Decentralizing the Internet Protocol via Tachyon
The Internet is governed by Internet Protocols (IPs), which are a group of networks designed to make access to the Internet faster, easier, and less hassling. It is also part of the work of IPs to ensure transparency and non-breaching of the users’ data.
However, when it became obvious that the Internet Protocols (IPs) were compromising and giving way to some other security threats, it became a necessity to create a different medium for accessing the Internet. It is for that reason that we have Tachyon, which is an Internet Protocol that leverages the blockchain technology to bring about the needed change in the ways we access the Internet.
Tachyon Protocol – The Decentralized Network Stack
We need something viable to protect our Internet space. It is most imperative to make use of the relevant tools and facilities (such as the ones provided by the Tachyon Protocol) because they would help in decentralizing and redefining the ways we make use of the Internet. At this juncture, we would look at the different architectures and properties, which are used by the Tachyon Protocol for all-around protection and bolstering of Internet Protocols.
1; Reconstruction of TCP/IP Stack
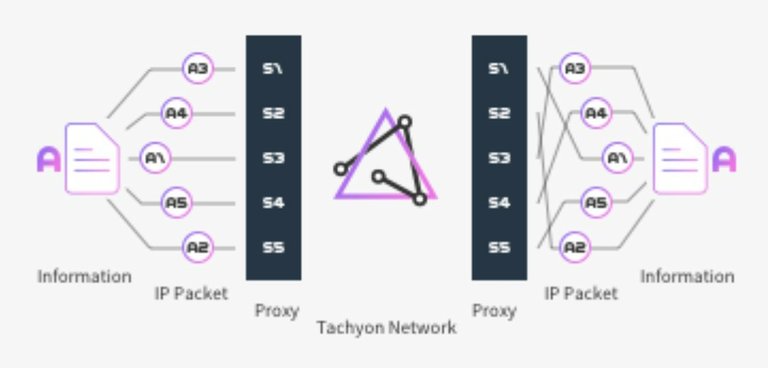
It is time to reconstruct the traditional Internet Protocols (IPs). In a situation like this, we would be making use of the Tachyon Protocol, which is a decentralized variant to the current (and centralized Internet Protocols – TCP/IP).
The reconstruction offered by the Tachyon Protocol includes creating multiple paths for routing, end-to-end encryption, and above all, the use of a decentralized structure as a way of removing controlling from centralized administrators.
2; Countering Traffic Monitoring
It is no secret that many centralized IP manipulators would be looking to find out the source of your traffic. Once that has been ascertained, the next step would be to take steps to reduce your chances of driving traffic from those mediums. It is in your powers to stop these manipulators before they wreck you. The Tachyon Protocol helps you to do that.
By delegating the Tachyon Anti-Analysis architecture, the Tachyon Protocol would be able to counter traffic monitoring. Doing so also makes it possible to block any other loopholes that create a path for third parties to intercept your entire communication network. Worthy of note is that the Tachyon Protocol’s Tachyon Anti-Analysis architecture would be able to delegate additional security strategies including Multi-Relaying and Multi-Path Routing as ways of ensuring that your entire communication networks aren’t bugged.
3; Tachyon Booster UDP
The aim here is to make use of Tachyon Booster UDP (TBU) to change the methods of the traditional and centralized transport layers. In this instance, TBU would be able to accelerate transmission times using a number of tools, such as Optimal Routing, the blockchain technology, and DHT.
Tachyon project has very strong and reputable backings
source
IPX TOKEN

Source
IPX which is very vital in Tachyon Protocol is listed on Bithumb and Bithumb Global .
Final Words
This is the perfect time to bolster the strengths of Internet Protocols (IPs), which have hitherto been susceptible to many security risks. Now that a network like the Tachyon Protocol is here, we can be confident that our Internet space would be saner and risk-free.
For more insight on this remarkable project, visit the links below
🌐 website
📖 Whitepaper
📢 Bitcointalk ANN Thread
💬 Telegram
🐦 Twitter
Writer's info
Bitcointalk Username : deodivine1
Bitcointalk Profile URL : https://bitcointalk.org/index.php?action=profile;u=1390292