Recently, Hacken got a “bug report” from one of our community members. The guy wanted to gain publicity with found vulnerabilities and decided to discuss the topic in our community broad enough on March 21. Having received emails with the description of vulnerabilities, Hacken is ready to provide the official statement regarding the situation.
First of all, let’s review the initial information regarding this case. A grey hacker found some sort of “vulnerabilities” on Hacken.io website and immediately disclosed the fact of their existence to the community in Telegram Group. Notably, during the first half an hour, he mentioned that he wants his bounty for undisclosed vulnerabilities, which is a clear sign of white hat hacking ethics violation.
After our dev team contacted the hacker via personal messages, he agreed to provide the list of “vulnerabilities”. According to him, there are 6 of them on hacken.io website.
After reviewing the provided screenshots and descriptions, we agree on only one point - there are certain peculiarities in some operations. 5 out of 6 “bugs” are actually the same. A guy just inserted veeeery long emails, phone numbers and other types of information in forms on our website. The only negative outcome of this peculiarity is the following - a person could write a repeater program that would submit similar requests very quickly and cause the server to go offline. Notably, this is the greatest vulnerability on our website. Also, Hacken wants to emphasize that this peculiarity is the responsibility of the third party services (TypeForm and MailChimp) and we will dig deeper into the problem to find the ways of fixing this peculiarity.
The last “vulnerability” is the most complicated one (LOL). The grey researcher found the translation issue on our website, which is obviously our fault and will be fixed ASAP. Though, you can call it neither a bug, nor vulnerability. You are welcome to check the screenshots from our dialogue.
It could have been the end of the story, and Hacken might have even paid the hacker for the lightest vulnerability (which is officially not allowed cause we don’t have Bug Bounty statement about the hacken.io website, what means that we can refuse any payment for disclosed vulnerabilities without clarifying the reason).
The situation of so-called “beg hunting” (beggar hunting) is pretty typical. One of the recognized white hats and researcher from our community, Tarek Siddiki, provided a description of a similar case of blackmailing.
However, the hacker didn’t stop on disclosing such “vulnerable” bugs on our website. In personal communication with one of our leading white hat hackers, the guy clearly stated that he wants us to pay 100 HKNs otherwise he will tear our website down. You can check the highlights of their communication in the screens below:
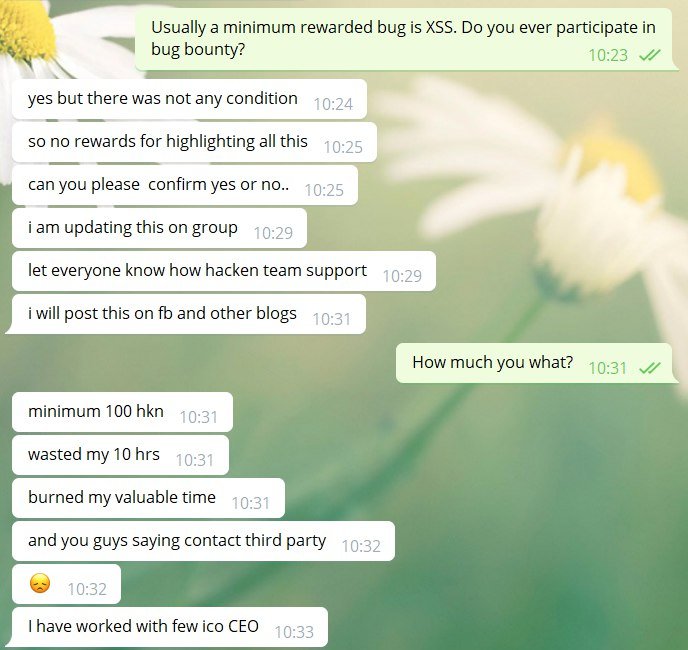
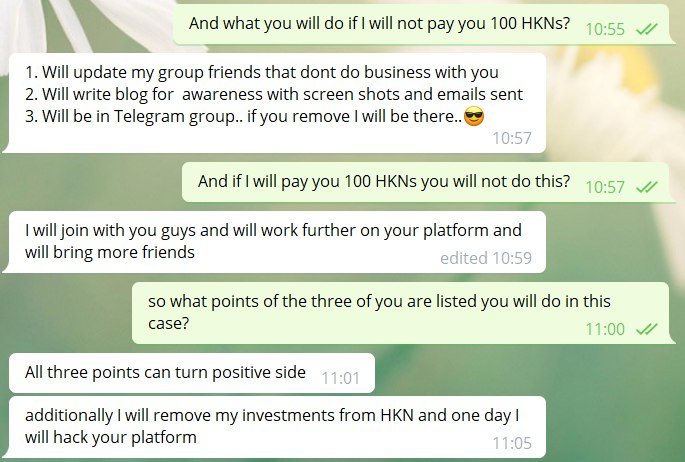
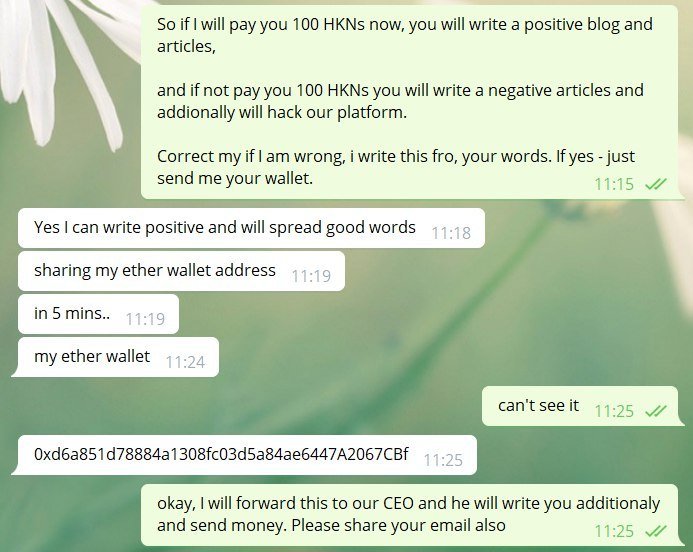
As you can see, the hacker clearly stated that the price of his silence and “spreading the good word” is at least 100 HKNs (thank you for the trust in our crypto). Otherwise, he promised to hack our platform and spread the negative news about Hacken.
We officially disregard the statements from a “white hat hacker” who blackmails us to get money. Even more, we strongly encourage him and his friends to go ahead and spread the negative news about our project and SELL all our tokens, as this gray hacker promised to do. HKN is a token for white hat hackers, so probably a guy and his friends wouldn’t need them:)
He can also win some bonus points by creating a viral campaign of negative news about Hacken Ecosystem. Our Marketing team is doing very hard to spread the awareness, and any mentions of the brand will help:)
Also, we thank for submitting some peculiarities of TypeForm processes and emphasizing some linguistic errors.
We really value the efforts of our community and constantly fix such types of issues found by you. However, it’s clearly not bug hunting :)
Follow Hacken’s (HKN) official channels:
Also, you can trade HKN here:
Kuna: HKN/BTC
Hacken Starts #HackenProof Launch Giveaway - $HKNs + Trezors + Hacken merch
![giveaway-01[1].jpg](https://images.hive.blog/768x0/https://steemitimages.com/DQmYkgadnBym3wY2sXkAmw163gsCDRWxxCbXuw7VpvkRznS/giveaway-01%5B1%5D.jpg)
1st place — 50 HKNs + Trezor + Hacken merch;
2nd — 30 HKNs + Trezor + Hacken merch;
3rd —Trezor + Hacken merch;
4h — 40 HKNs + merch;
5th — 30 HKNs + Hacken merch.
All you have to do is:
Be at least 18 years old;
Follow this link: https://wn.nr/BWQAJt
Start making entries! The more entries, the better chances to win!
The giveaway will last from March 27 until March 10.
Jeez.
Not only didn't he have any actual vulnerabilities, but he was rude and tried to blackmail you...
I hope he somehow saw this post and felt some shame.
Indeed! Well, this guy made our day somehow :D
BTW, one of our clients was also blackmailed once. Check the article
https://themerkle.com/what-to-do-when-you-are-blackmailed-by-hackers/
Thanks for the article. an interesting read :)