
To recap:
- The DAO smart contract was drained of 3.6 million ether on 17th Jun 2016 into a child DAO by an unknown attacker.
- The Ethereum community subsequently hard-forked the chain negating the attack (like it never happened) and refund of the ethers to the DAO token holders has been ongoing.
- When blockchains are hard-forked as a result of upgrades, there would be a mirror image of the unforked chain, normally left with little interest from both miners and holders. However, in this instance, the ‘unforked’ or classic chain, due to unexpected support from a minority group (20%), resulted in the demand of these ether classic (ETC) coins when it got listed on exchanges for trading. This led the emergence of an intrinsic value for these ETC, albeit at a fraction of the forked ether price (13%).
- The attacker has put actions in place to withdraw out these 3.6 million ether classic from his own DAO on the unforked chain which has a mandatory imposed “holding” period that will vest in a few hours time at exactly Mon, 05 Sep 2016 22:02:35 (UTC) after which he can deposit it into any normal account in the ether classic chain.

A more detailed update of the DAO attack can be found [here] (https://medium.com/@pullnews/understanding-the-dao-hack-for-journalists-2312dd43e993#.3jblup37h).
So what are the attacker’s options from here on?
a) Send the 3.6 million ETC to various exchanges and sell them to exit into bitcoin or other coins that provide greater anonymity?
------>This method has been tried and failed by other parties as exchanges would be monitoring all coin deposits via tracking movements from this receiving account of the attacker. At the same time, his identity will likely be exposed to the exchanges.
b) Attacker buys heaps of ETC at depressed pricing before the 3.6 million ETC vesting deadline and surprises the market by subsequently refunding the ETC back to the DAO token holders or reduce overall ETC supply via “burning” the ETC by sending it to a 0x000 address. This results in a massive price rally thereafter in which attacker would be able to profit from his earlier long trade.
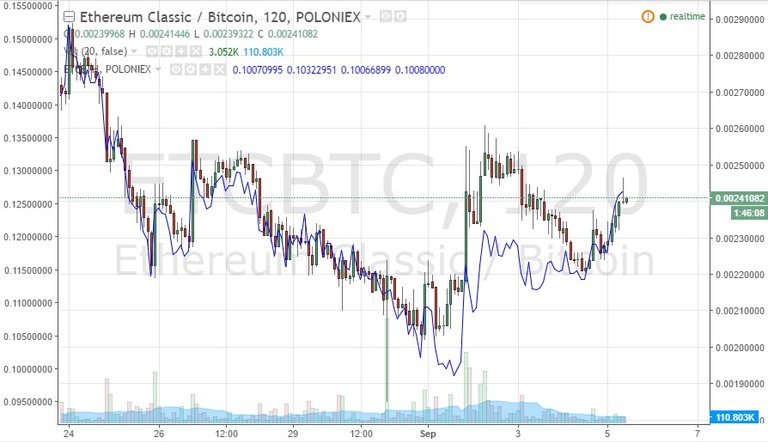
------>This method involves a large outlay of capital and/or margin to establish a sizable long position, while having to grapple with other highly volatile speculative forces and considerable position entry risk. Notwithstanding this, ETC price has indeed retraced upwards from the recent lows (20%) in the last 2 days which does signal returning demand for ETC.
c) Sell the ETC at a discount to one or a few big-pocketed Darknet buyer(s).
------>This process will require someone to take over “carrying-the-tainted-baby” on a large scale. The process will involve a lot of trust or risky escrowing among darknet participants.
d) Develop a smart contract to perform a discounted ETC swap arrangement with anyone.
------>Assuming attacker is a smart contract savvy programmer, he could develop a smart contract to swap any required amounts of ETC with anyone for a different harder-to-trace coin (e.g. Bitcoin) using bridging applications such as BTC Relay. Hence a buyer can pay the contract in BTC and obtain, say for argument sake, 200% of the BTC value in ETC to make it worth the buyer’s while.
------>But surely exchanges would be able to track these swap transactions and freeze them at each exchange receiving account? Well, what if the attacker periodically send various minuscule amount (say 0.0001 ETC) from his main ETC operating account to several exchanges’ customer accounts to taint the majority of accounts (these customer accounts are easily obtainable from the chain explorer)? It would be challenging for the exchanges to determine which incoming ETC funds originated from swap transactions with the DAO attacker and which are truly legitimate ETC.
e) Attacker will do nothing and hold the ETC for now and wait.
Conclusion:
I think option a. would be a non-starter for obvious reasons. Option b. is unlikely due to the large capital outlay and entry risk involved. However with the recent push-up in price which nobody could really explain the rationale for, I would not rule this option out totally. Option c. is unrealistic due to logistics barriers – darknet folks are currently trying to increase greater anonymity by moving towards adopting Monero as we speak.
As such, I feel the most likely attacker course of action would be either option d. or e.
Option d. allows him to launder/mix his tainted ETC to a wide pool of buyers at the lowest risk, through foregoing a large portion of his bounty without having to deal directly with the exchanges. There would be an increase in supply of ETC into the market and price would likely be depressed initially. However, distributing out this large amount to a greater diversified number of holders would most probably be viewed in positive light by the market subsequently, hence I expect a bounce in the price after the kneejerk dumping at announcement of this smart contract if it ever eventuates.
Option e. would also be likely if attacker is still finalizing his next move. Nevertheless, an attack is never over until the bounty has been monetized fully. In this scenario, it would be like a continued guillotine hanging over and depressing the ETC price constantly until this large amount resolves somehow one way or another.
Perhaps I may have missed out on other options. Pls share your thoughts and lets see how this pans out.
Technicals:
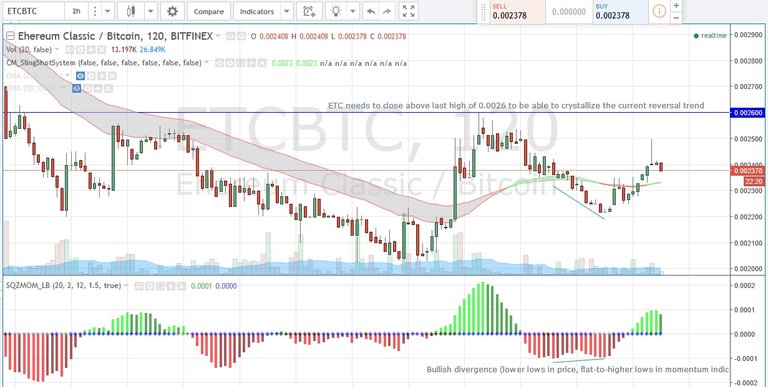
ETCBTC chart seems to have turned the corner showing a nice bounce after a positive bullish divergence was indicated during that last bottom. From here on, it needs to close above the last high of 0.0026 to nail a new peak or risk re-testing the previous precarious 0.0020 lows. If this was a setup pump trap, then this retest would be easily broken through to further new lows on a dump exit.
Welcome all comments, thoughts, and upvotes :).
wow..