It was believed that bitcoin possessed some form of confidentiality in the past. This is one of the factors that has attracted a lot of user who believed that they can run huge monetary transactions on the blockchain without it being traced back to their personal identity by the private and public key pairs bitcoib creates in securing individual accounts. But upon closer inspection on. the blockchain network it as been disclosed that reverse in the case as through the blockchain transaction could be traced back to the user through the transactions history and the inflow of data which can always link back to ones personal identity. Some example of the platforms include Bitcoin, Zcash,rehCash, steemt,Monero and a few others.
In fact it has also been established that storing data on the blockchain has provem to be transparent that personal confidentiality is thrown out the window. This spreads across not only on Bitcoin but it's like a wildfire across the blockchained networks.
Upon close evaluation some users do not have a problem with having their accounts or personal identify and cash flow reports being public for everyone to see but a large number of users want and yearns for anonymity due to the level and volume of assets they control.

Introducing Wimble Wimble
If you a a movie person or you have seen "Harry potter" you might have come across scenes where the term wimblewimble was used. The term wimblewimble is a adoption from the popular harry potter movie where it was a term used in casting a spell. The Term WimbleWimble was a creation of Greg Maxwell and this creation had two concepts in Mind.
1. Confidential Transaction, 2. Transaction Cut-Through.
Confidential Transaction
These transactions are Created using the cryptographic commitment schemes which is run by two main factors or should I say concepts which are hiding and Binding.
FOR EXAMPLE
Its like putting on your wifi which already is secured with a pOASSWORD only known to you. anyone who scan using his or her device and always locate your wifi network but wouldnt have access to,it until you decide to willingly give out the password to allow that user access to your wifi network.-
The binding protocol is such that itdoesn't reveal details of the transaction but verify the credibility of the details which is now up to the owner reveal the hiding key.
inputs and outputs of confidential transaction are stored in linear form as such the owner has to reveal both the binding key and the hiding key which will also require the next person receiviing the information outputs to set a new binding and hiding key only known to him in order to adequately secure the cinfidentiality of the transactions.
CUT-THROUGH TRANSACTION
due to the linear nature of the pedersom commitment (the concept on which the MimbleWimble is built ).
Due to the linearity property of Pedersen Commitments, if we have two identical transactions: from A to B, and then from B to C, we can cut through the intermediate transaction, resulting in a merged transaction from A to C, which is a valid transaction in the system. Since block is just a list of transactions, each with its list of inputs and outputs, a block can be seen as one large transaction as well, allowing us to “cut through” i.e merge all intermediate outputs both within a single block as well as across multiple blocks in the blockchain. Extending this approach to the entire chain, we get a system that only needs to store the current UTXO state, instead of entire transaction history. Validity of the history that brought us to this state can be confirmed by storing only the headers of the previous blocks which hold the proof of validity of previous states (using a structure called a Merkle tree) and Proof of Work that allows to reach consensus on which of the header chains should be considered the correct one (in case of blockchain branching).
Important of privacy in storing cryptocurrency value
Many may not have encountered the demerits of not having privacy and therefore they do not realize the risk the are running at. Some of these risks include.
Hacking
as we all know the blockchain is no man land as anyone had access to information they need. nothing is kept a secret on the blockchain this exposes users and organizations hack as the general public has access to transaction history reports and funds repow at their beck and call.
Less control
There as certain informations and data that most financial asset management organizations and personnel do not want public and some information that shouldn't be public but when they're running it through a transparent network they hav no choice of privacy.
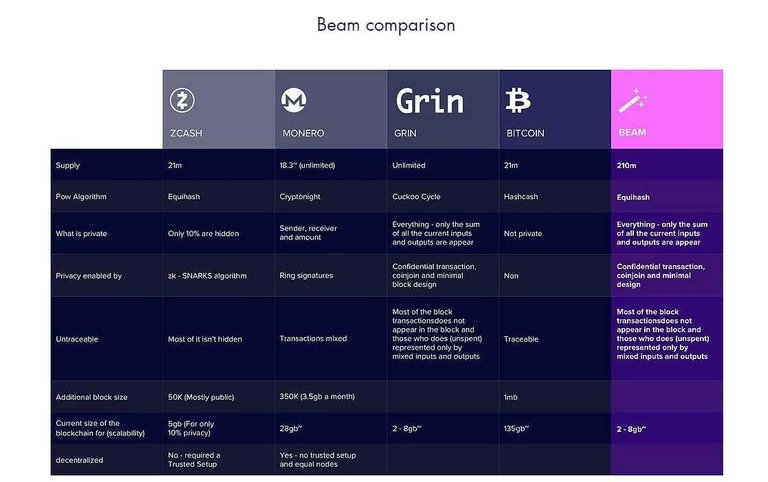
Advantages of Beam
Beam is a network that hands over information control and access management back to the user where they can have control over informations that is made available to the public. Aside the control privilege its more scalable because of its privacy protocols it only allows few transactions info per transactions now this aids for easy transaction confirmations and reduces scalability issues faced on the network. They also through the creation of a linear blockchain allow a free transfer and security of information until it reaches the expected recipient.
Use Case
Grace has over time grown her invest in the cryptoshere to a huge fortune. She has acquired for herself a lot of investment which has now put her on public eye and this has put a bulls eye on her. Since the blockchain network is transparent everyone know how and what transactions she carries out as it can always be traced back to her. In search of means of securing her investment and her personality she hears about beam from reading report on telegram, she decided to give it a try and it just was what she needed.
Use case 2
Fivo is a micro financial organization that supports and financing viable projects on the cryptosphere. They intend to do this without drawing too much attention to themselves and also keep its privacy as to how they make and manage their finance as other organizations are beginning to pry. They did a quick research and discovered Beam which offers them ultimate control over their data privacy. They are super excited.
Roadmap

Meet the team
The Engineers
The Advisors
This is my entry to the @originalworks sponsored writing contest
https://steemit.com/crypto/@originalworks/1125-steem-sponsored-writing-contest-beam
beam2018
This post has been submitted for the @OriginalWorks Sponsored Writing Contest!
You can also follow @contestbot to be notified of future contests!
Harry Potter wifi names for your wifi router.
https://www.susthesurfer.com/harry-potter-wifi-names-for-your-router/