I have a theory about this virus WannaCry running off the NSA tool ETERNALBLUE striking and the serious implications for Cryptocurrencies. Since Bitcoin has experienced a massive uptick in value in a short time the NSA or other alphabet agency is on the offensive trying to reign in the Bitcoin explosion. What do you think?
I'm sure many of you have noticed the dramatic falling of cryptocurrencies over the last 24-48 hours. Ever since the news about this Cry virus hit the public. Do you believe the projections of it falling to 400$ in the next few days? How far do you think it will fall? I've noticed a slight recovery in the last couple of hours but it is still down by quite a margin for the last 24 hours.
Do you think this latest CRY attack, which is affecting people in Russia (it probably wasn't the Russians) and all over the world and is demanding payment in Bitcoin, is in fact a calculated attack by the NSA trying to put a stop to the Bitcoin fever as of late? I don't think it will be successful but it does seem to me to be a concerted effort by TPTB to try to kill Bitcoin.
Personally, I think Bitcoin is here to stay and I'll ride out the storm. If the value drops I'll just buy more while it is low. What do you think?
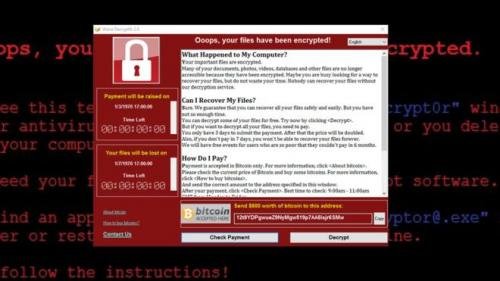
The ransomware has been identified as WannaCry
Update 4: According to experts tracking and analyzing the worm and its spread, this could be one of the worst-ever recorded attacks of its kind. The security researcher who tweets and blogs as MalwareTech told The Intercept “I’ve never seen anything like this with ransomware," and "the last worm of this degree I can remember is Conficker.” Conficker was a notorious Windows worm first spotted in 2008; it went on to infect over nine million computers in nearly 200 countries. As The Intercept details,
Today’s WannaCry attack appears to use an NSA exploit codenamed ETERNALBLUE, a software weapon that would have allowed the spy agency’s hackers to break into any of millions of Windows computers by exploiting a flaw in how certain version of Windows implemented a network protocol commonly used to share files and to print. Even though Microsoft fixed the ETERNALBLUE vulnerability in a March software update, the safety provided there relied on computer users keeping their systems current with the most recent updates. Clearly, as has always been the case, many people (including in governments) are not installing updates. Before, there would have been some solace in knowing that only enemies of the NSA would have to fear having ETERNALBLUE used against them–but from the moment the agency lost control of its own exploit last summer, there’s been no such assurance.
Today shows exactly what’s at stake when government hackers can’t keep their virtual weapons locked up.
As security researcher Matthew Hickey, who tracked the leaked NSA tools last month, put it, “I am actually surprised that a weaponized malware of this nature didn’t spread sooner.”
Update 3: Microsoft has issued a statement, confirming the status the vulnerability:
Today our engineers added detection and protection against new malicious software known as Ransom:Win32.WannaCrypt.
In March, we provided a security update which provides additional protections against this potential attack.
Those who are running our free antivirus software and have Windows updates enabled, are protected. We are working with customers to provide additional assistance.
Update 2: Security firm Kaspersky Lab has recorded more than 45,000 attacks in 74 countries in the past 10 hours. Seventy-four countries around the globe have been affected, with the number of victims still growing, according to Kaspersky Lab. According to Avast, over 57,000 attacks have been detected worldwide, the company said, adding that it "quickly escalated into a massive spreading."
It irritates me that organisations that are trying to expose irresponsible government exploits such as Wikileaks and Shadowbrokers are getting the blame for these attacks. They are the only ones trying to shore up the gaping holes in important infrastructure such as NHS patient records.
Agreed.. I think groups like the "Shadow Brokers" should be embraced.. but we also see this in the white hat hacking community as well.. If I find a vulnerability on another network and report that to the system administrator, more that likely that system admin will take some kind of lawful action against the white hat hacker, in stead of thanking that individuals for exposing holes in there network..
Yeah, I believe it is a false flag for sure. When you read about "the attack" it sounds insane. The "virus" attacked itself just before taking down the US.....Sure. If Bitcoin does go back to $400 I'll be stocking up! I would see it as an opportunity. Great article. Thank you. I'm following you.