A Simplified Explanation of 802.11r
What is 802.11r and Why Do I Care?
802.11 is a protocol suite that describes how wireless networks operate. You may be familiar with 802.11a, 802.11b, 802.11g, 802.11n, and 802.11ac which are the overarching standards, but you are probably less familiar with some of the underlying protocols that make up each standard. One of these underlying protocols is 802.11r which explains how Fast Transitions happen within an Extended Service Set. I'm going to explain what 802.11r is all about, but first, let's get some definitions out of the way.
Basic Service Set (BSS) - A BSS is the basic building block of an 802.11 wireless LAN. It consists of a single wireless access point and any stations that are connected to that access point. All operating parameters such as operating frequency, operating channel, and supported data rates are defined by the access point. The simplest BSS consists of a single access point and a single station, but a BSS may also consist of a single access point and many connected stations. Stations communicate only with the AP that they are connected to, and all traffic within the BSS flows through the access point. Typically, the BSS is identified by the MAC address of the access point.
Extended Service Set (ESS) - In an infrastructure wireless LAN an ESS consists of one or more Basic Service Sets all operating as a single logical network. Devices connected to the same ESS can communicate with one another and may roam between different BSS's within the ESS. An ESS is identified by the Service Set Identifier (SSID).
When a station roams, data connectivity is lost which can cause latency, dropped connections, and perceived slowness of the network. The basic goal of 802.11r is to minimize the time that it takes for a wireless station to roam from one BSS to another BSS in the same ESS, thus minimizing the impact of the brief loss of data connectivity. Before we dig into exactly how 802.11r works, let's first explore how devices authenticate to a wireless network and how roaming events were handled prior to 802.11r.
Connecting to a Wireless Network
Here are the steps that a wireless client would go through to connect to a wireless network prior to 802.11r.
- Client Authentication to AP
- Authentication response from AP
- Client Association to AP
- Association Respons from AP
- 4-way handshake part 1 - AP nonce passed to Client
- 4-way handshake part 2 - Client nonce passed to AP
- Client and AP derive encryption key based on the passed nonces
- 4-way handshake part 3 - AP verifies encryption key and communicates the Group Transient key
- 4-way handshake part 4 - Client acknowledges successful encryption
Prior to 802.11r, each time that a client roamed from one BSS to another, the client would need to go through all of the aforementioned steps in order to connect to the new AP. All of this communication between the AP and client typically takes less than one second. This seems fast, but for some real-time applications such as voice and video, there will be a noticeable degradation in service. This is a problem, and this is where 802.11r comes into play.
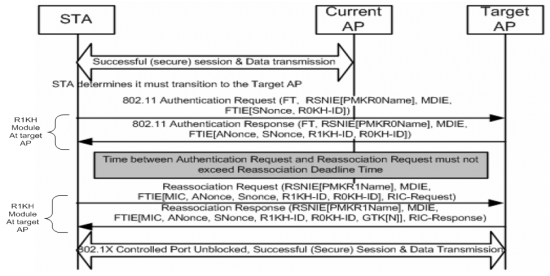
802.11 Roaming With 802.11r
Here are the steps that a wireless client would go through to roam from one BSS to another BSS with 802.11r enabled on the ESS.
- Fast Transition Authentication - includes information from the original authentication as well as the client nonce
- Fast Transition Authentication Respons - includes information from the original authentication as well as the AP nonce
- Client and AP derive encryption key based on the passed nonces
- Fast Transition re-authentication request - Client verifies encryption key
- Fast Transition re-authentication response - AP acknowledges successful decryption and the Group Transient Key.
As you can see, 802.11r simplifies the process of roaming by relying on the AP that is currently serving the client to vouch for the client when it roams to a candidate roaming AP. It doesn't seem like much, but the ability to avoid making the client and new AP perform the 4-way handshake dramatically reduces the time required for a client to roam. This makes the brief data connectivity loss imperceivable to the end user even when using real-time applications.
Please let me know if you have any comments or questions below. Thanks for reading!