UK’s National Cyber Security Centre has linked recent attacks to the North Korean-affiliated hacking team Lazarus Group, according to reports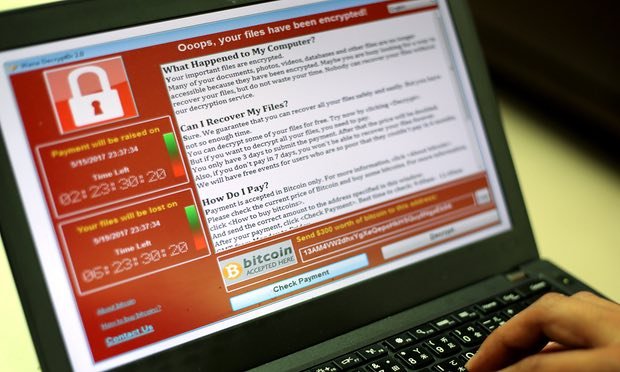
Britain’s National Cyber Security Centre (NCSC) has reportedly attributed the WannaCry malware, which affected the NHS and other organisations worldwide in May, to the North Korean-affiliated hacking team Lazarus Group.
The NCSC, which is the public face of the British defence against cyber-attacks and works closely with the UK surveillance agency GCHQ, said it would neither confirm or deny the reports. But a separate source confirmed the NCSC had led the international investigation into the WannaCry bug and completed its assessment within the last few weeks.
GCHQ’s US counterpart, the National Security Agency, has also linked the WannaCry bug to North Korea. The NCSC investigation reached the same conclusion based on its own research, the source said, adding no evidence had emerged of anyone else being involved.
Private companies have reverse-engineered the code, but the British assessment was apparently based on wider information.
Analysis of the code behind the application in early June, like that carried out by cybersecurity firm SecureWorks, suggested links to North Korea.
According to the firm, an earlier version of WannaCry, named “Wanna Decryptor v1.0”, was being distributed in a way that shared code with an earlier piece of malware called Brambul. “Brambul is uniquely associated with North Korean threat group Nickel Academy (AKA Lazarus group),” SecureWorks says. The same code overlap was also seen in another piece of malware used to attack the Polish banking regulator KNF, another operation attributed by SecureWorks to the Lazarus group.
The core of WannaCry was an exploit first discovered by the NSA, before being stolen and posted online by an anonymous entity named The Shadow Brokers. That exploit, named EternalBlue, allowed an attacker to jump between Windows computers, bypassing security constraints on the way; it is the key reason why the malware was able to spread so far and fast, and take out entire organisations in a very short space of time. Since WannaCry operated as a “worm”, spreading from computer to computer automatically, it is unlikely that its creators had any specific target in mind.
The best-known attack attributed to the Lazarus Group, a devastating hack of Sony Pictures in 2014, came as the company planned to release the film The Interview, a comedy starring Seth Rogen and James Franco as journalists embroiled in a plot to assassinate Kim Jong-Un.
But unlike other state actors, such as Russian-affiliated group APT28 AKA Fancy Bear, many of Lazarus Group’s activities are based around cybercrime, with immediate financial reward. In a pre-digital age, the country was accused of regularly forging US dollar banknotes; now, it may be building malware with the goal of collecting extortion money. WannaCry is not the first ransomware linked to the Lazarus Group and North Korea: a strike against a South Korean supermarket chain was also identified as such.
WannaCry was unusual, however, in the wildfire way that it spread. Some have speculated it may have not been deliberately released: the software contained features that are unusual for advanced ransomware, such as a hardcoded payment address, rather than a unique one for each victim, and a universal “killswitch” which, when registered, prevented the software from self-replicating.
“North Korean cyber actors are not crazy or irrational: they just have a wider operational scope than most other intelligence services. This scope comprises a broad range of criminal and terrorist activity, including illegal drug manufacturing and selling counterfeit currency production, bombings, assassination attempts, and more,” says threat intelligence company Recorded Future.
“Use of ransomware to raise funds for the state would fall under both North Korea’s asymmetric military strategy and ‘self-financing’ policy, and be within the broad operational remit of their intelligence services”, Recorded Future added.
Code overlaps are one of the key metrics by which cybercrime is attributed to various organisations and entities. If two pieces of software use the same portions of code to achieve their goals, that may imply they share a common author. But even with clues like that, attribution remains a tricky process which is as much art as science. It may be possible to identify multiple malware types as being the likely product of the same author, but linking that author back to a specific locale or command structure is extremely difficult.
Since you’re here …
Hi! I am a robot. I just upvoted you! I found similar content that readers might be interested in:
https://www.theguardian.com/technology/2017/jun/16/wannacry-ransomware-attack-linked-north-korea-lazarus-group