WITH GOLDILOCK STORAGE IS SAFE
INTRODUCTION.

Goldilock is a new system of storing data without connection to the internet, it only makes data available when needed. It is a new innovation that removes the burden of securing wallets, passwords and private keys from individuals. It creates a safe environment around cryptocurrency and digital assets for users. It is a storage system that triggers a shift from the archaic and often inefficient way of securing data. It is also accessible and available anytime from anywhere. Goldilock combines means such as multi-factor authentication, biometrics, regressive technology triggers and cryptography. With the launching of this platform in Q2 of 2018, cryptocurrency and digital assets are protected from destructive forces and also prevent cyberattack and digital breach. With Goldilock crypto businesses security is assured.
FEATURES OF GOLDILOCK SECURITY SUITE.
- Patent-pending
- User-controlled
- Remotely activated airgap security solution for cryptocurrency key custody
- Storage of sensitive digital assets.
MORE FEATURES OF GOLDILOCK SECURITY SUITE AND THEIR SIGNIFICANCE
The Goldilock wallet: This is used by crcryptocurrency
Integrations via the Goldilock invest in crypto businesss. It is used by institution to secure information, private crypto keys and critical digital assets
Collocations: Used by institution to gain direct control over their servers
4 On-Premises Deployment option: It is for home use and for institution.
currently cryptocurrency investors and managers of sensitive digital assets depends on a narrow option to store their assets. The options available are, cold storage solution and and online hot wallets.
WHAT'S COLD STORAGE SYSTEM AND WHY IS IT UNRELIABLE TO STORE VALUABLES?
Cold storage refers to any cryptocurrency wallet that is not connected to the internet. Generally cold storage is more secure, but they don't accept as many cryptocurrencies as do many of the hot wallets. However, the cold storage system is unreliable because of the following reasons
- It can be stolen
- It can be hacked
3.It can be misplaced - It can be destroyed or even confiscated.
HOT STORAGE SYSTEM.
Hot wallet is the opposite of cold storage system, it refers to any cryptocuurency wallets that's not connected to the internet. Though hot wallets are easier to setup, access, and accept more tokens. But this is inefficient due to the following reasons.
- Vulnerability to hacking
- Denial of service
- Custodial company collapse.
The major consequence of the inadequacies of these two systems is that institutions and individual suffer financial losses due to mishandling of their keys.
Other storage options that are available are also not reliable, for example, paper and USB keys can be lost, stolen and hacked. Also solutions offered by groups like Xapo or Coinbase through cold storage encryption is also not accessible easily, access to bank vault is also limited.
All of these limitations have made iinvestment by crypto investors and sensitive digital assets manager to be at a gross disadvantage.
GOLDILOCKSOLUTION
Goldilock combines the security of offline data and accessibility convenience to proffer solutions to the problems aforementioned.
Goldilock solutions are listed below.
QUICK USERS ACCESSIBILITY OF DATA IF AND WHEN NEEDED: This prevent hackers from having access to online data
PHYSICAL SEGREGATION OF PERSONAL DATA
ACCESSIBILITY OF PRIVATE KEYS AND PERSONAL DATA
Explanation of the image below
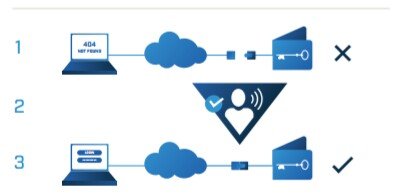
- In 1, wallet is stored through offline physical airgap mechanism and not accessible from the internet.
2 In 2, a non-IP mechanism is used, the user activates their wallet making it accessible over the internet - In 3, the user can securely access their wallet over an encrypted connection using a dedicated URL and access credentials.
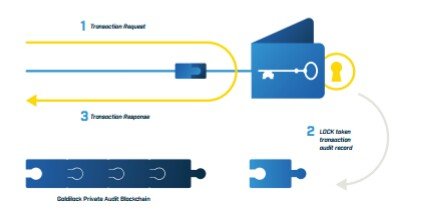
Goldilock delivers a unique ket custody and data storage solution, including
- Physical airgap disconnection from electronic networks.
2.Dedicates per-usee hardware for processing storage of encrypted data - Regressive connectivity and signal processing
- Biometric gateways
- Device recognition
- Personal generated codes
- Scalable physically-segregated connectivity solutions
- Two-Factor Authentication
- Optimal multi-signature security
10.Secured physicsl vaults - Multisite encrypted data backup
- Secure dashboards and live reporting on access and usage
- Fully-insured third-party guarantees for the extraction and delivery of data to owners on demand or in the case of business disruption ( source: white paper page 5 )
BENEFICIARIES OF GOLDILOCK SOLUTIONS.
1.CONSUMERS
- INSTITUTIONS.
Now let's talk about the solutions for each category of user
SOLUTIONS FOR CONSUMERS
Goldilock that uses code to store data is used by consumers. The encrypted data inside the storage device is in a secure, enclosed area. The user or the consumer only accesses the data when he needs it and it goes offline after the completion of any transaction he wants to execute, this is made possible because of the physical-seggregation from the internet. It protects data from wrong users and hackers. The accessibility is high because the user chooses the command to use to make the storage device online. The safety, accessibility, user-access only has made this alternative one to explore. Users can then shift from the traditional storage system to this better option.
SOLUTIONS FOR INSTITUTION.
Institutions can afford the solutions proffer by goldilock in a number of ways. They include.
- Crytptocurrency Exchanges
- Online/ hot wallet operators
- Hardware/ cold wallet operators.
CRYPTOCURRENCY EXCHANGES
Cryptocurrency exchange or digital currency exchange ( DCE) as the name implies involves the exchange of cryptocurrencies or digital currency for other assets, such as conventional fiat money for business purposes. Usually attempts to obtain cryptocurrency or digital currencies by illegal means , for instance through phishing, scamming or hacking are common and this usually lead to a collossal loss in billion of dollars worth of cryptocurrency. In order to forestall this theft cases, gridlock enables cryptocurrency exchange to only make available crytocurrency available upon demand. This eliminates unnecessary queues in transaction processing and also reduces the processing times. Client keys are protected against hackers, accessible and connected.
ONLINE/ HOT WALLET OPERATORS
Here, an on-premises development option is leveraged on. It makes use of physical devices that enable remotely operated airgap security for institution or home use.
HARDWARE/ COLD WALLET OPERATORS.
This encourages accessibility for cold storage operators
DATA STORAGE AND DIGITAL ASSET SECURITY
One of the greatest challenges the heath care domain face is healthcare data security. Healthcare data security is a strictly regulated area in US and Europe and there are strict requirements regarding who (a person or entity) is covered, what information is protected, and what must be done to ensure appropriate protection of healthcare patient information. Health data security ensures improved health care delivery for patients and health professionals.
Good financial records are essential for reporting income tax returns. ... Bankers want to see a balance sheet, income statement, and cash flow statement before they loan money to any business. Finally, accurate financial records along with production data are
important in making decisions about the farm enterprise.
Legal records also important to monitor legal proceedings.Goldilock makes all these accessible upon demand.
GOLDILOCK AS A TOOL TO MEET STANDARD DATA PROTECTION LAW.
Information Protection law or data protection law is an enactment that protects sensitive information about private individuals, it prohibit the disclosure or misuse of information about private individuals. Countries in Europe, Asia and Africa have recently enacted standard data security laws. The law imposes a fine on institutions that fails to protect consumer data. An example of such law is The European Union's General Data Protection Regulation that became operational since May 25, 2018. Also in Canada, the Personal Information Protection and Electronic Documents Act ( PIPEDA) went into effect on January 1, 2001.
The basic principles of data protection are highlighted below
- Any data collected should have a well-defined purpose
- Accuracy of records that are kept about an individual
- Information collected by an individual cannot be disclosed to other organization unless the consent of the individual is sought or permitted by law
- Unused data should be discarded
- Sensitive data ( religion and sex) should not be collected.
Due to the promulgation of all these laws to check recent and persistent hacks of cryptocurrency exchanges, key theft and lost of billions of dollars, organizations have had the cause to rely on solutions offered by Goldilock because it offers solution at a price that's not commensurate with the solution offered.
Goldilock is positioning itself to help individuals and institutions comply with standards that may later become operational.
WHY THE TOKEN?
The token used by goldilock is called "LOCK TOKEN". The lock token is an NEP-5 asset on the NEO blockchain. Potential users of goldilock would have to purchase this token to gain access. It is only the lock token that serves as a pass to the gridlock wallet, after the user might have logged on to the gridlock wallet, the wallet would instruct the NEO public bblockchain to ensure the public key address of the users own a LOCK token. This arrangement shuts out unauthorized persons from thieving cryptocurrency and other digital assets. LOCK token keeps a record of the user's node activity, codes user-owned data for the user only. LOCK is also the acceptable currency for individual users on the Goldilock Security Suite.NEO, GAS and NEP-5 would rrecieve support from gridlock token and this obviously would make NEO the most secured cyrptocurrency in use.
WHY THE NEO SMART ECONOMY
One would wonder why goldilock opt for NEO. It is quite simple and understandable.
NEO combines the digitization of assets, smart contracts and distributed network to offer the following advantageous features.
- Ensures regulatory compliance
One condition that must be met by participants of the blockchain is their ability to verify and audit digital assets before they can be given license to operate. NEO helps government and institution to carry this by confirming digital identities
- Faster processing of transaction
The use of "Delegated Byzantine Fault Tolerance" the dBFT by NEO ensures fast verification of transactions. It removes transaction ques and this is done without any cost.
INFORMATION ON TOKEN SALE.
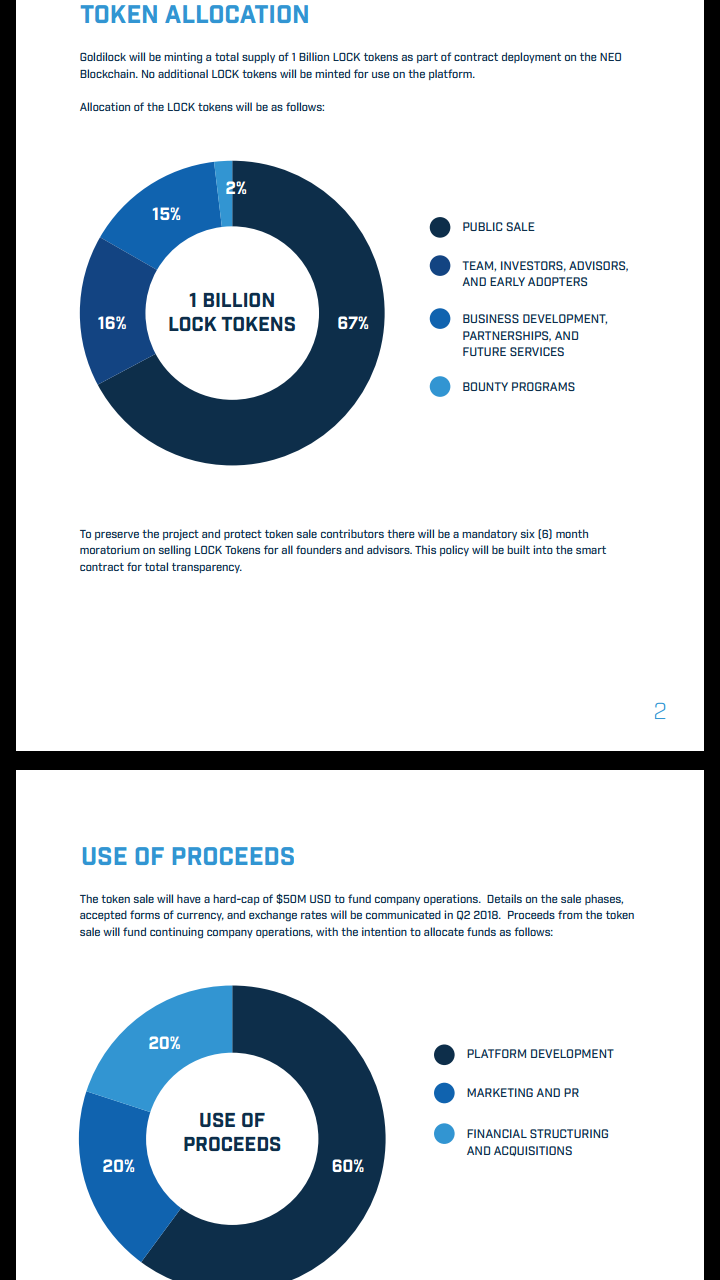
Out of the available 1 billion, Goldilock plans to sell 670 million in Q2 208. While information on further sales during the year would be made known later.

SUMMARY AND CONCLUSION
Using the three core solutions, goldilock now serves as oasis in the desert quenchig people's thirt for storage problems. It has brought more confidence to the blockchain business. Individuals, health , financial and legal institutions can depend on goldilock solutions and even government
MEET THE GOLDILOCK TEAM


For More Information & Resources:
Goldilock Website
Goldilock WhitePaper
Goldilock Tokenomics
Goldilock Telegram
Goldilock Discord
Goldilock Linkedin
Goldilock Facebook
Goldilock Twitter
Goldilock Reddit
Goldilock Github
This is my entry for the @originalworks contest. Joint contest here
Goldilock2018
This post has been submitted for the @OriginalWorks Sponsored Writing Contest!
You can also follow @contestbot to be notified of future contests!
Dear friend, you do not appear to be following @wafrica. Follow @wafrica to get a valuable upvote on your quality post!
Congratulations @timilehin10! You received a personal award!
You can view your badges on your Steem Board and compare to others on the Steem Ranking
Vote for @Steemitboard as a witness to get one more award and increased upvotes!