Imagine a new kind of cybersecurity service that coordinates the efforts of thousands of expert researchers and ethical hackers across the planet in real-time. Bug hunters, computer scientists and penetration testers working together to eliminate security vulnerabilities before they become dangerous. Imagine that this service was so well designed that it was tailored to meet the specific needs of your company. Imagine it was so affordable it was within reach of even the smallest business.
That reality is here: it’s Uncloak’s threat bounty program.
Cyber-attacks are a fast-growing problem
Cybersecurity is now one of the most urgent issues for companies to address. Recent incidents like the Facebook, Equifax and Uber Data breaches show what devastating effects can follow from mismanagement of cybersecurity.
The common perception is that cybercrime is targeted at the big end of town, but survey data reveals that even small companies are impacted. Data released by the FBI shows that cybercrime attacks have increased by 2,370% since 2015 and the global cost is now in the billions of dollars.
Every business needs a bounty program
In 1995 the exec’s at Netscape were wrestling with a growing problem; their innovative web browser was making them a household name, but it was also attracting unwanted attention from hackers and cybercriminals. As soon as they patched one gap in their security, some hacker found a new one.
People wanted their online experience to be secure. If they thought hackers could hijack the Netscape browser and steal their data, then they would stop using it.
*A young developer had a brilliant idea; why not encourage hackers to work with us, instead of against us? Encourage them to hunt vulnerabilities in our systems and reward them for reporting them to us, rather than exploiting them for criminal purposes. *
The first “bug bounty program” was born. It was a success, and other companies were soon trying to imitate the idea, but there was a catch; managing the thousands of hackers sending in threat reports was a huge job and cost a lot of money, so only very big companies could afford to have a bounty program.
For most companies that’s how things have stayed; the first thing they know about security threats to their services is when hackers break in and hijack them.
Threat bounty programs can change that; they’re an essential part of effective cybersecurity, and they should be available to every company, big or small.
Threat bounties are the new security standard

It isn’t just software companies that need protection from cybercrime. Virtually every business relies on internet services for their daily operation, from email to stock management and marketing.
More online commerce means more data and more vulnerabilities for hackers to try and exploit.
Companies operating bug bounty programs paid more than US$7.6 million in bounties in the first half of 2018, alone. A recent Gartner report found that the high cost of operating bounty programs has kept them out of reach for most businesses.
Only 5% of companies Gartner surveyed used threat bounties as part of their cybersecurity, but the report shows that demand for threat bounty services is high. By 2022 more than 50% of companies will want to implement them, Gartner predicts.
That’s where Uncloak comes in.
Secure threat bounty protection for every business
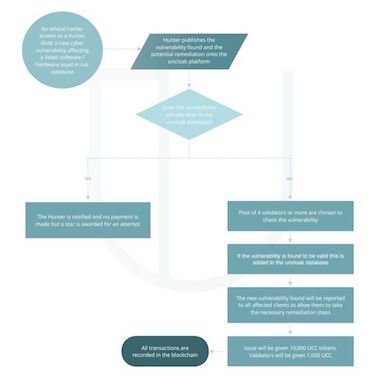
Uncloak revolutionises the threat bounty concept by integrating the work of ethical hackers and cybersecurity researchers in a Blockchain network. Instead of having a centralised monitoring system trying to verify and authenticate thousands of threat reports, the Uncloak Blockchain will compare the reports of all the hunters in the ecosystem automatically using an intelligent peer-to-peer network.
Uncloak creates a Blockchain trust environment where threat hunters can examine vulnerabilities without directly accessing companies’ sensitive data.
As well as making it faster, the efficiency of Uncloak’s intelligent Blockchain structure makes it affordable for small companies.
Both end-users and cybersecurity researchers will benefit from having up to the minute intel on new threats and solutions, and ethical hackers who identify vulnerabilities will be automatically rewarded with UCC tokens.
Who are Uncloak’s threat hunters?
Uncloak uses a comprehensive vetting system to ensure that our threat bounty hunters work in the best interests of enhanced cybersecurity. Uncloak’s threat hunters come from an ethical hacking, research and/or penetration testing background and their participation in the Blockchain platform means that all the data they contribute is cross-checked and verified by rigorous peer review.
Threat bounty hunters working in the Uncloak Blockchain will get immediate recognition for their work and companies using Uncloak will benefit from its unprecedented immediacy of protection.
Learn more about Uncloak

No business can afford to ignore the threat of cybercrime. Even small companies have contact lists and financial records that are valuable targets for attackers. Companies wondering how to do a threat bounty program can implement Uncloak affordably and rely on having a state-of-the-art solution.
Experience a demo of Uncloak right now on our website: go to https://demo.uncloak.io/
If you would like to learn more about the technical details of our unique AI/Blockchain system, please take a look at the Uncloak Whitepaper, here.
Please subscribe to our social channels to keep up with the latest Uncloak news:
● Telegram
● Twitter
● Facebook
● Reddit
● Steemit