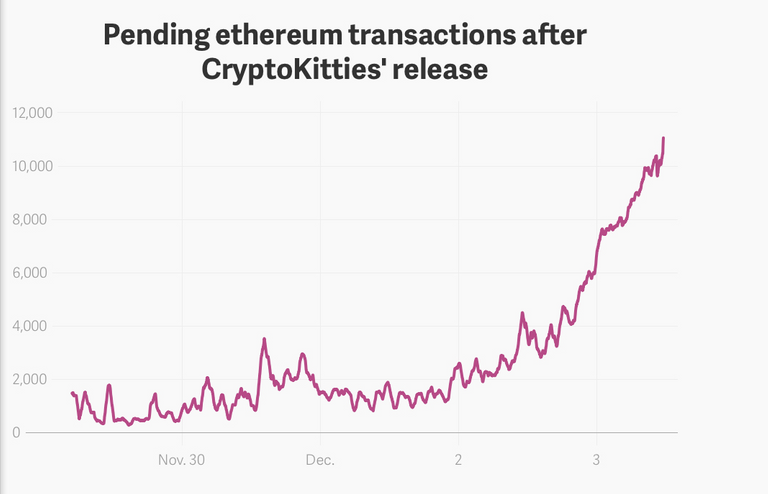
Image source: TheAtlas
But what's wrong with CryptoKitties and other applications of this kind? First, the huge demand for cats increased the queue of transactions waiting for being included in the block. At the same time, pet owners in pursuit of high priority paid several times higher commission. This increased the network fee for the rest of the network users, creating huge “traffic jams”https://cointelegraph.com/news/cryptokitties-receives-12-mln-in-funding-from-big-name-investors of unprocessed transactions.
Secondly, the prices occured to be uncontrolled. If immediately after the app release one cat cost about $2 in ETH, just within a month the price reached $10, and in 2 months – $25, with up to $113,000https://techcrunch.com/2017/12/03/people-have-spent-over-1m-buying-virtual-cats-on-the-ethereum-blockchain/ paid for one kitten. Isn’t it a good manipulation?
The potential threat of such applications cannot be underestimated. Developers fully control both the game and running smart contracts. Cats are gradually growing in price, and each contract can be suspended at any time. According to developers, this is a security measure in the event of hacking one of the three management accounts owned by the team. However, the holder of the main account key is able to freeze the entire game and, consequently, all the users’ accounts. Finally, the smart contract, responsible for the characteristics of the kittens, is allowed to be modified by the developers and has a closed code.
Some users compare~~~ embed:ethereum/comments/7jmk4s/crypto_kitties_is_a_pyramid_scam/ this game with a pyramid. A new zero-generation cat appears every fifteen minutes, and its price equals the average cost of the last five cats sold plus a 50 percent surcharge. The higher the generation is, the slower pets are reproduced. Zero-generation kittens belonging to developers are the most expensive. By selling all produced animals, developers can earn an income of over 2.2 mln ETH - and this amount doesn’t include commission for every action like mating and selling. reddit metadata:fGV0aGVyZXVtfGh0dHBzOi8vd3d3LnJlZGRpdC5jb20vci9ldGhlcmV1bS9jb21tZW50cy83am1rNHMvY3J5cHRvX2tpdHRpZXNfaXNfYV9weXJhbWlkX3NjYW0vIHRoaXMgZ2FtZSB3aXRoIGEgcHlyYW1pZC4gQSBuZXcgemVyby1nZW5lcmF0aW9uIGNhdCBhcHBlYXJzIGV2ZXJ5IGZpZnRlZW4gbWludXRlcywgYW5kIGl0cyBwcmljZSBlcXVhbHMgdGhlIGF2ZXJhZ2UgY29zdCBvZiB0aGUgbGFzdCBmaXZlIGNhdHMgc29sZCBwbHVzIGEgNTAgcGVyY2VudCBzdXJjaGFyZ2UuIFRoZSBoaWdoZXIgdGhlIGdlbmVyYXRpb24gaXMsIHRoZSBzbG93ZXIgcGV0cyBhcmUgcmVwcm9kdWNlZC4gWmVyby1nZW5lcmF0aW9uIGtpdHRlbnMgYmVsb25naW5nIHRvIGRldmVsb3BlcnMgYXJlIHRoZSBtb3N0IGV4cGVuc2l2ZS4gQnkgc2VsbGluZyBhbGwgcHJvZHVjZWQgYW5pbWFscywgZGV2ZWxvcGVycyBjYW4gZWFybiBhbiBpbmNvbWUgb2Ygb3ZlciAyLjIgbWxuIEVUSCAtIGFuZCB0aGlzIGFtb3VudCBkb2VzbuKAmXQgaW5jbHVkZSBjb21taXNzaW9uIGZvciBldmVyeSBhY3Rpb24gbGlrZSBtYXRpbmcgYW5kIHNlbGxpbmcufA== ~~~
It cannot be said that the popularity of CryptoKitties paralyzed the Ethereum network, but definitely it made its operation much more complicated, with prices getting expensive and transactions congesting the blockchain. It is still unknown how this will end, but if the number of breeding-type applications will grow, the decentralization of Ethereum may come under serious attack.
Myth or not?
Decentralization is an integral part of any cryptocurrency. However, the numerous flaws resurfacing as the Ethereum blockchain continues to be used in different conditions, confirm that the network is not 100 percent decentralized. There is still a lot of work to be done for elimination of centralizing factors. The most difficult part of this would be creating incentive conditions for those who build the decentralization - miners and validators. One of such highly anticipated updates is Casperhttps://cointelegraph.com/news/casper-what-is-known-about-the-new-ethereums-network-upgrade, which is scheduled for the summer-autumn of this year.
"The decentralisation unicorn, does it really exist? 90 % of the mining power is owned by 16 miners in Bitcoin and 11 in Ethereum." - Emin Gun Sirer, Associate Professor @Cornell #genesislondon pic.twitter.com/CiHCIA3FsS
— Dolfin (@DolfinHQ) February 22, 2018
Is decentralization only a myth or are inevitable changes necessary? It is not a surprise that Cornell professor Emin Gün Sirerhttps://cointelegraph.com/tags/emin-g%C3%BCn-sirer compared it to unicorns - they are beautiful, everyone would like to believe in them, but logic does not allow.