"Hackers have managed to hijack millions of Android devices over the past few months to secretly generate Monero coins in a new "drive-by" cryptomining campaign, security researchers have discovered. According to Malwarebytes researchers, the campaign first spotted in January seems to have begun in November 2017.
In this malicious campaign, the threat actors redirect unsuspecting mobile users to dubious pages set up to perform in-browser cryptomining by exploiting their device's processing power to generate Monero coins.
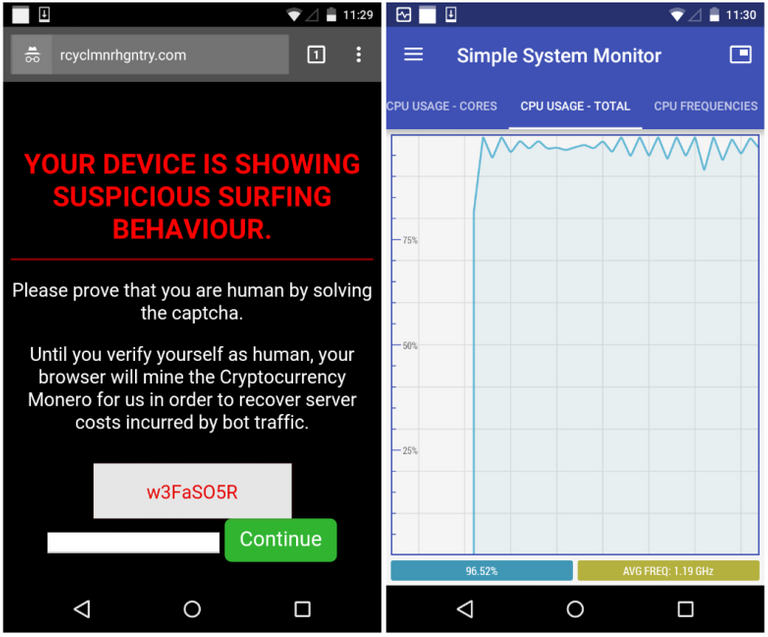
Visitors are presented with a CAPTCHA to solve to prove that they are human and not a bot.
"Your device is showing suspicious surfing behaviour. Please prove that you are human by solving the captcha. Until you verify yourself as human, your browser will mine the Cryptocurrency Monero for us in order to recover the server costs incurred by bot traffic," the warning message reads.
Until users solve the CAPTCHA code, the site runs an exhaustive cryptojacking script that exploits the phone's CPU power to mine Monero - a process that could damage the device if left running long enough.
"Until the code (w3FaSO5R) is entered and you press the Continue button, your phone or tablet will be mining Monero at full speed, maxing out the device's processor," Jerome Segura, lead malware intelligence analyst at Malwarebytes, wrote in a blog post.
Once they enter the code, users are simply redirected to the Google home page.
Researchers said victims may encounter this forced redirection during regular browsing sessions or via infected apps with malicious ads."
be careful of coinhive related services as well as minergate big red flags
Hi! I am a robot. I just upvoted you! I found similar content that readers might be interested in:
http://www.ibtimes.co.uk/hackers-hijack-millions-android-devices-secretly-mine-monero-drive-by-cryptomining-scheme-1660847